When a new vulnerability is disclosed in CVE, it will be scanned within 15 minutes in preparation for an attack and an actual exploit will be attempted within a few hours.

Generally, when information security vulnerabilities are disclosed, a worldwide common number 'CVE ID' is assigned to each vulnerabilities to identify the contents. Research has shown that hackers are scanning for these exposed vulnerabilities within at least 15 minutes, looking for unpatched endpoints.
2022 Unit 42 Incident Response Report: How Attackers Exploit Zero-Days
Hackers scan for vulnerabilities within 15 minutes of disclosure
https://www.bleepingcomputer.com/news/security/hackers-scan-for-vulnerabilities-within-15-minutes-of-disclosure/
According to cybersecurity deployer Palo Alto, hackers are constantly monitoring software vendors' bulletin boards looking for new vulnerabilities that can be used for initial access to corporate networks and remote code execution.
Attackers typically start scanning for vulnerabilities within 15 minutes of the announcement of the CVE. Scanning isn't particularly difficult, so even less-skilled attackers can scan vulnerable endpoints on the Internet, and more capable hackers will sell their scan results in the dark web market. It has been reported to be exploited within hours and often attack systems that have not had the opportunity to apply patches.
Attackers can start scanning for vulnerabilities faster, forcing system administrators to fix bugs before they can be exploited.

In the case of
According to data collected by Palo Alto, the most exploited network access vulnerability in the first half of 2022 was the Proxy Shell exploit chain, which accounted for 55% of all recorded exploit incidents. ProxyShell is an attack that exploits a chain of three vulnerabilities tracked as CVE-2021-34473, CVE-2021-34523, and CVE-2021-31207.
In addition, Log4Shell came in second with 14%, SonicWall's various CVEs were 7%, ProxyLogon was 5%, and Zoho ManageEngine ADSelfService Plus's RCE was abused in 3%.
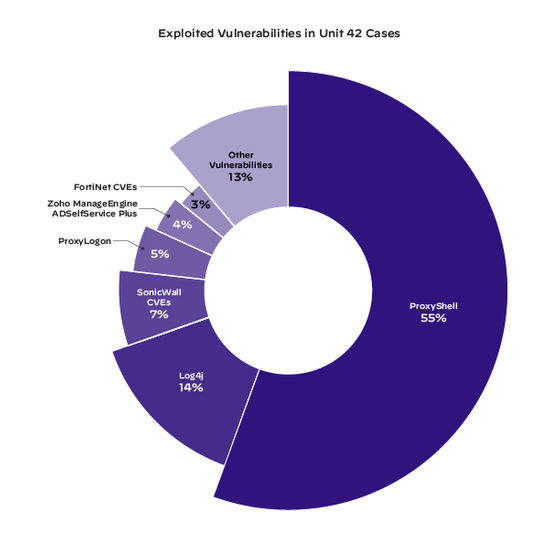
'As is clear from this statistic, the exploited flaws are not up-to-date and are mostly semi-permanent,' Palo Alto said. However, more valuable and more protected systems, where administrators quickly applied security updates, tend to be targeted shortly after zero-day or vulnerability disclosure.
Palo Alto points out that 'competition between defenders and malicious actors' is whether the time from vulnerability disclosure to patch application is fast or the time to attack is fast. He added that an attacker was invading the network with the help of phishing and insiders. It's very important to do it. You need to apply the update as soon as possible. '
Related Posts:







