How Much Money Can You Earn If Apple's Great 'Bug Hunters' Hack Apple for Three Months?

Corporate interest in security risks is growing day by day, such as HackerOne, which pays incentives to receive reports of vulnerabilities.
Some companies participate in the Vulnerability Bounty Platform, while others set up their own incentive schemes. Sam Curry , a 'bug hunter' who works only with such vulnerability bounty as income, formed a hacking team and conducted activities to find Apple's vulnerabilities for three months. The amount of bounty received from the sexual bounty program ' Apple Security Bounty ' is posted on the blog.
We Hacked Apple for 3 Months: Here's What We Found
https://samcurry.net/hacking-apple/
Curry decided to start his efforts to find Apple's vulnerabilities in a tweet by programmer Bhavuk Jain saying, 'I found a zero-day vulnerability in'Sign in with Apple'and received a bounty.' It was said that. Curry, who believed that Apple Security Bounty was only targeted for vulnerabilities related to Apple's physical devices, learned that vulnerabilities related to web services were also targeted, and tried to find Apple's vulnerabilities. It seems that he decided to try it.
Zero-day in Sign in with Apple --bounty $ 100k https://t.co/9lGeXcni3K
— Bhavuk Jain (@ bhavukjain1) May 30, 2020
To make the project more enjoyable, Curry contacted hackers with whom he had worked and asked if he would like to work on the project together, and everyone participated despite the unguaranteed monetary rewards. He said he did it. The project members gathered in this way are Curry himself, Brett Buerhaus , Ben Sadeghipour , Samuel Erb , and Tanner Barnes . The project team worked for three months from July 6th to October 6th, 2020.
Curry explained that the project team scanned the web service first to get an overall picture of Apple's web service and identify 'hacked targets.' According to the scan, Apple owns the entire 17.0.0.0/8 IP address, there are 25,000 websites, 10,000 of which are in the '.apple.com' domain and 7,000 are unique. It turns out that the website exists under a domain such as the top-level domain '
After launching a brute force attack on the attack targets narrowed down by scanning, it was possible to obtain two interesting information: the vulnerability of the VPN server and the access token of Spotify. From the two vulnerabilities, he obtained information such as how to authenticate Apple's web services, the structure of applications, and how to use development tools, and relied on such basic information to launch attacks on each web service.
Curry's team found a total of 55 vulnerabilities in three months. Of these, 11 were 'urgent', 29 were 'high', 13 were 'medium', and 2 were 'low'. All vulnerabilities are posted on the blog, but Curry's interesting vulnerabilities are explained in more detail. For example, a demo movie has been released on YouTube for the 'Can hack iCloud mail to access all data stored in iCloud' vulnerability.
Proof of Concept-YouTube
When you open iCloud Mail from the web screen and check for new mail ...
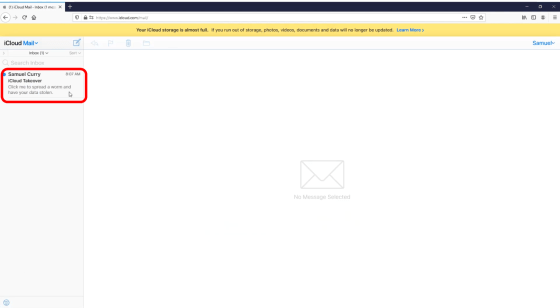
The words 'Your iCloud has been hacked!' Appear, and you can see how the images, movies, contacts, etc. stored in iCloud have been stolen.
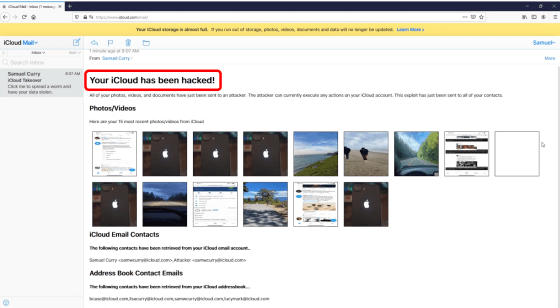
This attack exploits a vulnerability that integrates the contents of two HTML style tags in an email received by an iCloud email client. If you embed the style tag in the email text, you can execute the script remotely. Since all iCloud services are provided within the 'www.icloud.com' domain, it was possible to extract data in iCloud by running it in combination with a cross-site scripting vulnerability, Curry said. Explains.
As of October 8, 2020, Curry's team received a whopping $ 288,500 incentives from Apple Security Bounty. In addition, all the vulnerabilities that have been released have been fixed, and it is said that Apple's permission has been obtained for publication.
Curry worked on this project and described Apple Security Bounty as 'a solid way to go.' The high-severity vulnerabilities submitted by Curry's team were fixed in just four hours after submission. Also, Apple's authentication system was indescribably complex, Curry said.
Related Posts:
in Web Service, Security, Posted by darkhorse_log