Signed certificate data leaked from NVIDIA and multiple malware spoofing NVIDIA drivers appeared

NVIDIA announced on March 1, 2022 that confidential information was stolen by a hacker group attack, and was requested to pay the ransom in virtual currency and remove mining performance restrictions by taking the stolen data as a hostage. It is
Malware now using NVIDIA's stolen code signing certificates
https://www.bleepingcomputer.com/news/security/malware-now-using-nvidias-stolen-code-signing-certificates/
'We are aware that threat actors have acquired employee credentials and some NVIDIA sensitive information and have begun to leak online,' NVIDIA said on March 1, 2022. Announced the damage of the attack. This attack is by the hacker group 'LAPSUS $' which is active mainly in South America, and LAPSUS $ is 'product circuit diagram' 'driver' 'firmware' 'document' 'internal tool' 'software development kit (SDK)' ' Claimed to have stolen a total of 1TB of data, including 'all information about the Falcon microcontroller built into the NVIDIA GPU.' We are requesting NVIDIA to 'pay for ransom in virtual currency', 'open source GPU drivers for Windows, macOS, and Linux', and 'eliminate the mining performance limiting function' Lite Hash Rate (LHR) ''.
NVIDIA admits that confidential information has been stolen by hacking groups, threatening to 'remove GPU mining restrictions'-GIGAZINE

And on March 4, 2022, security researcher
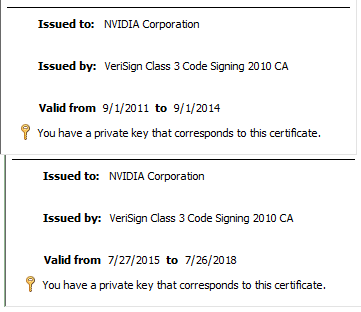
Both of the above code signing certificates have expired, but Windows will allow the driver to be installed even if the code signing certificate has expired. Therefore, if an attacker grants the leaked code signing certificate to the malware, Windows will recognize the malware as an NVIDIA driver and install it.
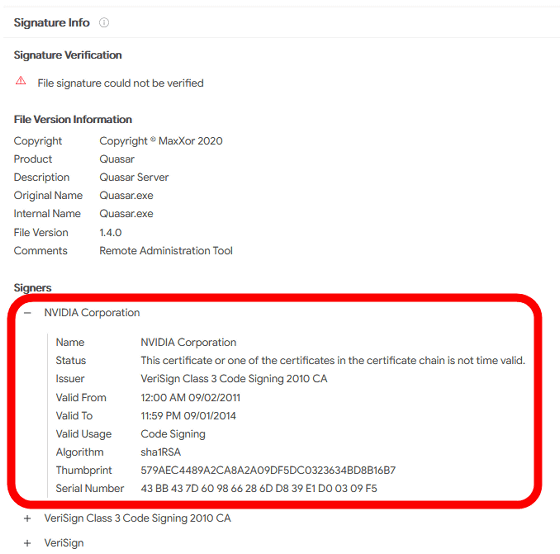
Multiple attacks using leaked code signing certificates have already been reported. For example, the following malware details page registered with VirusTotal, a virus checking service, lists NVIDIA as the signer.
David Weston , vice president of security and enterprise at Microsoft, used Windows Defender Application Control (WDAC) to block arbitrary drivers or to block specific versions of NVIDIA to prevent malware attacks impersonating NVIDIA. We recommend measures such as allowing the certificate of.
WDAC policies work on both 10-11 with no hardware requirements down to the home SKU despite some FUD misinformation i have seen so it should be your first choice. Create a policy with the Wizard and then add a deny rule or allow specific versions of Nvidia if you need
— David Weston (DWIZZZLE) (@dwizzzleMSFT) March 3, 2022
However, security-related media Bleeping Computer has pointed out that setting up WDAC is difficult for the average Windows user, and wants the leaked code signing certificate to be added to the Windows revocation list. On the other hand, if the code signing certificate is added to the revocation list, the real driver developed by NVIDIA will also be blocked, so I'm guessing that it will take time to solve the problem.
Related Posts:
in Security, Posted by log1o_hf






