Four zero-day vulnerabilities in IBM's enterprise security products, security researchers disclose information on GitHub

by
Security researcher Pedro Ribeiro published technical details and proof of concept on GitHub about four unfixed zero-day vulnerabilities affecting IBM Data Risk Manager (IDRM), IBM 's enterprise security software. .
PoC / ibm_drm_rce.md at master · pedrib / PoC · GitHub
https://github.com/pedrib/PoC/blob/master/advisories/IBM/ibm_drm/ibm_drm_rce.md
Researcher Discloses 4 Zero-Day Bugs in IBM's Enterprise Security Software
https://thehackernews.com/2020/04/ibm-data-risk-manager-vulnerabilities.html
According to Ribeiro, IBM Data Risk Manager contains serious vulnerabilities and high-impact bugs in 'Bypass Authentication', 'Insert Command', 'Insecure Default Password', 'Download arbitrary file'. An attacker could download arbitrary files via the network or execute code remotely.
An authentication bypass vulnerability is that a password error of an existing account including an administrator can be reset by exploiting a logical error in the session ID function. It has also been pointed out that an attacker could inject and execute a malicious command because IBM Data Risk Manager forces the user to use the nmap command to perform a network scan.
In addition, in the IBM Data Risk Manager
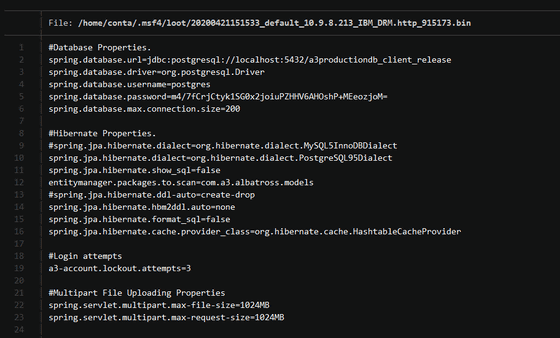
Ribeiro said that he tested on IBM Data Risk Manager version 2.0.1 to 2.0.3, but there is no mention of the vulnerability in any update log, and version 2.0.4 to the latest 2.0.6 also showed this. I think the vulnerability remains. 'IBM Data Risk Manager is security software for businesses that handle very sensitive information. The vulnerability left behind by such software means that it may be credentials to access other security tools. This can lead to serious information leakage for businesses, 'Ribeiro points out.
Ribeiro reportedly reported this problem to IBM, but IBM said, 'Because IBM Data Risk Manager only targets' enhanced support 'that customers can pay for, it is not covered by the vulnerability disclosure program. Then, we closed the case after creating a report. 'Since we were denied disclosure of vulnerability information, it seems that we have decided to disclose information on GitHub.
Ribeiro said, `` In any case, I don't have an account for the bug bounty platform HackerOne , and I don't agree with the disclosure terms of HackerOne or IBM, so I'm not asking for or expecting bounty . I just wanted to responsibly disclose this vulnerability to IBM and let IBM fix it. '
An IBM spokesperson told The Hacker News, a technical news media, that 'the process was incorrect and the researchers who reported to IBM did not respond appropriately. We are working on a fix and will be discussed in a security advisory. '
Related Posts:







