U.S. Cyber Command warns that 'patches for critical Atlassian Confluence vulnerabilities should be applied now'

On Saturday, September 3, 2021, the Cyber National Operations Force (CNMF) belonging to the
Mass exploitation of Atlassian Confluence CVE-2021-26084 is ongoing and expected to accelerate. Please patch immediately if you haven't already— this cannot wait until after the weekend.
— USCYBERCOM Cybersecurity Alert (@CNMF_CyberAlert) September 3, 2021
Atlassian Releases Security Updates for Confluence Server and Data Center | CISA
https://us-cert.cisa.gov/ncas/current-activity/2021/09/03/atlassian-releases-security-updates-confluence-server-and-data
US govt warns orgs to patch massively exploited Confluence bug
https://www.bleepingcomputer.com/news/security/us-govt-warns-orgs-to-patch-massively-exploited-confluence-bug/
CVE-2021-26084: Confluenza --Censys
https://censys.io/blog/cve-2021-26084-confluenza/?hss_channel=tw-3566263693
Confluence is a web-based team workspace designed for employees to collaborate on various projects within a company, provided by the Australian company Atlassian.
CNMF points out the vulnerability 'CVE-2021-26084' that Atlassian published a security advisory in late August 2021. The vulnerability is an OGNL (Object Graph Navigation Library) injection that allows an unauthenticated attacker to execute arbitrary code on a Confluence server or an instance of a data center.
According to Bleeping Computer, an IT news site, evidence of intrusion from Brazil, China, Hong Kong, Nepal, Romania, Russia, and the United States has already been found on the server ...
Started Observing Live We Exploitation Of The New Confluence Vulnerability (CVE-2021-26084). Pic.Twitter.Com/VP6YrJTKC7
— Ba1gan (@Balgan) September 1, 2021
Multiple abuse cases of CVE-2021-26084 have been reported, such as the deployment of PowerShell and Linux shell scripts, and the installation of virtual currency mining programs on the Confluence server without permission.
2021-26084 Exploit-CVE Activity Also Detected From 2.57.33.43 (????????) As Of 2021-09-02T06: 46:. 57Z Pic.Twitter.Com/kbl9zEXgNA
— Bad Packets (@bad_packets) September 2, 2021
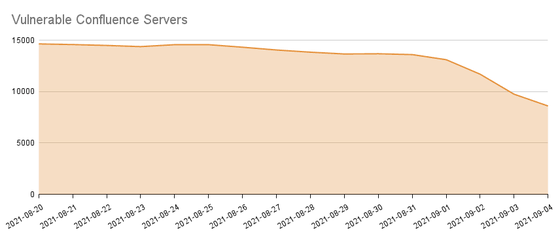
Atlassian released a security update on August 25, 2021, including a patch for CVE-2021-26084. However, Censys, the developer of IoT-specific search engines, said in an official blog, 'Of the 14,701 services that Censys identified as Confluence servers, 13,596 ports and 12,876 individual IPv4 hosts. Has not applied the fix patch, 'reported August 31, 2021.
Since then, as news about the Confluence vulnerability has spread, more servers have been patched, and as of September 5, 2021, the number of vulnerable Confluence instances has dropped to 8597, Censys reports.
The US Cyber Command is calling for an urgent application of a patch distributed by Atlassian.
???????? #ActionRequired patch immediately! ???????? https://t.co/b6eAYdFuW4
— US Cyber Command (@US_CYBERCOM) September 3, 2021
The Cybersecurity and Infrastructure Security Agency (CISA), the US Department of Homeland Security's cybersecurity jurisdiction, also said, 'A remote attacker exploits this vulnerability and puts the affected system under control. It's possible, 'he said, calling on Confluence users and administrators to review the security advisory and apply the required updates immediately.
Related Posts:
in Security, Posted by log1i_yk







