Vulnerability in which playback history and private movies are leaked from YouTube's 'embedded player'
YouTube has the ability to output HTML tags that allow you to embed a player playing a YouTube movie on another website. The embedded player is a convenient existence that allows you to access playlists as well as play and stop movies. However, the discoverer,
bugs.xdavidhu.me --xdavidhu's bug bounty writeups.
https://bugs.xdavidhu.me/google/2021/01/18/the-embedded-youtube-player-told-me-what-you-were-watching-and-more/
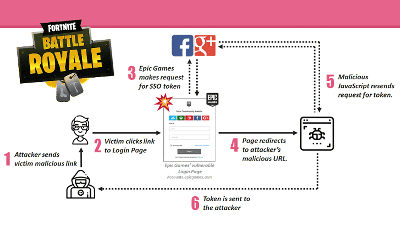
Your YouTube account has a 'Playback' list, a 'See Later' list, a 'Favorites' list, and an 'Upload' list, but Schütz said the URLs for these lists were 'guessable'. I found that. For example, in the upload list that includes the uploaded movie, the first three characters of the channel ID part of the URL 'https://www.youtube.com/channel/channel ID' that displays the channel are 'UUB' or 'UUD'. It was possible to access by changing to.
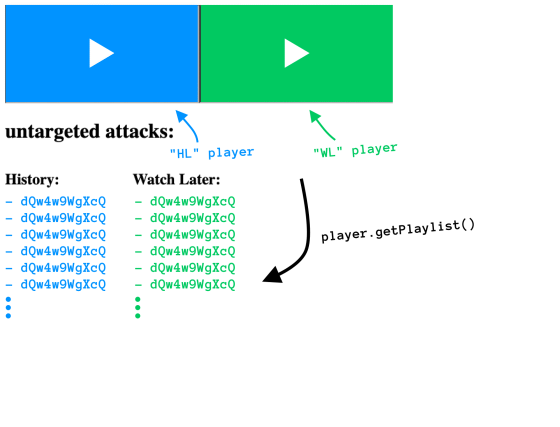
If you weren't logged in to your account, you could only access 'published' movies for your upload list, so if you could only guess the URL of the list, there was no possibility of a private movie leak. However, Schütz also found that YouTube's 'embedded player' could create a logged-in state for the account of the person who played the player.
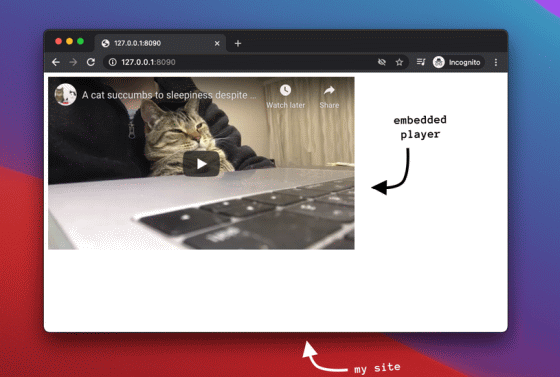
YouTube movies can be installed as embedded players in the website, and the installed players can be controlled by JavaScript using the
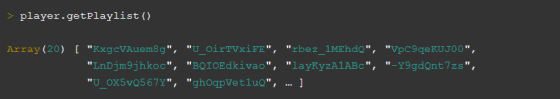
When Schütz was working on a YouTube hack, the YouTube Player API had a getVideoData method that could get information about the movies in the playlist. The VideoData object that can be obtained with the getVideoData method contained information such as the movie ID, creator, and title. In addition, if the person who played the player was logged in to YouTube, the embedded player would also be logged in, giving the embedded player full access to the account.
For this reason, if you set up a YouTube embedded player on your website and combine the YouTube Player API method with the guessed URL, you could access private movies.
This vulnerability was discovered in October 2019 and has been fixed at the time of writing the article. Schütz received $ 1337 from Google as a reward for the vulnerability, but 'I think now that the impact of the vulnerability was small,' he said at the time. Looking back on the amount of the reward, he said, 'The more you understand the system, the more ideas you can think of how to break it.'
Related Posts:
in Software, Web Service, Security, Posted by darkhorse_log