The topic is that smart padlock that can be unlocked in 0.8 seconds will break security in 0.8 seconds

A fingerprint authentication smart padlock that can be unlocked in 0.8 seconds developed by Canadian startup company Tapplock has vulnerability that can be unlocked in 0.8 seconds exactly the same as unlocking with a normal scheme if it is used That is to say.
Totally Pwning the Tapplock Smart Lock (the API way)
https://medium.com/@evstykas/totally-pwning-the-tapplock-smart-lock-the-api-way-c8d89915f025
The "world's worst" smart padlock - it's EVEN WORSE than we thought - Naked Security
https://nakedsecurity.sophos.com/2018/06/18/the-worlds-worst-smart-padlock-its-even-worse-than-we-thought/
There are two vulnerabilities pointed out in the Smart padlock made by Tapplock of 99 dollars (about 11,000 yen). One is that it can be unlocked in 30 seconds by using a tool such as a Phillips screwdriver, which is a physical design defect.
And the second one is to be able to calculate the code necessary for unlocking from the Bluetooth network address of the smart padlock, and if you create the application it was possible to unlock it in about 2 seconds. However, since the network address of Bluetooth is ready for everyone, there is a problem that anyone can unlock if you know the formula to derive the unlock code. As for this problem, too much security consideration is lacking, so I have troubled many security researchers why I made such errors.

In addition to these design defects, the vulnerability pointed out by Mr. Stykus this time uses Tapplock's web service, and as a preliminary preparation it has to have at least one Tapplock account and the target account If it knows ID, it is executable. With Tapplock's web service, if access control is not done other than login / logout, if you know only the target ID, you can browse the information of that ID and you can access the information necessary for unlocking .
Also, even if you do not know the account, since the unencrypted HTTP is used when communication between the client and Tapplock's web service is in the initial state, simply by checking the packet information flowing in the network, It is possible to check account ID easily. Also, since the account name of Tapplock is set from the location information, it is possible to easily guess packet information without eavesdropping. The following image is a JSON file that is sent to Tapplock's web service from the smart padlock client application, indicating that the position information of the smart padlock etc. are not encrypted and are transmitted in clear text.
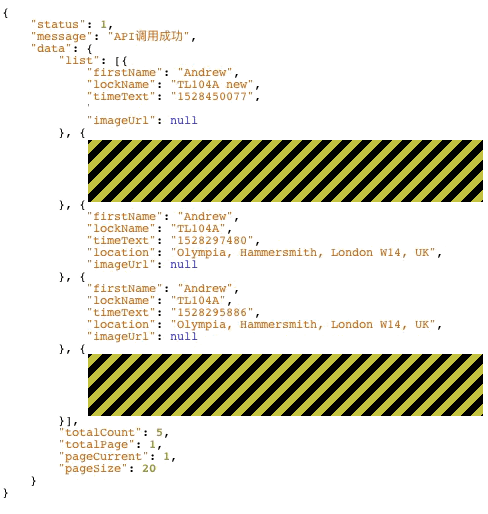
There was also a report that the time taken until unlocking was 0.8 seconds when the attack method using the vulnerability pointed out by Mr. Stykas was implemented as a program and it actually takes a fingerprint authentication of the smart padlock to unlock it It is clear that it is equivalent to time.
Tapplock provides a patch for dealing with this attack, applying all patches will not set an easy-to-guess ID, communication will be encrypted HTTPS modified to connect It is supposed to be able to do. For this reason, Tapplock explains that users of smart padlocks should apply the update immediately.
Related Posts:







