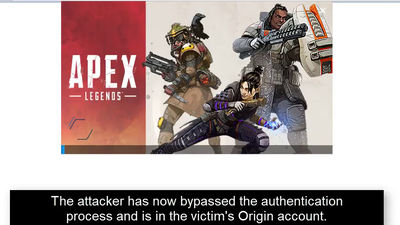
A vulnerability could be found that a hacker could steal a 'Fort Knight' account
A security researcher reports that there is a vulnerability that makes it easy for user accounts to be stolen at " Fort Knight " where 80 million users worldwide play battle royal games with building elements.
Fortnite's Vulnerability: Only the Secure Survive | Check Point Software Blog
https://blog.checkpoint.com/2019/01/16/fortnite-vulnerability-where-only-the-secure-survive/
Fortnite Flaws Allowed Hackers to Takeover Gamers' Accounts
https://thehackernews.com/2019/01/fortnite-account-hacked.html
Researchers working at Check Point , a software development company, point out that there are multiple security vulnerabilities in Fort Knight. One vulnerability allows an attacker to hijack Fort Knight's player account remotely by simply letting the user click on the link.
Researchers point out the vulnerability of Fort Knight to SQL injection and cross site scripting , as well as a bug that bypasses the firewall of web applications, plus the " OAuth authentication takeover bug".
Fort Knight is a popular game with more than 80 million users worldwide, and there are cases that Fort Knight's accounts are sold for more than $ 50,000 (about 5 million yen) in online auctions such as eBay . Therefore, takeover of account is "a nightmare," The Hacker News points out.
Fort Knight's special account uses single sign-on (SSO) such as Facebook, Google, Xbox, PlayStation, so players can easily create and log in to your account.
According to researchers, by combining cross-site scripting flaws and redirect issues on subdomains of Epic Games, the developer of Fort Knight, the attacker says, "By simply clicking a specially crafted link, the user account It has succeeded in creating a mechanism to steal authentication tokens ". Once the link is clicked to steal the authentication token, the attacker can access the player's personal information, purchase in-game currency, or sell the account itself.
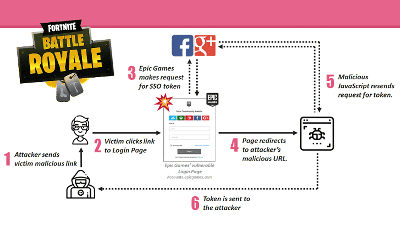
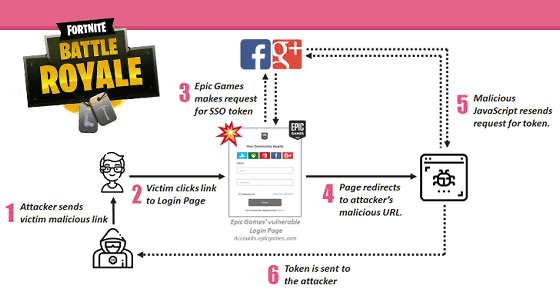
The flow of account takeovers is briefly described as follows.
1: Attacker sends malicious link to Fort Knight user
2: User clicks the link to access Fort Knight's login form
3: Login form requires SSO token against third-party SNS by attacker's workmanship
4: Redirected from login form to malicious URL charged by attacker
5: Malicious JavaScript again requests SSO token
6: Authentication token is sent to the attacker, allowing account takeovers
According to Check Point researchers, it seems that some users already suffered from account hijacking. In addition, it is pointed out that the possibility that the attacker may even access the contents of the voice chat that the victim went with other players during the game, and that the privacy of the account owner may be infringed seriously. In addition, by exploiting SQL injection which is one of the vulnerabilities, there is a possibility that the attacker may specify "the version of MySQL database used by Epic Games", too.
Check Point also publishes a movie that summarizes the vulnerability of Fort Knight.
Fortnite Login Vulnerability - YouTube
Besides, researchers have successfully executed a cross site scripting attack on the user login process, bypassing the firewall of the web application used in Fort Knight. The multiple vulnerabilities discovered by Check Point have already been reported to Epic Games as of mid December 2018.
Check Point and Epic Games encourage Fort Knight users to not accidentally click on links provided on user forums or other sites, The Hacker News recommends that you enable 2-step verification I will write ".
Related Posts: