A cyber attack similar to "Rowhammer attack" that can take authority by continuous access to storage such as SSD is possible

ByGilly Berlin
IBM researchers will not reveal the cyber attack methods that can take administrative privileges by continuous access to the system storage.
From random block corruption to privilege escalation: A filesystem attack vector for rowhammer-like attacks - woot17-paper-kurmus.pdf
(PDF file)https://www.usenix.org/system/files/conference/woot17/woot17-paper-kurmus.pdf
IBM researchers: Rowhammer-like attack on flash memory can provide root privileges to attacker - Myce.com
http://www.myce.com/news/ibm-researchers-rowhammer-like-attack-ssds-can-provide-root-privileges-attacker-82386/
IBM researchers are holding security workshops in Vancouver, Canada "WOOT '17We announced an attack method of rewriting blocks and taking authority by repeating continuous access to storage.
In 2015, "Rowhammer Attack" was used to exploit the physical property that interference between cells occurs with the miniaturization of DRAM memory, rewriting the contents of the cell and taking over the system.
What kind of attacks the Rowhammer attack is, the metaphor in "# 1: RAM" of Kaspersky Official Blog below is easy to understand and excel.
5 Threats Approaching Hardware - Kaspersky Official Blog
https://blog.kaspersky.co.jp/hardware-malware/7249/
To ensure security, some RAMs can not be changed except specific programs and OS processes. Briefly, important processes can be placed in tightly protected buildings, but unreliable programs only have to beat the entrance doors.
However, when stepping on the footed butterfoot in front of this door (that is, keep changing the contents of the memory cell quickly and continuously), it turned out that the lock of the door was broken. Surprisingly, recent locks are becoming unreliable ...
It is a Rowhammer attack that has been demonstrated in DRAM so far, but IBM researchers discover that similar attacks can occur in NAND type memory storage SSDs as well. The following movies show how to take power from ext3 file system of Linux installed on SSD of MLC NAND,
[Demo] From random block corruption to privilege escalation - YouTube
About this attack, media such as Myce.com reported as "Attack aiming at SSD", but IBM researchers say "I want to correct the contents" on Hacker News bulletin board.
Author here, I would like to set the record straight. We do not claim to have a ... | Hacker News
https://news.ycombinator.com/item?id=15031874
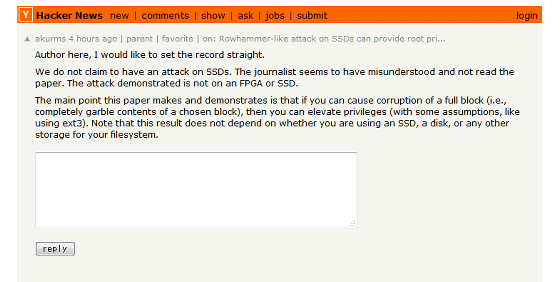
According to the writing, "This paper is not about any attacks targeting SSD, journalists are misunderstanding, it seems that they are not reading papers. The essence of this paper is that if all It means that if you can damage the block, you will be able to deprive the privilege.The result is not dependent on the type of storage such as SSD, HDD, etc. where the file system runs, "and more general attack on system storage It seems to be a method.
Related Posts: