Pointed out that there is a flaw in the ``CVE'' system that assigns IDs to vulnerabilities and manages them

When a vulnerability that becomes an information security flaw is discovered, it is given an identification ID called CVE (Common Vulnerabilities and Exposures), evaluated for severity, and listed. Daniel Stenberg, the maintainer of cURL, a transfer library, raises questions on his blog that there is a big problem with this CVE system.
CVE-2020-19909 is everything that is wrong with CVEs |
https://daniel.haxx.se/blog/2023/08/26/cve-2020-19909-is-everything-that-is-wrong-with-cves/
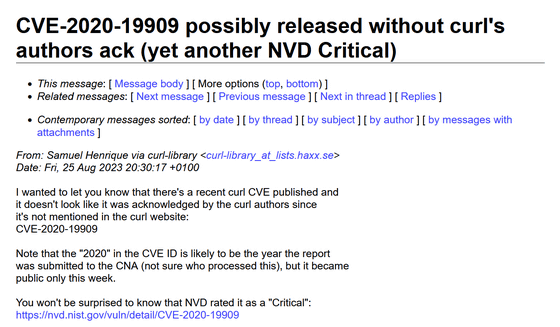
On August 25, 2023, Stenberg wrote on the cURL mailing list, 'We would like to inform you that a cURL-related vulnerability has recently been given the CVE identification ID of 'CVE-2020-19909' and has been reported. However, it is not mentioned on cURL's official website and does not appear to be endorsed by cURL's development side.'
``The cURL project is passionate about security and is constantly collaborating with security researchers,'' Stenberg said. As a result, Mr. Stenberg was surprised that cURL vulnerabilities were summarized in a CVE report and submitted without knowing anything at all.
According to sources, CVE-2020-19909 was released in late August 2023, a few days before being notified on the mailing list. Normally, when you report a vulnerability to CVE, the year you registered the report is listed, but CVE-2020-19909 has '2020'.
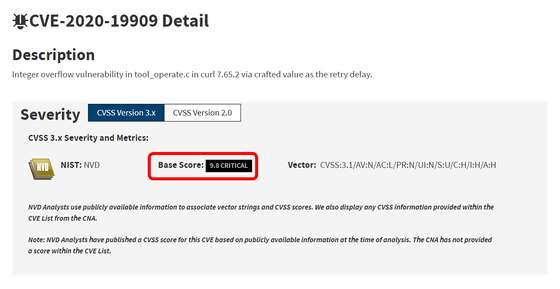
In the National Vulnerability Database (NVD), which is operated by the National Institute of Standards and Technology (NIST) in the United States, CVE-2020-19909 is described as ``a value crafted as a retry delay in tool_operate.c of curl 7.65.2. Integer overflow vulnerability'. Furthermore, the severity of this CVE-2020-19909 was rated as ``Critical'' with a score of 9.8 out of 10.
Mr. Stenberg said he was aware of the issues pointed out in CVE-2020-19909 because he was involved in many security reports, reviews, and complaint evaluations regarding cURL. In fact, on July 27, 2019, it was posted to HackerOne, a cybersecurity platform, that ``cURL command line options have an integer overflow problem.''
curl | Report #661847 - Integer overflows in tool_operate.c at line 1541 | HackerOne
https://hackerone.com/reports/661847
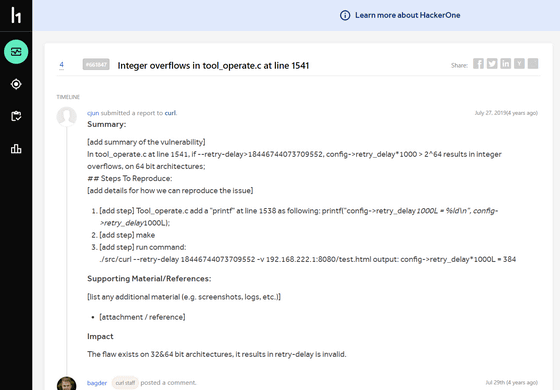
Stenberg confirmed that the reported issue was indeed a bug, closed the security report, submitted a pull request , and fixed the bug. This fix was implemented in version 7.66.0 of cURL released in September 2019. In other words, it is a problem that has been completely fixed by version upgrade at this time.
Stenberg said the issue pointed out in CVE-2020-19909 is the bug he fixed this year, stating that 'NVD is so committed to actually understanding and understanding vulnerabilities. I always knew it wasn't, and I don't understand why they set it to a severity of 9.8 again, just looking at the word 'integer overflow' and thinking, 'Oh, what a horrible flaw.' Clearly none of the NVD staff had used their brains to check for vulnerable code or patches to fix bugs, and by all accounts this bug was a security risk. You can see that it is not a problem, ”he commented.
Vulnerabilities are registered with NVD, which hosts the database of CVEs, and security information is shared with the world from there. Ubuntu has already reported that ' CVE-2020-19909 is not vulnerable and has no impact ', but when searching for 'CVE-2020-19909' it says 'a vulnerability with a severity of 9.8 was found in cURL' You will find many sites that share information.
Mr. Stenberg points out that NVD's failure to properly verify the contents of the CVE has caused erroneous information to spread around the world. In March 2023, the CVE-2023-27536 vulnerability was reviewed by the cURL maintainer, and although it was ranked low in severity, NVD rated it as 'CRITICAL' with a score of 9.8. It seems that there is something that has happened. At this time, he seems to have complained to NVD, and Mr. Stenberg describes NIST's Common Vulnerability Scoring System (CVSS) as 'a crap system'.
According to social news site Hacker News, ``In the past, anyone could submit a CVE report against anything, which sometimes led to malicious CVEs. , it is unclear why the 2020 CVE was registered now: someone took the identifying ID of a CVE that was reserved 3 years ago and for some reason decided to expose it as a cURL vulnerability. There was a comment saying, 'It looks like it .' It was also reported that the report could have been generated by AI-powered vulnerability detection automation, which would often have a high calculated severity.
Related Posts:
in Security, Posted by log1i_yk