More than 83 million IoT devices are found to be affected, and security camera images may be stolen.

Network cameras, which allow you to check the inside of a room even from a distant place, are widespread, but there
ThroughTek Kalay P2P SDK | CISA
https://us-cert.cisa.gov/ics/advisories/icsa-21-229-01
NVD --CVE-2021-28372
https://nvd.nist.gov/vuln/detail/CVE-2021-28372
Mandiant Discloses Critical Vulnerability Affecting Millions of IoT Devices | FireEye Inc
https://www.fireeye.com/blog/threat-research/2021/08/mandiant-discloses-critical-vulnerability-affecting-iot-devices.html
The vulnerability discovered by Mandiant exists in the 'Kalay platform ' developed by ThroughTek, which develops IoT devices. According to ThroughTek, Kalay's equipment is used in more than 83 million units worldwide. These include network cameras such as baby surveillance cameras and security cameras, and Mandiant warns that exploiting the vulnerability could lead to the theft of these footage.
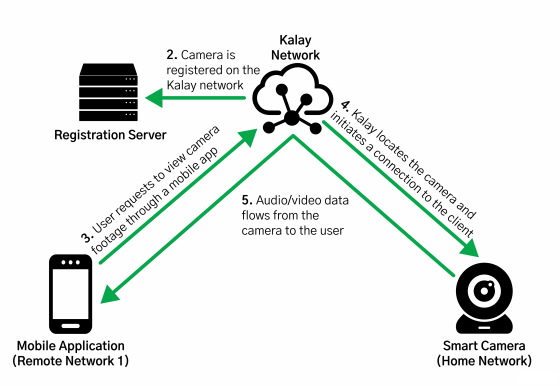
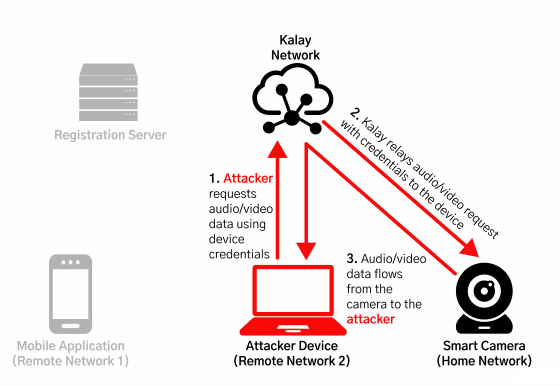
Mandiant describes the possible attacks by exploiting the vulnerability discovered this time as follows. First, when not under attack, users can inquire Kalay's server for the unique ID of their camera from a device such as a smartphone and view the video stored on the server.
However, if an attacker exploits the vulnerability, it is possible to hijack the unique ID of the attacked network camera. In this state, if a network camera user requests Kalay's server to view the video, the video data will be sent to the attacker instead of the correct user.
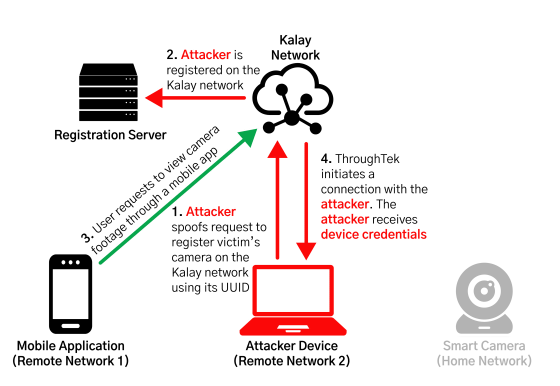
In addition, Mandiant points out that if an attacker exploits another vulnerability in Kalay's network, it will also be possible to access the attacked device directly over the network.
Mandiant has reported the vulnerability it discovered to the

Mandiant has also reported the vulnerability to ThroughTek, and ThroughTek is developing an SDK that fixes the vulnerability. Mandiant and ThroughTek are asking IoT device manufacturers using Kalay's SDK to update the SDK to a version that fixes the vulnerability.
Related Posts:
in Hardware, Web Service, Security, Posted by log1o_hf