Vulnerability that websites and applications are hijacked by Apple's authentication system `` Sign In with Apple '', discoverers receive bounty over 10 million yen from Apple

Apple has announced a vulnerability in the Sign In with Apple authentication system announced at WWDC in 2019 that could allow an attacker to hijack a website or app. Bhavuk Jain, who discovered the vulnerability, reported the problem to Apple and said he won a prize of $ 100,000 (about 10.7 million yen).
Zero-day in Sign in with Apple
https://bhavukjain.com/blog/2020/05/30/zeroday-signin-with-apple/
Critical'Sign in with Apple 'Bug Could Have Let Attackers Hijack Anyone's Account
https://thehackernews.com/2020/05/sign-in-with-apple-hacking.html
Sign in with Apple bug discovery earns developer $ 100,000 | Appleinsider
https://appleinsider.com/articles/20/05/30/sign-in-with-apple-bug-discovery-earns-developer-100000
'Sign In with Apple' is a system that uses an Apple ID for authentication of third-party services such as websites and applications, and it is possible to realize login that combines Face ID and Touch ID. It is the same mechanism as the authentication system provided by Google, Faceabook, etc. At the time of article creation, if linked with other login systems, support until the end of June is obligatory .

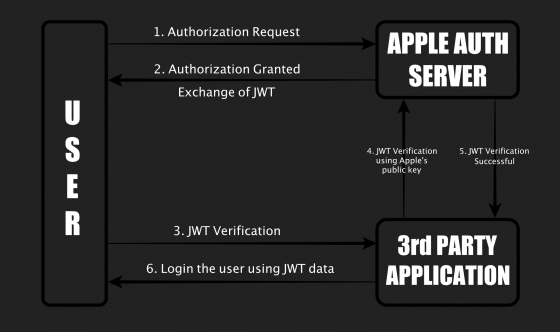
The 'Sign In with Apple' authentication mechanism looks something like this. First, the user sends an authentication request to Apple's authentication server based on his Apple ID information, and if the request is allowed, a JSON format token will be issued. After that, third-party services such as websites and apps receive tokens from users and acquire authentication authorization from Apple's server based on the tokens. Finally, it is a mechanism to allow users to log in.
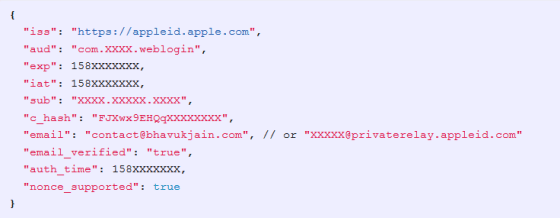
The content of the token that Jain actually obtained by analyzing the communication by 'Sign In with Apple' is as follows. This token is exchanged between Apple's authentication server, user, and third-party service to confirm that 'the user or server is not impersonated'.
However, Jain discovered in April 2020 that this 'Sign In with Apple' was vulnerable. By sending a request to Apple's authentication server, it was possible to issue tokens with any email address as well as Apple ID. In addition, Jain points out that it was possible to obtain authorization by signing the token with Apple's public key. This means that a malicious attacker can spoof your email address and issue a token to take over a website or app that you have logged in with 'Sign In with Apple.'
Apple's investigation and remediation of this vulnerability has already been completed, and there has been no evidence of its exploitation. Jain says that by reporting this vulnerability to Apple, he won a prize of 100,000 dollars (about 10.7 million yen)
Related Posts:
in Web Service, Security, Posted by darkhorse_log