A vulnerability that can be exploited such as ``leaking IP address'' is found in Grand Theft Auto V's community server ``FiveM''

In the popular game software ``
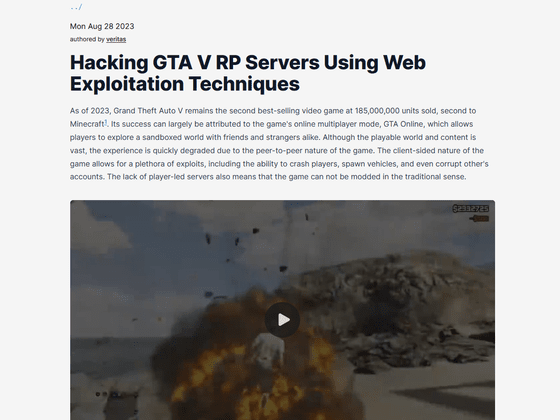
Hacking GTA V RP Servers Using Web Exploitation Techniques
https://www.nullpt.rs/hacking-gta-servers-using-web-exploitation
By using FiveM, a platform provided by
When you open FiveM, you can filter servers by name, region, number of players, and other criteria, as well as view a list of resources applied to the server.

Mr. Veritas focused on the server that applied the resource 'rcore_radiocar'. 'rcore_radiocar' is a resource that allows each player to broadcast music to nearby players by specifying a YouTube or SoundCloud link.
It has been confirmed that a file called 'SoundPlayer.js' exists within 'rcore_radiocar'.
[code]
rcore_radiocar
└── html
├──css
│ ├── reset.css
│ └── style.css
├── index.html
└── scripts
├── SoundPlayer.js
├── class.js
├── functions.js
├── listener.js
└── vue.min.js[/code]
According to Veritas, checking the details of SoundPlayer.js will reveal the functionality of how music is played on the client side. It turns out that SoundPlayer.js is actually processed by the 'create()' function.
SoundPlayer.js extracts the ID of a YouTube video from the URL specified by the user. If the ID cannot be extracted, it will be treated as an unknown source and the audio library ' Howler.js ' will be used to analyze and play the audio.
[code]
create()
{
// ...
var link = getYoutubeUrlId(this.getUrlSound());
if(link === '')
{
this.isYoutube = false;
this.audioPlayer = new Howl({
src: [this.getUrlSound()],
loop: false,
html5: true,
autoplay: false,
volume: 0.0,
format: ['mp3'],
onend: function(event){
ended(null);
},
onplay: function(){
isReady('nothing', true);
},
});
$('#' + this.div_id).remove();
$('body').append('
}
else
{
// ...
}
}
[/code]
However, this method is vulnerable to cross-site scripting (XSS). Veritas said, ``With this method, users can specify any URL, so if a malicious attacker creates and specifies an XSS URL, they can execute arbitrary JavaScript on another player's machine within the server. You can,” he points out.
Below is the demo video conducted by Veritas. When Veritas specified a link to a video on YouTube, other players could hear the music as well, and at the same time, the IP address of the user who heard the music was stolen.
Also, by using the FiveM vulnerability, it is possible to read the user's clipboard and write other data. According to Veritas, access to the clipboard function has been prohibited as of May 27, 2023.
In addition, 'chat/html/App.js' on the game server contains resources like the following that show how in-game messages are handled:
[code]
// window.post defined in chat/html/index.html
window.post = (url, data) => {
var request = new XMLHttpRequest();
request.open('POST', url, true);
request.setRequestHeader('Content-Type', 'application/json; charset=UTF-8');
request.send(data);
}
send(e) {
if(this.message !== '') {
post('http://chat/chatResult', JSON.stringify({
message: this.message,
}));
} else {
this.hideInput(true);
}
}
[/code]
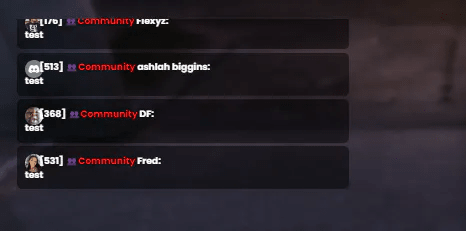
This resource could be exploited to trick another user into sending specific messages. In the image below, Veritas' code shows multiple users sending the message 'test'.
Also, by exploiting the resource 'gksphone', it is possible to use the in-game mobile phone feature to access the microphone that another user has allowed.
[code]
window.gksPhone = top.citFrames['gksphone'];
window.reqMicrophoneScript = top.document.createElement('script');
window.reqMicrophoneScript.innerHTML = `
function requestMicrophone() {
return navigator.mediaDevices.getUserMedia({ audio: true })
.then((stream) => {
// ...
})
}
requestMicrophone();
`
// inject the function into the gksphone resource
// which already has microphone access :)
window.gksPhone.contentWindow.document.body.appendChild(window.reqMicrophoneScript);
[/code]
In addition, it is possible to steal in-game currency from another player or forcefully change the appearance of an avatar by misusing resources.
Veritas warned that ``FiveM contains vulnerable resources that could harm thousands of players on hundreds of servers by exploiting a simple script.'' In addition, 'To prevent abuse, it is necessary to build a mechanism and a system that prohibits inappropriate character input. Also, it is important for server owners to regularly update installed resources to the latest version.' states.
Related Posts: