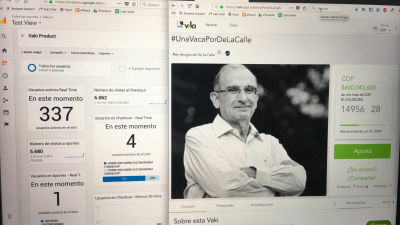
Hundreds of sites misconfigured Firebase security rules, exposing a total of 125 million pieces of sensitive information

Three security engineers, Logykk, mrbruh, and xyzeva, wrote in a blog post that misconfigured Firebase security rules have left hundreds of sites exposing a total of 125 million records containing plaintext passwords and other sensitive information.
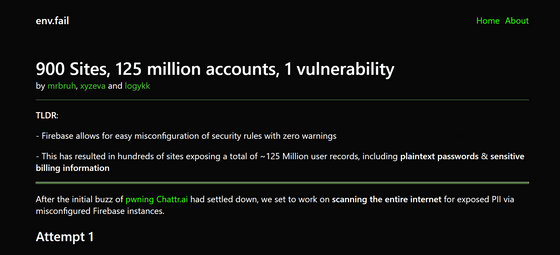
900 Sites, 125 million accounts, 1 vulnerability - env.fail
The three security engineers discovered that Firebase was misconfigured on a service called Chatter.ai , which restricts account privileges appropriately when you register via the official route on the website, but allows you to gain access to all of the Firebase databases if you create an account directly using the Firebase API.
The three suspected that similar misconfigurations were occurring on other sites, so they decided to scan the entire Internet. First, mrbruh created a scan script in Python, but memory consumption gradually increased, and after about an hour of scanning, they ran out of memory. Next, Logykk created a scanner in Go and ran the scan over the course of two to three weeks.
A total of 550,000 sites were found to have configurations that could potentially lead to Firebase misconfigurations. Xyzeva created a secondary scanning tool called Catalyst to check for read access to common Firebase databases.
In cases where read access was available, we collected a sample of 100 records to determine the type of information they contained and to estimate how much data had been exposed by comparing the total database size with the size of each record, and then stored the results in a private database, as shown below.
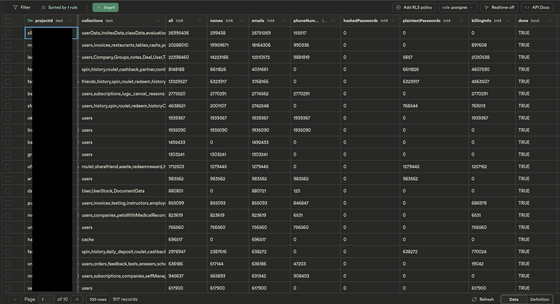
The estimation results are as follows.
Total number of records: 124,605,664
Names: 84,221,169
Email addresses: 106,266,766
Phone numbers: 33,559,863
Passwords: 20,185,831
Bank account and other billing information: 27,487,924
The three contacted the sites with the incorrect settings. They sent 842 emails over 13 days, and 24% of the sites corrected the settings, 1% responded, and two sites offered bug bounties.
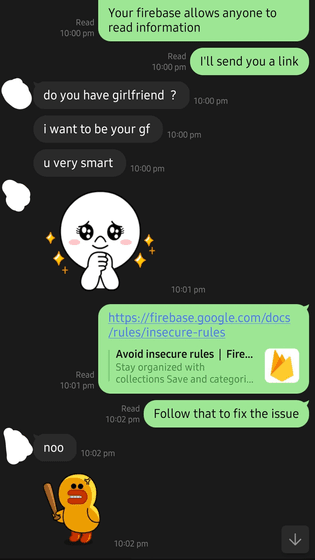
When he reported the mistake to customer support for an online gambling site that had stored 10 million passwords in plain text and exposed the details of 8 million bank accounts, he was met with flattering responses like 'Do you have a girlfriend?', 'I want to be your girlfriend' and 'You're so smart.'
In a thread on Hacker News, a news site where engineers gather, a Firebase employee cited the following reasons for the high number of security rule mistakes: 'Security rules are still a new concept, so new people who join a team and add data don't review the security rules,' 'The backend is implemented randomly in-house, so there is no concealment, which means they are scanned in bulk,' and 'The security rules themselves are difficult.'
Related Posts:
in Software, Web Service, Security, Posted by log1d_ts