'Bug vulnerability report existing on Facebook' that seems to understand 'how to earn bug bounty' a little

The 'Bug Reward Program', which pays a reward for reporting a software vulnerability, is a platform that can sometimes aim for a lot of money, just as there are '
How I hacked Facebook: Part One – Alaa Abdulridha
https://alaa.blog/2020/12/how-i-hacked-facebook-part-one/
Mr. Abdulridha said that he used the time created by the spread of the new coronavirus infection to obtain the certification test ' OSWE ' of the penetration test that invades web applications and finds vulnerabilities. Find the vulnerability of 'the ability to convert HTML to PDF' in the Facebook of the sub-domain 'legal.tapprd.thefacebook.com', that received a bounty $ 1000 from Facebook (about 104,000 yen) article is It seems that he decided to run a penetration test on 'legal.tapprd.thefacebook.com' as a trigger.
First, Abdulridha uses a fuzzing tool to find software bugs and explore what pages are on the website. As a result of searching by the tool, it was found that there are 43 pages that return '403 error' indicating access prohibition.
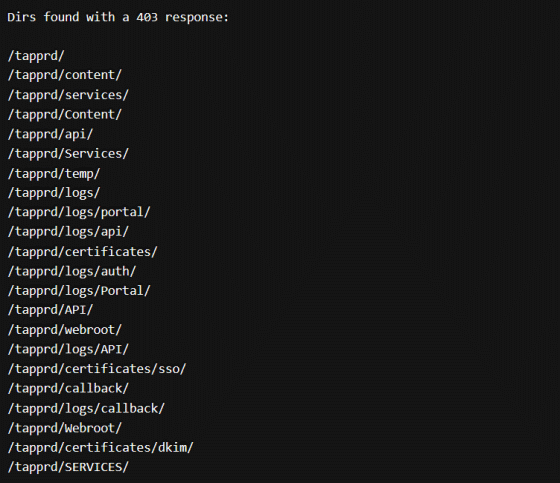
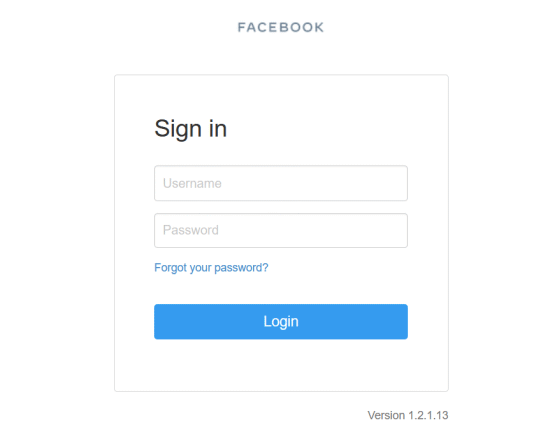
Furthermore, it turned out that 'https://legal.tapprd.thefacebook.com/tapprd/portal/authentication/login' did not result in a 403 error, and the following login screen was displayed.
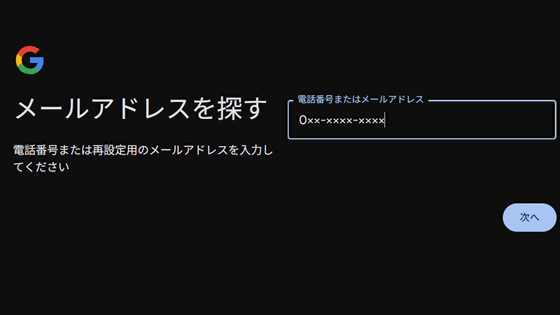
Examining the login screen further revealed the existence of a page called 'https://legal.tapprd.thefacebook.com/tapprd/auth/identity/user/forgotpassword'. When you access the URL, the screen for entering your email address will be displayed as shown below.
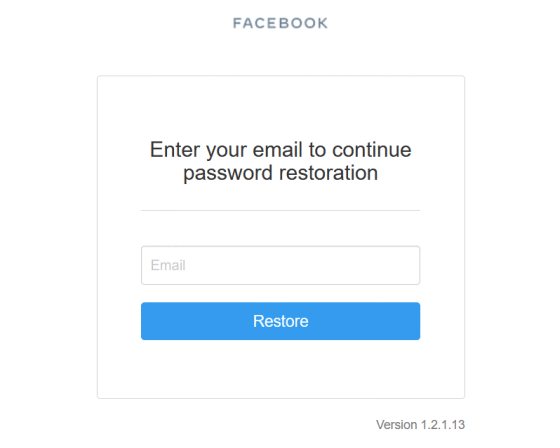
From the existence of the 'forgot password' page, Abdulridha searched the pages under 'https://legal.tapprd.thefacebook.com/tapprd/auth/identity/user/' with a tool, and found that 'https://legal. I found a page called 'tapprd.thefacebook.com/tapprd/auth/identity/user/savepassword'. Mr. Abdulridha thought that the 'save password' page had a vulnerability that could change the account password, so he tried sending the password to the page using
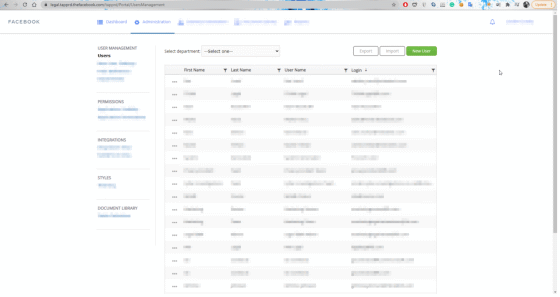
So Abdulridha got a list of admin accounts and random email addresses and sent them to the 'save password' page in sequence with the tokens, and succeeded in changing the password for an account. When I entered my e-mail address and changed password on the login screen, I heard that I was able to access the administrator screen.
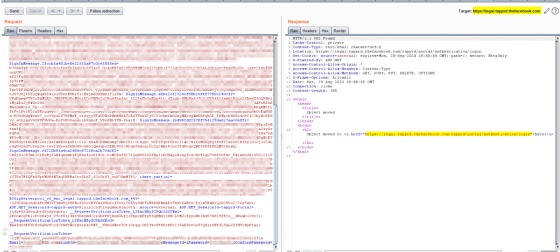
Regarding the seriousness of the vulnerability, Abdulridha said, 'Facebook employees logged in to this page with their work account, so if an attacker exploits the vulnerability, it may be possible to access the Facebook employee's account. There was. '
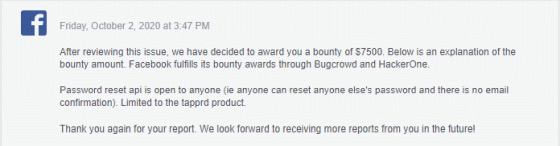
Mr. Abdulridha reported the vulnerability to Facebook and received $ 7,500 (about 780,000 yen) as a reward. In addition to this vulnerability, Abdulridha seems to have discovered a vulnerability related to the same page, and it is planned to release the contents in the near future.
Related Posts:
in Web Service, Security, Web Application, Posted by darkhorse_log