Smart rosary application that can be prayed at any time turned out to be easy to hack

The vulnerabilities were immediately discovered in the
ClickToPray eRosary Account Takeover-Fidus
https://fidusinfosec.com/clicktopray-erosary-account-takeover/
Deus ex hackina: It took just 10 minutes to find data-divulging demons corrupting Pope's Click to Pray eRosary app • The Register
https://www.theregister.co.uk/2019/10/18/vatican_erosary_insecure/
On October 18, 2019, the Roman Pope governing the Catholic Church announced the eRosary, a smart rosary that can be crossed and prayed at any time. The selling price is $ 110 (about 12,000 yen), and it is also sold on Amazon in Italy .

There is a vulnerability in “
Security company Fidus InfoSecurity said on the official Twitter account, “We have successfully developed a complete account takeover
Less than 5 minutes into looking at the eRosary application our research team has developed a full account takeover exploit.Can obtain e-mails, phone numbers, height, weight and other personal data.This has been reported. Luckily it's so new it's not in the wild yet.pic.twitter.com/XpqYqDpgC2
— Fidus InfoSecurity (@FidusInfoSec) October 17, 2019
When posting the above tweet, Fidus InfoSecurity did not reveal the details of the vulnerability in Click To Pray, but the next day Twitter was updated again, “After the security report of the other day, eRosary “The team behind our dedicated app has issued a fix so we can disclose more information.” In addition, some publicly available information regarding vulnerabilities is disclosed on the official website.
After our security report yesterday, the team behind the eRosary application have already issued a fix and we can disclose more: https://t.co/mrYuPJFNeO
— Fidus InfoSecurity (@FidusInfoSec) October 18, 2019
When using the Click To Pray app, you can choose between creating your account by entering your email address or creating an account in conjunction with your Google / Facebook account.
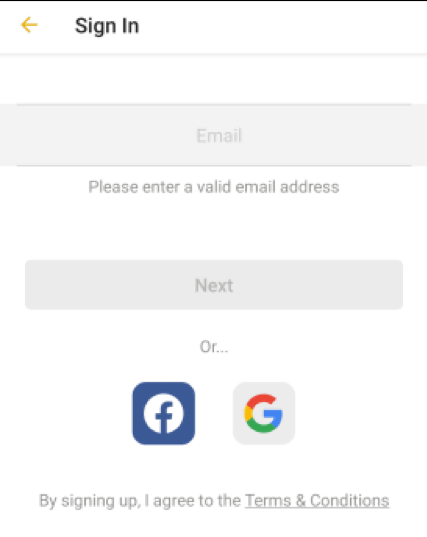
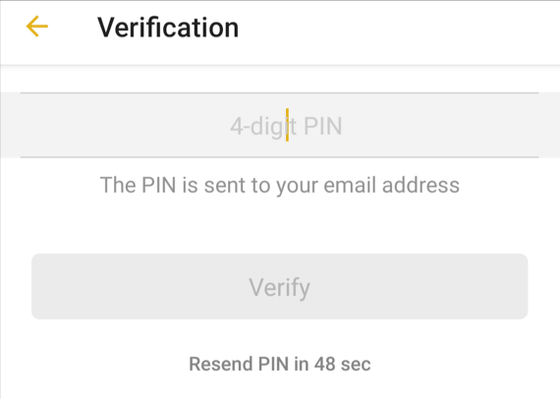
If you enter your email address, we will protect your account with a 4-digit PIN code instead of setting a password. If the account is protected with a PIN code and the user account is reset, an email will be sent to the registered email address.
The API of the application communicates with the back-end system, but it has become clear that the terminal used by the user, e-mail address information, regional information, etc. were sent via the API due to the vulnerability The information sent by the API was not encrypted and could be easily read.
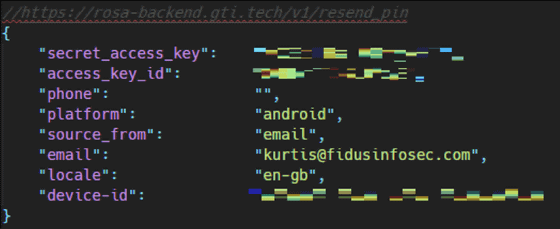
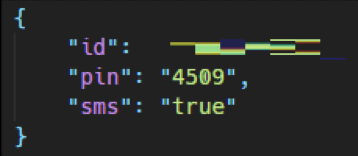
The API's 4-digit PIN code is also clearly specified.
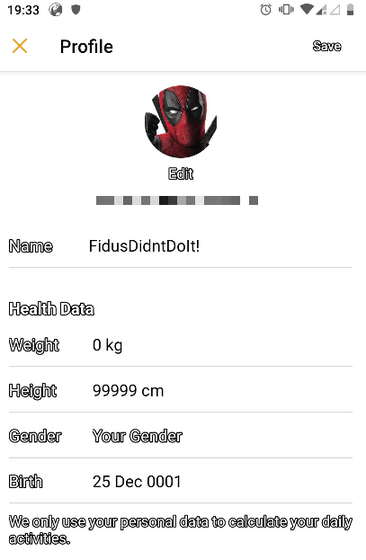
If you log in to the application using this PIN code, you can know information such as height, weight, gender, date of birth, etc. from the profile screen of the user account.
Fidus InfoSecurity says, “Applications that use a 4-digit PIN code are interesting. There is no API rate limit, so it ’s relatively easy to access an account without the vulnerabilities we found. '
In addition, when IT Register news register The Register created a dummy account, it was reported that the Fidus InfoSecurity research team succeeded in hijacking the account easily. The account does not record personal financial information of the user, but personal information that may be leaked due to hacking is `` possible to cause damage to the user if released in a country like China '' The Register is written.
Fidus InfoSecurity reported that the problem had been fixed within 36 hours after reporting the vulnerability, said Fidus InfoSecurity founder Andrew Mabbitt, “It fixes the Click To Pray API issue and the method is very 'It was complicated.' Furthermore, as a result of correcting the vulnerability, “It is no longer possible to extract the 4-digit PIN code from the API call. However, since the PIN code is 4-digit, the vulnerability to the brute force attack remains the same. It ’s not a problem. ”
According to the Roman Pope, the security researcher Elliot Alderson first discovered the Click To Pray vulnerability and reported the problem, and his research report on the PDF file was published on the Internet. It is open to the public.
Related Posts: