A vulnerability "BlueBorne" that can take over a smartphone via Bluetooth without being noticed by the other party?

A security vulnerability has been found in Bluetooth installed in many smart phones, PCs, and even IoT devices. There are 8 problems discovered by the security company "Armis" together, and they are collectively referred to as "BlueBorne"It is named. By hitting this problem, it is possible for a hacker to take over the operation of the terminal without being noticed at all by the attacked side.
BlueBorne Information from the Research Team - Armis Labs
https://www.armis.com/blueborne/
BlueBorne: Critical Bluetooth Attack Puts Billions of Devices at Risk of Hacking
http://thehackernews.com/2017/09/blueborne-bluetooth-hacking.html
BlueBorne is a coined word that combines "Airborne" meaning "Bluetooth" to pass through the air, and as its name suggests, BlueBorne makes hacking possible using Bluetooth's near field communication function, and in the worst case ToMan-in-man attackIt is a security hole that will be even stepped on the stepping stone. What kind of hijacking is actually possible is shown in the following movie created by Armis Labs.
Armis - BlueBorne Explained - YouTube
BlueBorne is a vulnerability that most of terminals equipped with Bluetooth can be targets. In this movie, demonstration is done using Google's Android smartphone "Pixel".

On the left side of the screen is the PC screen operated by the hacker, and on the right side the state of the side receiving the attack is displayed.
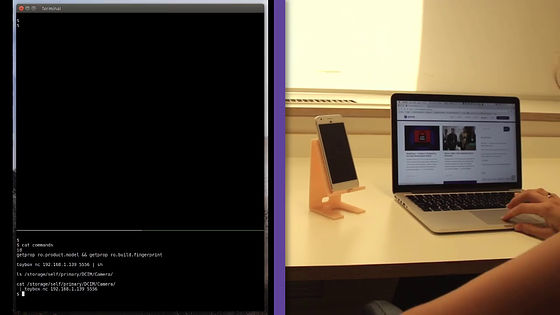
Hackers start attacking. Commands are input to the screen.
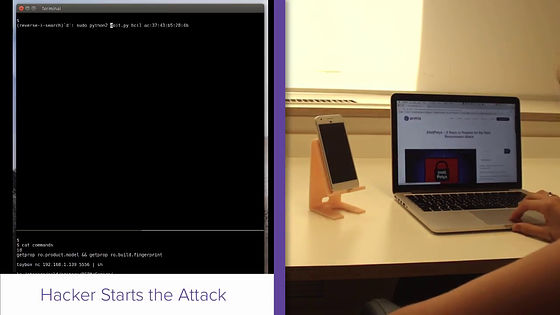
It seems that we succeeded in hijacking the terminal in a few seconds.

There is no change in the smartphone of the attacked side, and I have not noticed that it was totally taken over at this stage.

Next, the hacker wakes up the locked terminal.

The screen of the smartphone on the right screen turned on. The hacker uses the mouse here and operates so as to touch the terminal with the finger.

Hover over the camera icon and click ......

What a camera started up. Then, click on the camera switching icon ......

The image has been switched to the front camera.

In addition, the side who received the attack truly becomes aware of this situation, but this is only the state of the demonstration. In fact, it can be used in situations that are less noticeable, or it will be possible to launch applications other than cameras.
You can even launch the camera and even shoot.

And the screen is on the home screen of the terminal. It looks like nothing happens, but behind it the hacker is crawling the images stored on the device.

And I succeeded in pulling out the picture I shot the previous time from the terminal. By questioning the vulnerability of Bluetooth, this series of operations is executed without being noticed.

Conditions for enabling this attack include "that the target device's Bluetooth is on" and "exist within Bluetooth communication possible range", and "updated to corrected firmware What you do not have ". In other words, if the firmware is updated to the latest state, there is a high possibility that the security hole is obstructed, but in the case of the third party equipment whose support system is not sufficient, the risk becomes high.
It is noteworthy that it is a serious aspect of this vulnerability that it does not require pairing necessary for much of Bluetooth communication. It is a problem that a hacker has a weak point that it is hard for the attacking side to notice the takeoff because the hacker can take over the stranger's terminal without pre-pairing setting. Also, Armis Labs points out that it is possible to attack in situations without physical connection and furthermore it can expand attacks in a chain-like fashion.

After discovering this problem Armis Labs has provided information to companies and organizations such as Google, Apple, Microsoft, Samsung, and Linux Foundation, and each company has already taken measures. The problems pointed out are the following 8, of which 4 are including serious security concerns.
· Information Leak Vulnerability in Android (CVE-2017-0785)
· Remote Code Execution Vulnerability (CVE-2017-0781) in Android's Bluetooth Network Encapsulation Protocol (BNEP) service
· Remote Code Execution Vulnerability (CVE-2017-0782) in Android BNEP's Personal Area Networking (PAN) profile
· The Bluetooth Pineapple in Android-Logical flaw (CVE-2017-0783)
· Linux kernel Remote Code Execution vulnerability (CVE-2017-1000251)
· Linux Bluetooth stack (BlueZ) information leak vulnerability (CVE-2017-1000250)
· The Bluetooth Pineapple in Windows-Logical flaw (CVE-2017-8628)
· Apple Low Energy Audio Protocol Remote Code Execution vulnerability (CVE Pending)
In the case of smartphones, iOS 9.3.5 and earlier versions and OSs older than Android 6.x Marshmallow are subject to the problem. For iOS, the update rate to the latest OS is high, but Android tends to be delayed to shift to the latest OS, and when this problem is found, there are 1.1 billion target terminals worldwide And that. In addition, there are many IoT terminals with Bluetooth communication function, and Tizen OS, BlueZ, and Linux Kernel 3.3-rc1 and earlier versions of the Linux platform have problems.
For Android users, the application released by Armis Labs "BlueBorne Vulnerability Scanner"Google PlayIt is also possible to check from the appropriate model by installing from. If your terminal is applicable, it is better to turn off the Bluetooth function immediately.
Related Posts: