Tens of millions of Cisco devices found to be vulnerable to network intrusion, emergency patches distributed
Cyber security company
CDPwn: 5 Zero-Days in Cisco Discovery Protocol | Armis
https://www.armis.com/cdpwn/
Security Advisories | Cisco
https://tools.cisco.com/security/center/publicationListing.x
CDPwn vulnerabilities impact tens of millions of enterprise devices | ZDNet
https://www.zdnet.com/article/cdpwn-vulnerabilities-impact-tens-of-millions-of-enterprise-devices/

The vulnerability was discovered in a protocol called Cisco's proprietary 'CDP', which is used to search for information on Cisco devices in the network. CDP packets have an area that indicates the required power of
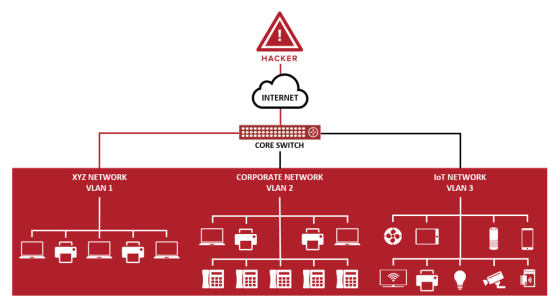
Highly functional routers and switches have a function called ' VLAN ', which virtually separates networks, and basically network devices that exist in different VLANs are treated as being connected to different networks. . Taking advantage of these characteristics of VLANs, VLANs are sometimes used to improve security, such as setting up VLANs for each department in a company. However, the vulnerabilities discovered this time will allow network attacks such as destruction of the VLAN, leading to lower security levels such as leakage of confidential information.
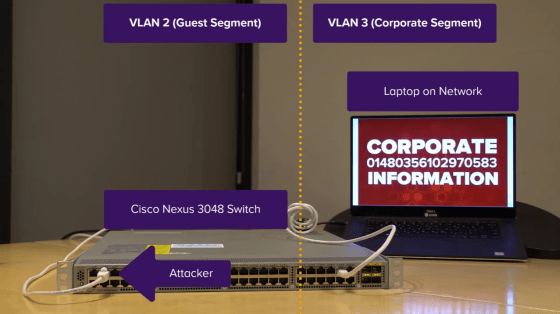
A demo video has been published that actually attacks the CDP vulnerability using the Cisco switch 'Nexus Switch 3048'.
There is a switch that separates the guest VLAN and the in-house VLAN. A hacker connects to the guest VLAN, and a notebook PC is connected to the in-house VLAN. Normally, hackers cannot access laptop information in this state.
Hackers analyzed the CDP packets sent from the switch and obtained information such as the ID of the VLAN to which they are currently connected.
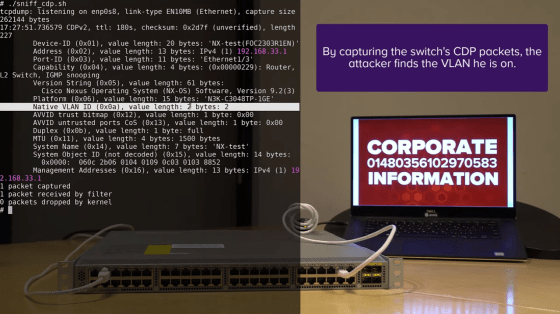
Based on the above information, the switch sends data to the switch that indicates the required power of PoE in the CDP packet, and causes a stack overflow .
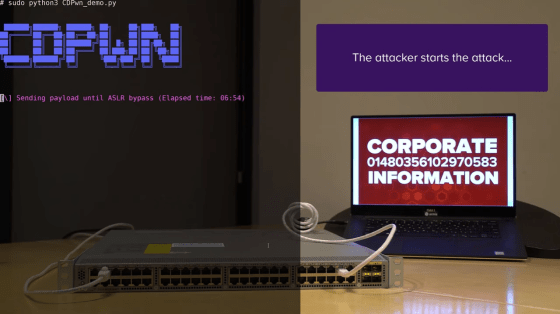
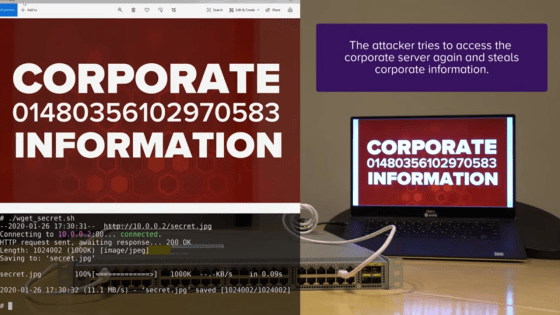
When the attack succeeded and the switch command was executed, the user name and password could be extracted and the IP address could be assigned to the VLAN.

Connected to the company VLAN, you can see the information of the notebook PC.
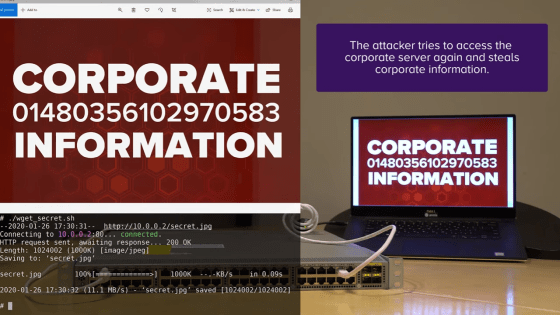
In addition, demo videos for hijacking IP phones using CDP have been released. This demo exploits a vulnerability in which IP phones treat broadcasted CDP packets as legitimate packets.
Cisco has been notified of vulnerabilities and has distributed patches to address them, all of which have a severity of 'High', the second highest of four levels.
Cisco FXOS, IOS XR, and NX-OS Software Cisco Discovery Protocol Denial of Service Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20200205-fxnxos-iosxr-cdp-dos
Cisco NX-OS Software Cisco Discovery Protocol Remote Code Execution Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20200205-nxos-cdp-rce
Cisco IOS XR Software Cisco Discovery Protocol Format String Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20200205-iosxr-cdp-rce
Cisco IP Phone Remote Code Execution and Denial of Service Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20200205-voip-phones-rce-dos
Cisco Video Surveillance 8000 Series IP Cameras Cisco Discovery Protocol Remote Code Execution and Denial of Service Vulnerability
https://tools.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-20200205-ipcameras-rce-dos
CDP is a data link layer in the OSI reference model , and is a protocol that operates only within the LAN. Since it does not flow into the WAN, it cannot be attacked from the Internet. However, Armis states that in order to avoid vulnerabilities, it is necessary to apply patches promptly or, if patching is difficult, monitor the behavior of Cisco equipment and identify suspicious behavior. You.
Related Posts:
in Security, Posted by darkhorse_log







