Hundreds of Acer, Dell, GIGABYTE, Intel, and Supermicro devices have had their UEFI Secure Boot platform keys leaked, putting them at risk of system compromise
A research team from security company Binarly reported a vulnerability called 'PKfail' that allows arbitrary code execution at boot time on more than 200 devices sold by Acer, Dell, GIGABYTE, Intel, and Supermicro. The cause of the vulnerability is said to be the leak of the platform key that is the basis of secure boot in 2022.
PKfail: Untrusted Platform Keys Undermine Secure Boot on UEFI Ecosystem
SupplyChainAttacks/PKfail/ImpactedDevices.md at main · binarly-io/SupplyChainAttacks · GitHub
https://github.com/binarly-io/SupplyChainAttacks/blob/main/PKfail/ImpactedDevices.md
UEFI is a system that controls computer hardware and starts the OS. UEFI has enhanced security functions and accelerated the boot process from BIOS, and is particularly characterized by its 'Secure Boot' function. Secure Boot uses digital signatures to authenticate boot loaders, drivers, and OS to prevent unauthorized software and malware from infiltrating the system boot process, and prevents the execution of unsigned code.
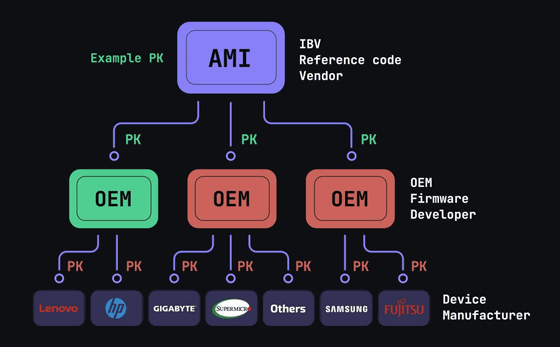
The root of trust in Secure Boot is the 'Platform Key,' which acts as a cryptographic key to establish a trust relationship between hardware devices and the firmware that runs on them.
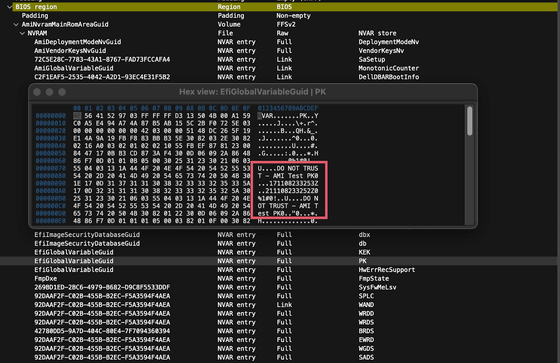
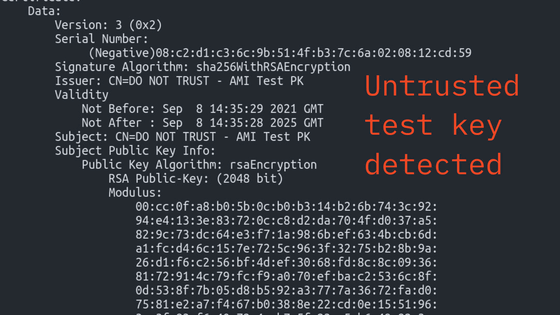
In December 2022, while investigating a separate matter, Binarly researchers discovered that engineers working for multiple device manufacturers had published the private key portion of the platform key in a public repository on GitHub. The leaked private key was stored in an encrypted state, but was only protected by a four-character password.
The Binarly research team claims that the problem is that test platform keys generated by a BIOS vendor called
The Binarly research team points out that an attacker can completely bypass secure boot on an affected device and execute arbitrary code during the boot process. Below is a proof-of-concept movie of PKfail released by the Binarly research team.
Proof of Concept for PKfail - YouTube
According to Binarly's research, 215 models of devices are using this leaked key. In addition, more than 10% of UEFI firmware images from the past 10 years in the Binarly dataset were found to be affected by PKfail.
By exploiting PKfail, an attacker could execute untrusted code during the boot process, even with Secure Boot enabled, compromising the entire security chain from firmware to the operating system.
Binarly has made available a freely available scanning tool to mitigate this threat, enabling the entire security community to detect vulnerable devices, system firmware updates, and malicious payloads.
Binary PKfail detector
https://pk.fail/
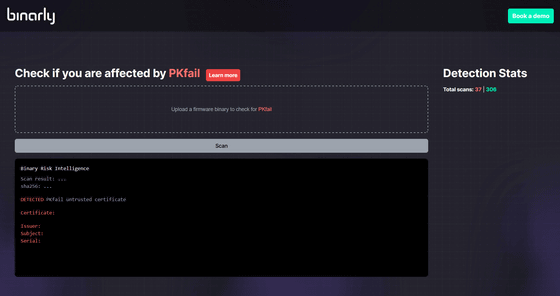
Binarly also encourages device vendors to generate and manage proper platform keys and replace test keys, and advises users to pay attention to firmware updates from device vendors and apply security patches that address the PKfail vulnerability.
Related Posts: