A minor vulnerability in the open source tool 'node-ip' was reported as a 'critical vulnerability requiring urgent attention,' leading to a flood of contacts and a temporary archive of the repository by the developer.

The GitHub repository for the IP address management package '
Dev rejects CVE severity, makes his GitHub repo read-only
https://www.bleepingcomputer.com/news/security/dev-rejects-cve-severity-makes-his-github-repo-read-only/
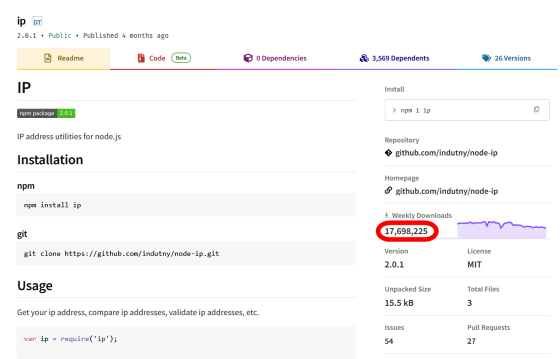
node-ip is an IP address management package for Node.js. Checking the package information for node-ip, we can see that it is a popular package that is downloaded more than 17 million times a week.
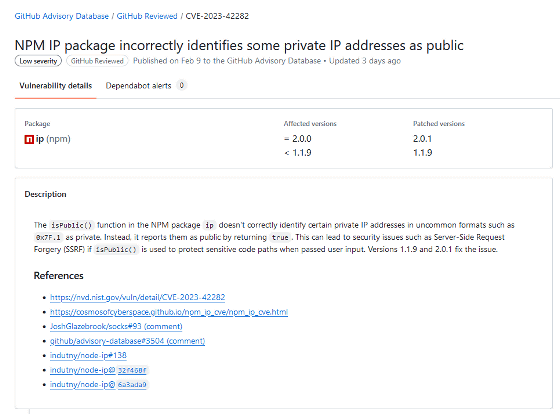
On February 9, 2024, a vulnerability in node-ip was reported in which 'private IP addresses may be treated as public IP addresses.' The report explains that exploiting the vulnerability could enable an SSRF attack , and it has been registered as a Critical vulnerability with a score of 9.8 in the National Vulunerability Database (NVD), a vulnerability database run by the National Institute of Standards and Technology ( NIST ). The CVE is 'CVE-2023-42282.'

After being registered in the NVD, the vulnerability was also
After the vulnerability was reported, Indutny
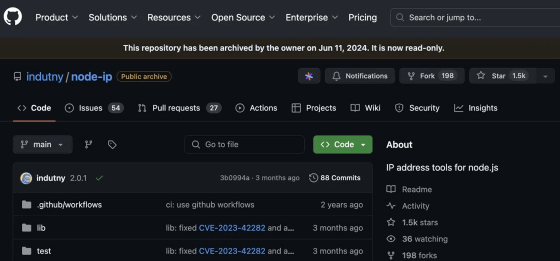
While acknowledging the existence of the vulnerability, Indutny argued that, 'although the report states that 'exploiting the vulnerability could enable an SSRF attack,' I don't believe there is any security risk to that extent,' and requested a review of the risk of the vulnerability on the same day it was archived.
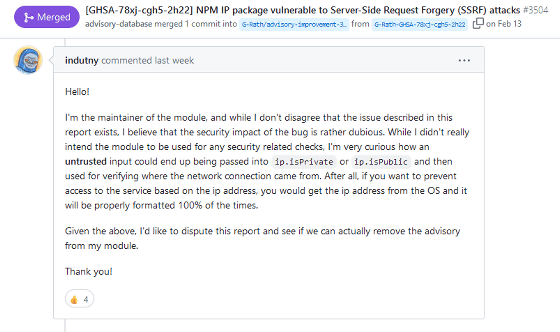
As a result, the vulnerability level was downgraded to Low on the GitHub Advisory Database. Indutny also received advice that 'you can configure
Indutny has unarchived node-ip after fixing the security risk on GitHub, but it remains vulnerable on the NVD with an urgent risk.
BleepingComputer, a foreign media outlet, points out that in light of Indutny's case, 'while most vulnerability reports are made by responsible security researchers, there are also some researchers who exaggerate their reports in order to build up the reputation of having found a critical vulnerability.'
In the past, developers of the data transfer tool cURL have complained about a vulnerability being reported as critical despite it actually being a low-risk vulnerability.
It is pointed out that there is a flaw in the 'CVE' system that assigns IDs to vulnerabilities and manages them - GIGAZINE

Related Posts: