Vulnerability 'BLESA' that innumerable Bluetooth devices such as smartphones and PCs are hijacked is discovered

It is reported that a vulnerability has been found in Bluetooth-equipped devices such as smartphones and PCs that can cause malfunctions by receiving unauthorized data. It is estimated that billions of devices worldwide are affected by this vulnerability, named ' BLESA '.
BLESA: Spoofing Attacks against Reconnections in Bluetooth Low Energy | USENIX
Bluetooth Spoofing Bug Affects Billions of IoT Devices | Threatpost
https://threatpost.com/bluetooth-spoofing-bug-iot-devices/159291/
Billions of devices vulnerable to new'BLESA' Bluetooth security flaw | ZDNet
https://www.zdnet.com/article/billions-of-devices-vulnerable-to-new-blesa-bluetooth-security-flaw/
A research team led by Jianliang Wu, a security researcher at Purdue University in the United States, will be able to malfunction devices via Bluetooth at the security conference ' WOOT '20 ' held on August 11, 2020. Reported that a vulnerability was found. The vulnerability in question is called 'BLESA' because it causes a spoofing attack via Bluetooth Low Energy (BLE) technology, which enables Bluetooth communication at extremely low power.
According to the research team, BLESA is included in the BLE specification, 'Authentication when reconnecting devices outside the range of Bluetooth with Bluetooth is not mandatory but optional' and 'Authentication of communication data' If it fails, authentication may be bypassed ', which is caused by two specifications.
The research team points out that a wide range of devices will be affected by BLESA by exploiting the often overlooked reconnection process rather than the pairing process, which is being actively studied as a Bluetooth security issue.
You can see what happens when the attack with BLESA is actually done by watching the demo movie below.
blesa demo --Youtube
Below is the Oura Ring, a ring-shaped health tracker paired with Google's smartphone Pixel XL via Bluetooth.
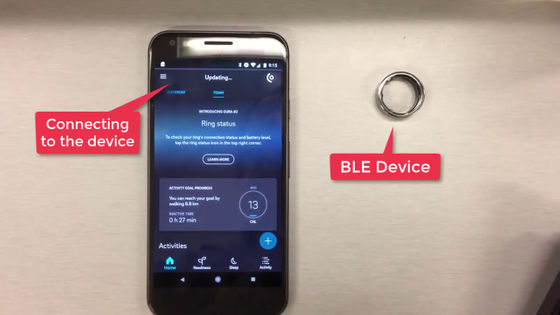
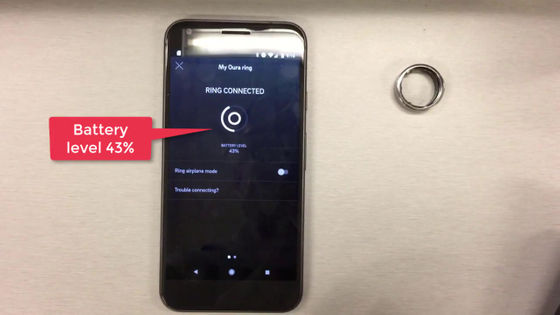
Before the attack with BLESA, when I looked at the battery level of the device with the Oura Ring app, it was '43%'.
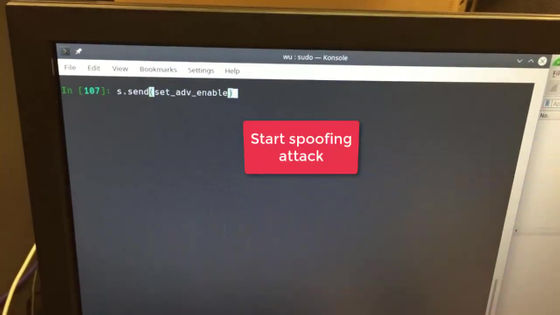
Quit the app and launch a spoofing attack.
When I launched the app again, it reconnected via Bluetooth.
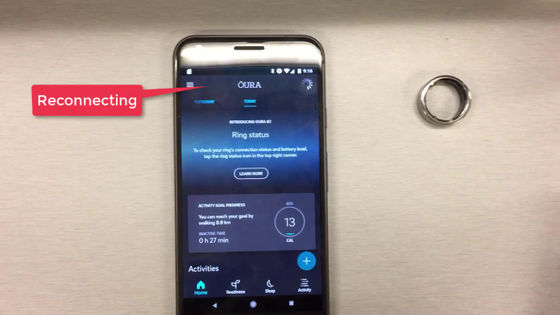
The result of sending spoofing data due to a spoofing attack ...
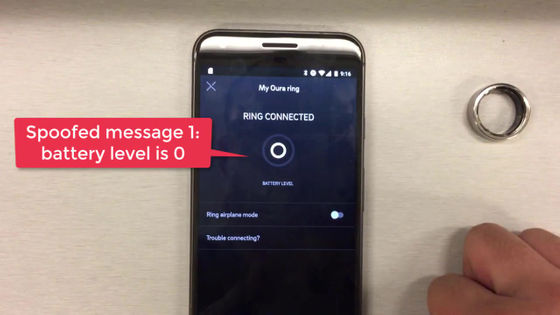
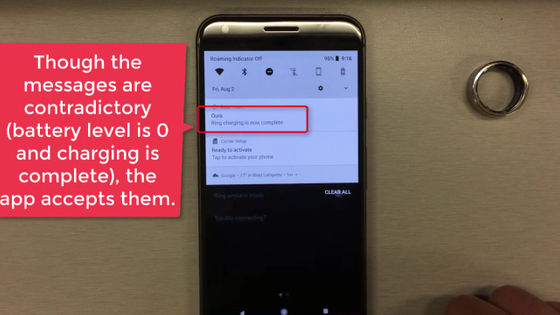
The battery level, which should have been 43%, has changed to '0%'.
Even though the battery is supposed to be 0%, there is also a notification that the spoofing attack has completed charging.
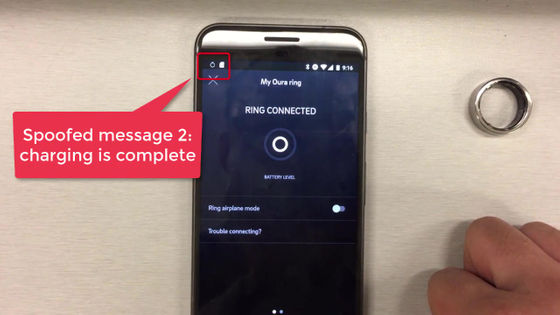
It's a contradiction to say 'full charge with 0% battery', but the app accepts this situation. This is a BLESA spoofing attack.
The research team confirmed that BLESA is effective for
Already, the research team has reported the discovery of BLESA to the BlueZ development teams at Apple, Google and Linux, and Apple fixed this issue in June. The BlueZ development team also announced that it will remove some code that exposes the device to BLESA attacks and implement proper BLE reconnection procedures. However, as shown in the movie above, at least as of June 2020, Pixel XL with Android 10 installed did not support BLESA.
In addition, from BLE usage statistics, the research team points out that 'there are billions of IoT devices using BLE software stacks that do not support BLESA.'
'Devices that do not support BLESA are currently in the hands of software suppliers and are waiting for a patch to fix the issue,' said news site ZDNet, which reported the issue.
In addition, the news site Threatpost, which handles security information, said, 'In September 2020,' BLURtooth ', which allows an attacker to overwrite the authentication key of a Bluetooth device, was discovered, and BLESSA is the second serious Bluetooth bug this month. That's it. '
Related Posts:
in Software, Smartphone, Security, Posted by log1l_ks