A hacking device "PoisonTap" of only 600 yen which makes backdoor just by inserting it in locked PC in just one minute appeared
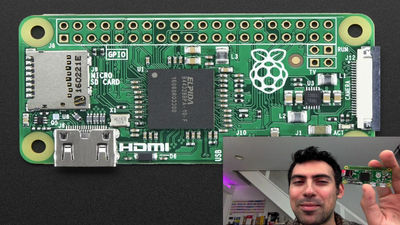
Sammy Camuka, famous for hacker world, got his own softwareRaspberry Pi ZeroHacking device just put on "PoisonTapWe developed and used the actual use on YouTube. PoisonTap is a terrible device that installs the backdoor in just one minute, even if it is locked with a password by simply connecting to the PC of the attacking target.
Samy Kamkar: PoisonTap - exploiting locked computers over USB
https://samy.pl/poisontap/
You can check how you actually use PoisonTap from the following movie.
PoisonTap - exploiting locked machines w / Raspberry Pi Zero - YouTube
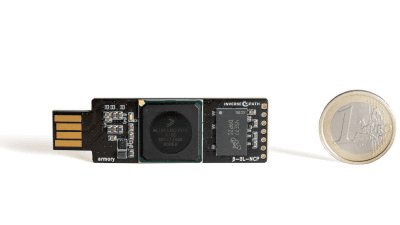
Samy of hacker has Poison Tap. PoisonTap is a hacking device that just loaded software developed by Sammy on the single board computer "Raspberry Pi Zero" of about 600 yen.
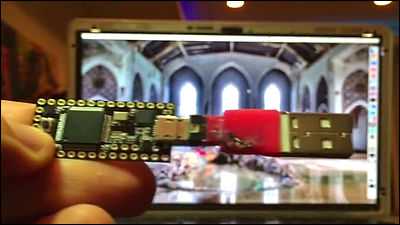
To use PoisonTap, just connect to the PC's USB port. It is a terrible device just to be easy to use.

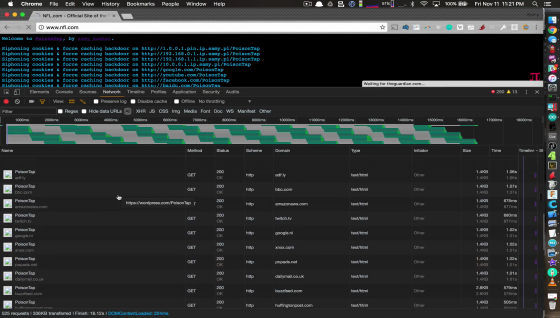
When PoisonTap is connected to PC and started up, PoisonTap emulates Ethernet. The PC recognizes PoisonTap as having Ethernet connection and sends a DHCP request.
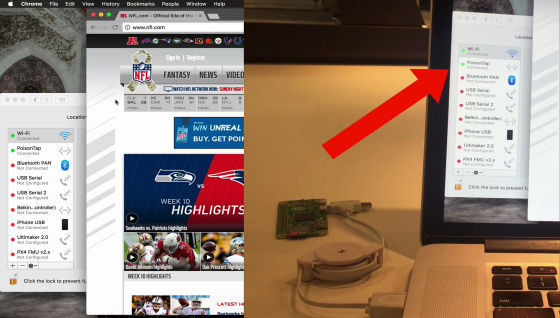
PoisonTap sends IP address to DHCP request from PC. Normally, such a connection is handled as a secondary network interface, but PoisonTap creates a DHCP response that makes all IP addresses on the Internet appear to be on the PoisonTap.
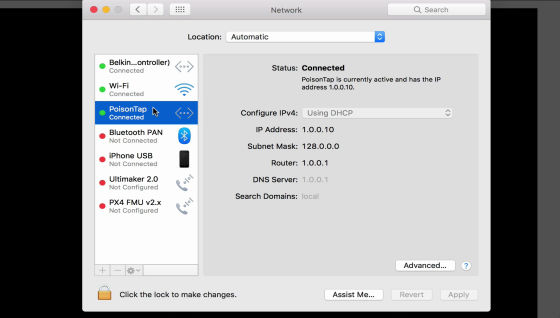
This forces the PC to force Internet traffic to be sent to PoisonTap rather than the Internet.
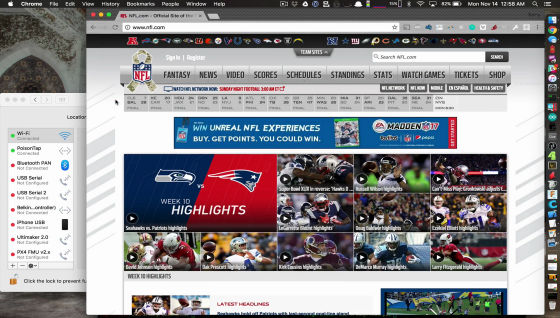
PoisonTap is now able to intercept Internet traffic as long as the browser is running on the PC. However, only HTTP requests can be intercepted.
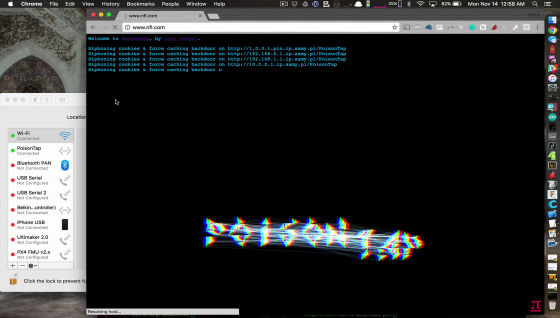
PoisonTap intercepts the HTTP request and replies with the attack code. Attack code attempts to steal cookies by camouflaging on any web site that has been hidden in hidden million iframes.
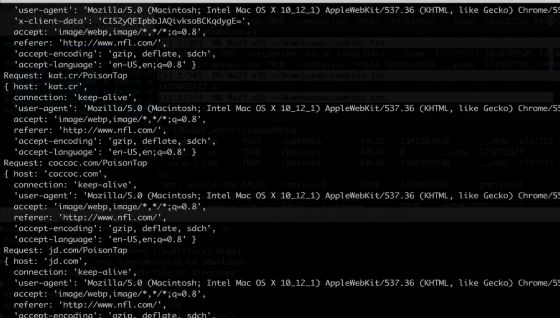
After that, we created a web-based backdoor that creates a WebSocket that is connected to the attacker's server. A hacker can send a command when WebSocket opens, so that the browser of the target PC can execute JavaScript code.
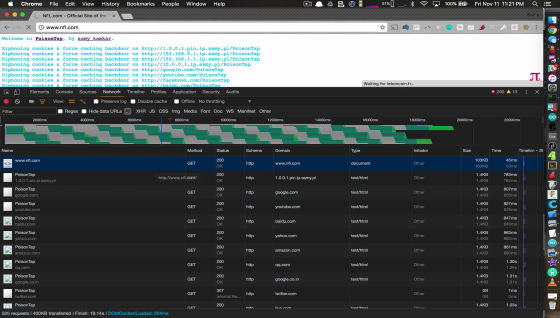
Also, PoisionTap performs a DNS rebinding attack to create a cache backdoor, allowing hackers to remotely access attackers' routers. Websites can block attacks by PoisonTap by using the Secure flag or by allowing only HTTPS.
Mr. Sammy said the code of the software installed in PoisonTapPublished on GitHubIt is in a state that everyone can use it.
Related Posts: