Personal information of 5.4 million Twitter users is stolen and exposed in the hacker forum, ``Beware of emails claiming to be Twitter in the future''

A forum used by hackers found that personal information of 5.4 million people leaked from Twitter was repeatedly traded. An interview with IT news site BleepingComputer confirmed that this data was stolen by exploiting a vulnerability reported by the bug bounty program and fixed in January 2022.
5.4 million Twitter users' stolen data leaked online — more shared privately
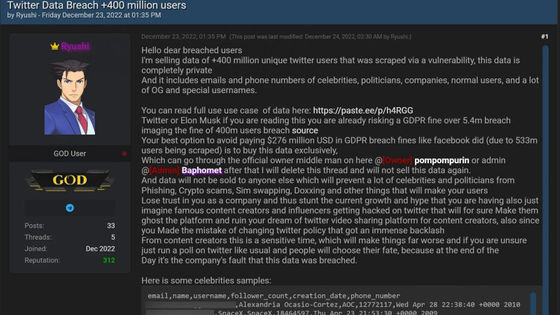
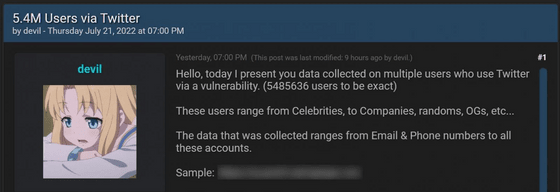
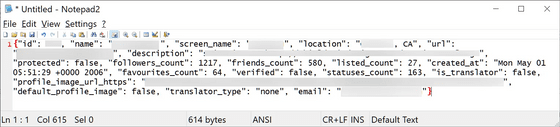
The problem of exposing a large amount of Twitter user data was first discovered in 2022, when a hacking forum said, `` Selling the personal information of more than 5.4 million Twitter users for $ 30,000 (about 4.1 million yen) '' Written in July. Most of the data shared by the threat actor named 'devil' consisted of public information such as Twitter ID, name, login name, location, authenticated status, but also private information such as phone number and email address. was included.
According to BleepingComputer, this data was collected in December 2021 using a vulnerability
It is unknown whether information disclosure on HackerOne was leaked, but BleepingComputer has information that multiple attackers are using this bug to extract personal information from Twitter.
Pompompurin, the administrator of the hacking forum, told BleepingComputer that after another threat actor named 'Devil' spread the vulnerability, they themselves exploited it to compromise the database of personal information. admitted to making
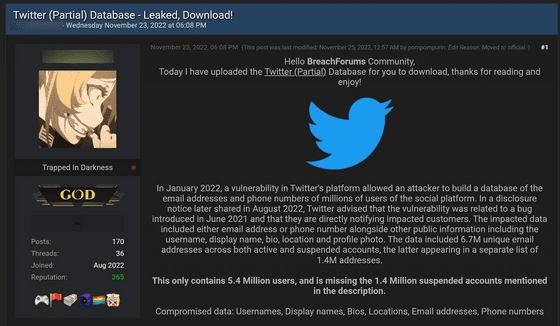
In addition to the 5.4 million user records sold, the database also includes 1.4 million additional profiles of suspended accounts collected using a separate API, for a total of 7 million records. It is said that it is. Pompompurin explained that it did not sell the database, but only shared it between a few individuals.
After 5.4 million user data was put up for sale in July 2021, hacking forums shared the same data for free on September and November 24th. Pompompurin has confirmed that this data is the same as previously sold, specifically containing 5,485,635 Twitter user records.
The issue was directly discovered by security expert Chad Loder. He deleted the post immediately after he first reported the incident on Twitter and reported the data leak again on Mastodon, a decentralized social network.
In a Twitter post, Loder said, ``I have received evidence of a massive Twitter data breach affecting millions of Twitter accounts in the EU and the US. After contacting some, I was able to confirm that this is real data.'
In a subsequent investigation, BleepingComputer obtained a sample file of user data different from the existing one, which contained 1,377,132 phone numbers of French users. BleepingComputer has confirmed that this additional leaked data is also genuine. In addition, the personal information of Twitter users obtained by BleepingComputer is different from that shared on the above-mentioned hacking forum managed by Pompompurin, so how widely exploiting Twitter vulnerabilities to steal data is done. points out BleepingComputer.
To Twitter users, BleepingComputer said, ``All emails claiming to be operated by Twitter should be scrutinized as the stolen data could be used in targeted phishing attacks to obtain login information. Potential phishing, especially if you receive an email claiming your account has been suspended, had login issues, or is about to lose verified status, and prompts you to log in to a domain other than Twitter Please ignore and delete the email because it is highly sensitive.'
BleepingComputer notified Twitter of this issue on November 24, 2022, but said that no response had been received at the time of writing the article.
Related Posts:
in Web Service, Security, Posted by log1l_ks