iPhone users exposed to password leaks for three months

It has been revealed that Apple's Passwords app, introduced in iOS 18, had a vulnerability in communicating over HTTP, which could have led users to phishing sites without their knowledge. This vulnerability was not fixed for about three months.
Apple's Passwords app was vulnerable to phishing attacks for nearly three months after launch - 9to5Mac
https://9to5mac.com/2025/03/18/apples-passwords-app-was-vulnerable-to-phishing-attacks-for-nearly-three-months-after-launch/
The vulnerability in Apple's Passwords app was discovered by security research team Mysk, who discovered that not only was the app set to open password reset pages over unencrypted HTTP by default, but it also retrieved account logos and icons over HTTP.
Let's say a user opens the Microsoft change password page from within your app.
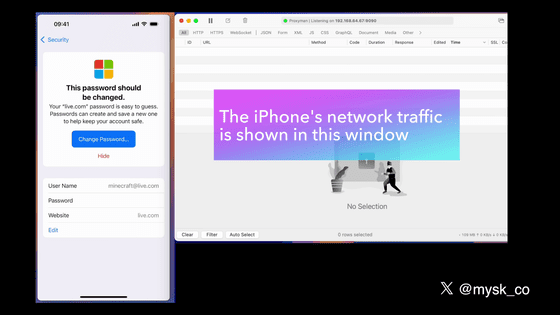
The app will then try to open the website over HTTP.
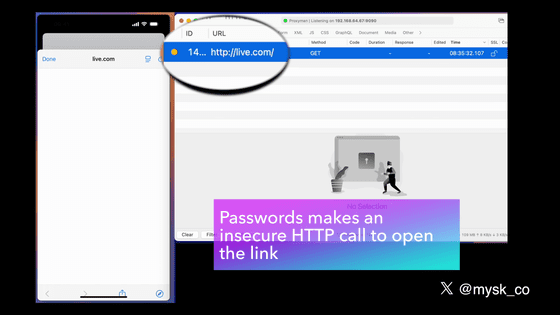
Most websites support unencrypted HTTP connections, but they automatically redirect users to the encrypted HTTPS protocol. The password change itself can be done on an encrypted page, so authentication information is not sent in plain text. However, if an attacker connects to the same network as the user, such as a cafe or airport Wi-Fi, and intercepts the HTTP request before the redirection, they could redirect the user to a phishing site.
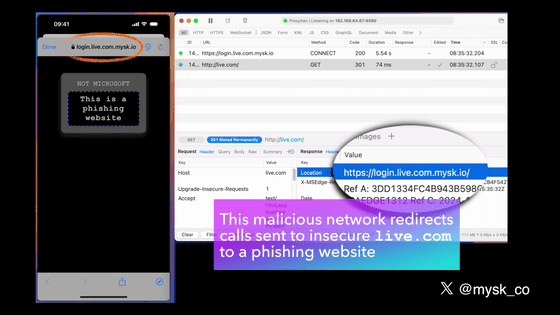
Mysk reported the vulnerability in September 2024, but it took Apple three months to patch it in iOS 18.2, released in December 2024. And it wasn't until March 2025 that Apple detailed a security update for the Password app.
'We're surprised that Apple didn't force HTTPS by default for such sensitive apps. Apple should provide security-conscious users with the option to disable icon downloads altogether,' said Mysk researchers.
Related Posts:
in Posted by log1p_kr