A defect that anyone can open by hacking into a Wi-Fi compatible garage is discovered, the manufacturer does not respond for months
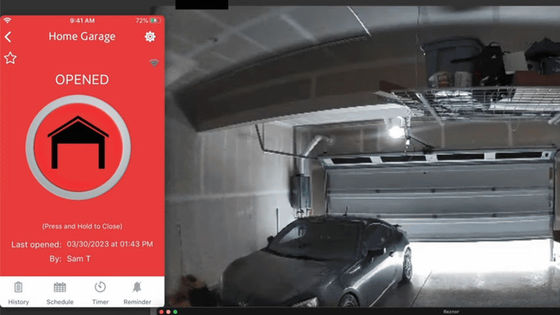
Smart devices that can access various functions anytime and anywhere via a network by connecting to the Internet are extremely convenient and highly functional, but security issues are always present as long as they are connected to the Internet. According to a 2022 survey by security researcher Sam Sabetan, a serious vulnerability was found in the ability to open and close garage doors from Wi-Fi compatible controllers and smartphones. Regardless, it became clear that the manufacturer was ignoring requests for modifications.
The Uninvited Guest: IDORs, Garage Doors, and Stolen Secrets | by Sam Sabetan | Apr, 2023 | Medium
Nexx Smart Home Device | CISA
https://www.cisa.gov/news-events/ics-advisories/icsa-23-094-01
Hackers Can Remotely Open Smart Garage Doors Across the World
https://www.vice.com/en/article/pkadqy/hackers-can-remotely-open-smart-garage-doors-across-the-world-simpaltek
There have been many reports of smart devices that can be locked and remotely controlled via the Internet, but have been hacked like PCs and smartphones. In the past, methods have been found to hack cars to remotely unlock them or honk their horns, Wi-Fi connected coffee makers could be hacked and held for ransom, smart chastity Security problems are being viewed as a problem in various devices, such as the band being hacked and unable to be unlocked, and the Ransomware Group claiming that Amazon's home security Ring was hacked . It is also pointed out that the fact that smart devices monitor users to some extent is always behind the convenience.
To what extent does a 'smart device' connected to the Internet 'monitor' the user's life and send information to the Internet?

A study conducted by Sabetan in collaboration with the U.S. Department of Homeland Security's Cybersecurity and Infrastructure Security Agency (CISA) in late 2022 found a series of significant A vulnerability has been discovered. Hackers can use this vulnerability to open and close garages, control alarms, and turn smart plugs on and off from anywhere in the world. Mr. Sabetan and CISA have contacted Nexx since around January 2023, but have not received a response. Defects continue to impact customers.'
It is estimated that more than 40,000 devices in both residential and commercial facilities will be affected by the Nexx system vulnerability. Sabetan also points out that more than 20,000 Nexx accounts are active.
Smart devices that use a protocol called MQTT (Message Queuing Telemetry Transport) usually use a unique password for each device to ensure a secure environment for operations over the Internet. However, in the case of Nexx, Sabetan explains that a common password is used for all devices, which is the cause of compromising the security of the entire system. The image below is an actual access to Nexx's MQTT server, and we were able to see all MQTT messages, including important customer privacy.
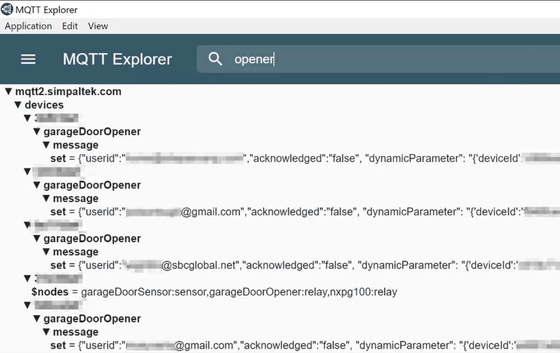
In the movie below, you can see a demonstration experiment of how to hack the smart garage. As an example of the procedure Sabetan showed, first open and close the smart garage as usual with the official Nexx app, and capture the data sent to the Nexx server with a hacking tool. At this time, it seems that due to the vulnerability of the system, it is possible to receive not only its own application information but also messages from other 558 devices, including email addresses and user names. After that, by playing the command captured via another software instead of the application, we have successfully opened and closed the smart garage without going through the dedicated application.
NexxHome Smart Garage Vulnerability-CVE-2023-1748-YouTube
In addition, Nexx's smart garage has a 'timer function' and a 'scheduling function' that 'automatically opens the garage at a specific time every day or at a pre-scheduled time'. It seems that it is becoming more susceptible to IDOR attacks that exploit vulnerabilities that allow general users to perform operations that are permitted only by authority. Because IDOR vulnerabilities occur when an application exposes references to internal objects such as files or database keys without proper authorization checks, Nexx's poor security features allow a small change in a parameter to create another You can now operate the device's schedules and timers.
CISA recommends that users should contact Nexx support directly, disconnect all devices from the internet, firewall the control system, and close any network, such as a business, that contains sensitive information. It is recommended to take measures such as separating the device from
Related Posts: