Approximately 3.6 million MySQL servers using port number 3306 have been released and turned out to be potential attack targets

According to a survey by security company Shadowserver, there are about 3.6 million MySQL servers accessible on port number 3306 / TCP, which may be the target of cyber attacks.
Over 3.6 million exposed MySQL servers on IPv4 and IPv6 | The Shadowserver Foundation
According to the Shadowserver report released on May 31, 2022, about 3.6 million MySQL servers using the default port number of 3306 / TCP are open to the public on the Internet, with TLS and non-TLS connections. He said he responded regardless.

For investigation, Shadowserver performs a scan by issuing a MySQL connection request on port 3306 / TCP and collecting the server's response in response to a greeting message. This included responses for both TLS and non-TLS connections. No intrusive checks were done to find the level of access to the database.
As a result of the investigation, the total number of MySQL servers connecting with 3306 / TCP using IPv4 is 3,957,457, and the total number of MySQL servers connecting with 3306 / TCP using IPv6 is 1,421,010, of which 227 with IPv4. It is said that 9,908 units and 1,343,993 units of IPv6 returned greeting messages.
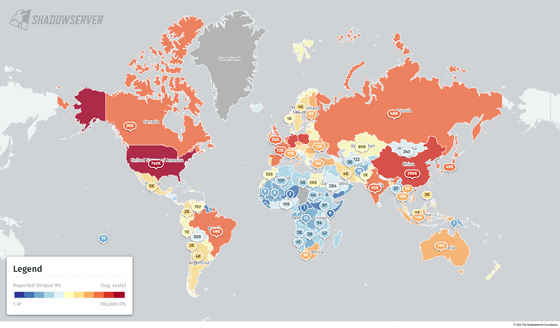
The country with the largest number of publicly available IPv4 / MySQL servers is the United States, which has about 740,000 units. In addition, about 296,000 China, about 207,000 Poland, and about 175,000 Germany follow. 49,000 units have been confirmed in Japan.
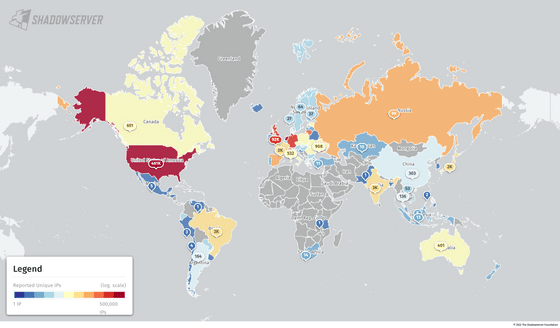
The country with the largest number of publicly available IPv6 / MySQL servers is also the United States, and about 461,000 have been confirmed. This is followed by about 296,000 Netherlands, about 218,000 Singapore, and about 174,000 Germany. 2000 units have been confirmed in Japan.
The top 10 affected IPv4 versions are:
| version | number |
| 5.7.33-36 | 150,600 units |
| 5.6.41-84.1 | 92,834 units |
| 5.7.23-23 | 69,627 units |
| 5.7.38-0ubuntu0.18.04.1 | 59,333 units |
| 5.6.51-cll-lve | 58,825 units |
| 8.0.23 | 57,148 units |
| 5.5.68-mariadb | 55,401 units |
| 5.6.50-log | 54,574 units |
| 5.5.5-10.1.48-mariadb | 40,853 units |
| 5.7.33-log | 35,809 units |
The top 10 affected IPv6 versions are:
| version | number |
| 5.5.5-10.5.12-mariadb-cll-lve | 908,128 units |
| 5.7.37-40-log | 147,072 units |
| 5.5.5-10.5.13-mariadb-cll-lve | 125,320 units |
| 5.5.5-10.5.15-mariadb-cll-lve | 72,856 units |
| 8.0.27-18 | 20,838 units |
| 5.5.5-10.3.32-mariadb-log | 11,121 units |
| 5.7.35-38 | 6640 units |
| 5.5.5-10.5.15-mariadb-cll-lve-log | 3435 units |
| 5.7.23-cll-lve | 2085 units |
| 5.7.33-cll-lve | 1993 units |
Shadowserver advises that 'the MySQL server rarely needs to allow external connections from the Internet.' When I received a report about my network or environment, I told him to filter the traffic to my MySQL instance and deploy authentication on the server to deal with it.
Related Posts:
in Web Service, Security, Posted by log1p_kr