NSA and FBI issue official warning that 'Russian government hackers are attacking government and private institutions around the world'

The National Security Agency (NSA) of the United States, the Cyber Security and Infrastructure Security Agency (CISA), the Federal Bureau of Investigation (FBI) and the National Cyber Security Center (NCSC) of the United Kingdom jointly work with the General Information Agency (GRU) of the Armed Forces of the Russian Federation. ) Hackers have warned that they continue to launch
Russian GRU Conducting Global Brute Force Campaign to Compromise Enterprise and Cloud Environments
(PDF file) https://media.defense.gov/2021/Jul/01/2002753896/-1/-1/1/CSA_GRU_GLOBAL_BRUTE_FORCE_CAMPAIGN_UOO158036-21.PDF
NSA, Partners Release Cybersecurity Advisory on Brute Force Global Cyber Campaign> National Security Agency Central Security Service> Press Room
https://www.nsa.gov/news-features/press-room/Article/2677750/nsa-partners-release-cybersecurity-advisory-on-brute-force-global-cyber-campaign/
NSA: Russian GRU hackers use Kubernetes to run brute force attacks
https://www.bleepingcomputer.com/news/security/nsa-russian-gru-hackers-use-kubernetes-to-run-brute-force-attacks/
FBI, NSA: Russian military cyber-unit behind large-scale brute-force attacks --The Record by Recorded Future
https://therecord.media/fbi-nsa-russian-military-cyber-unit-behind-large-scale-brute-force-attacks/
Jointly by NSA and other government agencies, at least from mid-2019, Unit 26165, which belongs to GRU's 85th Main Special Service Center (GTsSS), will continue to use Kubernetes clusters to launch brute force attacks on organizations around the world. I warned that there was. Kubernetes cluster refers to a set of node machines for running Kubernetes , an open source container orchestration system that deploys, scales, and manages containerized applications, and Unit 26165 refers to Cactus VPN from this Kubernetes cluster. -It is believed that the Brute Force attack continues after obfuscating through various VPN services such as IPVanish, NordVPN, ProtonVPN, Surfshark, and WorldVPN.
The specific procedure for a cyber attack by GRU is to first perform a blue force attack to identify valid credentials from a Kubernetes cluster, and then use the obtained certificate to execute a remote code execution vulnerability in Exchange Server ( CVE-2020-). 0688 and CVE-2020-17144 ) entering the government agencies and companies of the network took advantage of known vulnerabilities such as. It then deploys the reGeorg Web shell , which creates a Socks proxy within the intranet to persist the intrusion state, obtains other credentials, and uses the obtained credentials to access the internal email server.
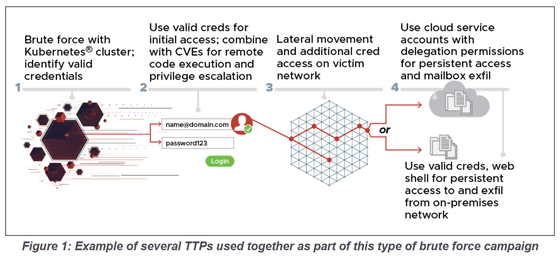
In addition, from November 2020 to March 2021, the 26165th unit carried out a brute force attack without utilizing the VPN service, and at that time, from the following IP address, the US government, military organization, politics Attacks have been identified against consultants and political parties, defense industry contractors, energy companies, logistics companies, think tanks, higher education institutions, law firms, media companies and more.
・ 158.58.173 [.] 40
・ 185.114.63 [.] 47
・ 185.233.185 [.] 21
・ 188.214.30 [.] 76
・ 195.154.250 [.] 89
・ 93.115.28 [.] 161
・ 95.141.36 [.] 180
・ 77.83.247 [.] 81
・ 192.145.125 [.] 42
・ 193.29.187 [.] 60
According to the NSA and others, the GTsSS cyber attack force is also known as 'APT28,' 'Fancy Bear,' and 'Strontium.' The NSA warned in August 2020 that fancy bear malware tools threatened national security.
FBI / NSA warns that Russian government hacker group 'Fancy Bear' is threatening national security with undiscovered Linux malware tool 'Drovorub' --GIGAZINE

Related Posts:
in Security, Posted by darkhorse_log







