Intel 12th generation Core 'Alder Lake' compatible BIOS related source code leaked, Intel admits it is genuine
A file that is considered to be the source code related to BIOS compatible with Intel's 12th generation Core series CPU known by the codename 'Alder Lake' leaked to 4chan, an overseas bulletin board site, and was uploaded to GitHub. The file was a ZIP file of about 2.8GB and contained a large amount of files and tools for building a BIOS, UEFI to be exact, for the AlderLake platform and chipset. Intel has confirmed that this leaked source code is genuine.
Intel's Alder Lake BIOS Source Code Reportedly Leaked Online | Tom's Hardware
https://www.tomshardware.com/news/intels-alder-lake-bios-source-code-reportedly-leaked-online
Intel Confirms Alder Lake BIOS Source Code Leak | Tom's Hardware
https://www.tomshardware.com/news/intel-confirms-6gb-alder-lake-bios-source-code-leak-new-details-emerge
What can we learn from leaked Insyde's BIOS for Intel Alder Lake
https://hardenedvault.net/blog/2022-10-08-alderlake_fw-leak/
The Alder Lake series was released on November 4, 2021, and the leaked files were compressed into a 2.8GB ZIP format. Under the hood, it was a tool made by BIOS vendor Insyde Software to make things easier for OEMs, such as UEFI provisioning and fine-tuning.
The source code to the Intel Alder Lake has been leaked online.
— vx-underground (@vxunderground) October 8, 2022
* Alder Lake CPUs was released November 4, 2021
* Source code is 2.8GB (compressed)
* Leak (allegedly) from 4chan
* We have not reviewed the entirety of the code base, it is massive
In addition, it has been confirmed that the file size after decompression was 5.86 GB and was uploaded to GitHub. The GitHub repository has already been deleted at the time of article creation, but it can be viewed on the Internet Archive etc.
wow, is that Intel Alder Lake BIOS source code?
— freak (@glowingfreak) October 8, 2022
unbelievable, 4chan hackers are back at it. https://t.co/F899yPYwdY
Intel commented to Tom's Hardware, a hardware-related news site that reported this issue, ``It seems that our proprietary UEFI code has been leaked by a third party,'' and the leaked file is genuine. I acknowledged that
It is unknown at the time of writing the article how the leaked file leaked this time, but it is known that one of the documents was described as 'Lenovo Feature Tag Test Information', and the Git log A description that appears to be the name of an employee of LCFC Electronics Technology, a Chinese ODM manufacturer, has also been found. Since LCFC Electronics Technology is a subsidiary of Lenovo, it is believed that it was probably leaked due to hacking damage somewhere in the adjustment / development process of UEFI for Lonovo PCs.
Interesting git log #OSINT https://t.co/05xDkqMqnD pic.twitter.com/uqYVIFF3wc
—SttyK (@SttyK) October 8, 2022
A PC's UEFI initializes the hardware before the OS loads, in which it establishes connections to security systems such as the Trusted Platform Module (TPM) . If the source code of this UEFI were leaked, it would be very likely that potential backdoors and security vulnerabilities would be exposed by malicious attackers or security researchers, Tom's Hardware said. said.
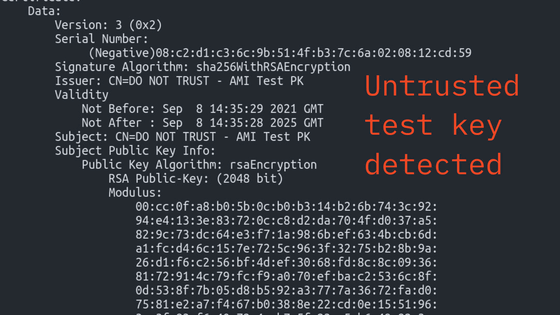
In fact, security researcher Mark Amorov has already analyzed the Model Specific Register (MSR) , which is usually reserved for privileged code, `` Intel Boot Guard '' that checks for UEFI tampering before booting. Found with the private signing key used for It reports that this Intel Boot Guard may be disabled.
I can't believe: NDA-ed MSRs, for the newest CPU, what a good day... pic.twitter.com/bNitVJlkkL
— Mark Ermolov (@_markel___) October 8, 2022
In addition, it is said that there was also a part related to Authenticated Code Modules (ACM) for Trusted Execution Technology (TXT) , which is one of Intel's security functions, and some people said that the reliability of security will be large in the future. The possibility of fluctuation has also been pointed out.
A very bad thing happened: now, the Intel Boot Guard on the vendor's platforms can no longer be trusted... ☹️ pic.twitter.com/K5mXcp5ipW
— Mark Ermolov (@_markel___) October 8, 2022
Intel said, ``We do not rely on information obfuscation as a security measure, so we do not believe this will expose new security vulnerabilities.This code is eligible for the Project Circuit Breaker bug bounty program. and researchers who discover potential vulnerabilities are encouraged to raise their awareness through this program, and we keep both our customers and the security research community informed about this situation. We are working to provide it, ”he said, noting that the reliability of security will not be shaken immediately.
Related Posts: