The second ``fatal'' level vulnerability in OpenSSL is discovered, and a modified version will be released at night on November 1, 2022, so please update immediately

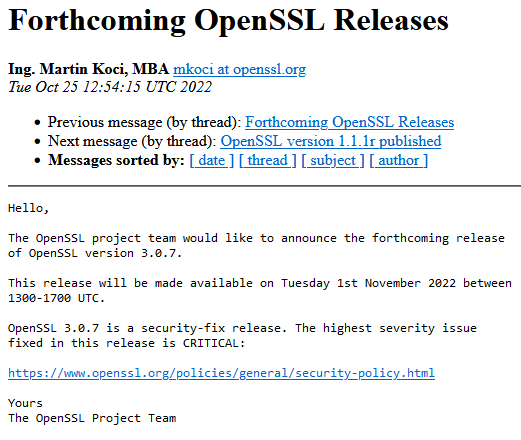
A vulnerability with a severity level of 'CRITICAL' was discovered in OpenSSL. The vulnerability has been addressed quickly, and a modified version of 'OpenSSL 3.0.7' will be released between 22:00 on November 1, 2022 and 4:00 on November 2, 2022, Japan time. It is the second time in history that a vulnerability of severity 'CRITICAL' was discovered in OpenSSL, following '
Forthcoming OpenSSL Releases
https://mta.openssl.org/pipermail/openssl-announce/2022-October/000238.html
OpenSSL is an open source library that supports the cryptographic communication protocol ' SSL/TLS ' and is widely used worldwide as a de facto industry standard library. For this reason, when the vulnerability 'Heartbleed' that can steal data was discovered in 2014, it bothered Internet administrators around the world.
The vulnerability discovered this time is ranked as having a severity of 'CRITICAL', like Heartbleed, and details have not been announced at the time of writing the article. According to OpenSSL's security policy , the ``CRITICAL'' label ``can be easily exploited remotely to compromise a server's private key'' and ``makes it possible to remotely execute code in common circumstances'' and `` common systems. ' Vulnerabilities that affect configuration and may be exploited .' Considering that 'Heartbleed' was the only 'CRITICAL' vulnerability before this vulnerability was announced, you can see how serious this vulnerability is.
The development team is already working on fixing the vulnerability, and plans to release a modified version of 'OpenSSL 3.0.7' between 22:00 on November 1, 2022 and 4:00 on November 2, 2022, Japan time. Network administrators are requested to update OpenSSL to the latest version as soon as possible.
In addition, OpenSSL version 1 series is maintained in parallel with version 3 series, but version 1 series is not affected by the vulnerability discovered this time .
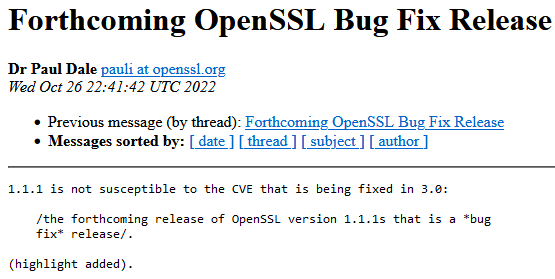
・ Added at 8:10 on November 2, 2022
At 1:00 on November 2, 2022 Japan time, we were notified that 'as a result of detailed analysis, the severity was lowered to HIGH (one step below CRITICAL) '.
OpenSSL Security Advisory
https://mta.openssl.org/pipermail/openssl-announce/2022-November/000243.html
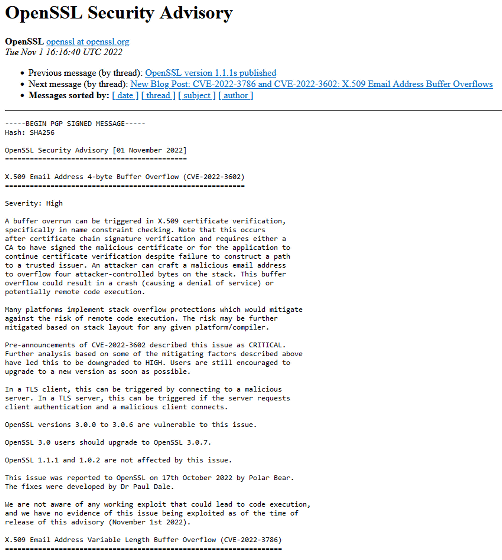
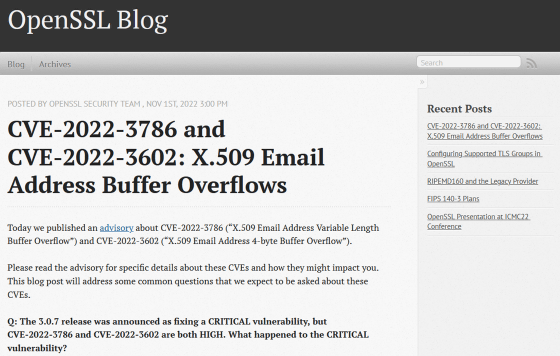
In addition, detailed information on the vulnerability, which was rated as 'CRITICAL' severity, was also released on the official OpenSSL blog. According to the blog post, the vulnerability in question was found to be unexploitable on many modern platforms that implemented proper memory protection. As such, it cannot be described as 'affecting general system configurations' and has been downgraded to 'HIGH' severity. However, the OpenSSL development team said, ``We recommend that users using versions 3.0.0 to 3.0.6 update to version 3.0.7 as soon as possible,'' calling for a quick update.
CVE-2022-3786 and CVE-2022-3602: X.509 Email Address Buffer Overflows - OpenSSL Blog
https://www.openssl.org/blog/blog/2022/11/01/email-address-overflows/
Related Posts: