A bug that can not encrypt the VPN connection is found on the iPhone, a simple workaround is also released at the same time

It turned out that iOS, which is the OS of iPhone, had a problem that the encryption of the
Apple iOS vulnerability causes connections to bypass VPN
https://protonvpn.com/blog/apple-ios-vulnerability-disclosure/
A Bug Existing Since iOS 13.3.1 Interferes With VPNs Encrypting Traffic-The Mac Observer
https://www.macobserver.com/news/product-news/ios-bug-vpns-traffic-encryption/
Swiss VPN provider ProtonVPN reported on March 25, 2020, 'A bug in iOS 13.4 has been detected that prevents all VPN traffic from being encrypted.' This bug has existed since at least iOS 13.3.1, which makes it possible to bypass VPN encryption, which may cause problems such as disclosure of user data or leakage of IP address. That is.

Normally, when the OS establishes a successful VPN connection, the OS will disconnect the existing connection and access the Internet through the VPN. However, due to this problem, normal communication is maintained for several minutes to several hours, and there is a possibility that communication may not be correctly encrypted.
ProtonVPN states, 'If your Internet connection is unencrypted, your data may be exposed, but this is rare nowadays. A more common threat is IP address disclosure. This would allow someone to steal your IP address or the server you connect to could see your IP address instead of the VPN server. '
The image below shows the results of ProtonVPN analyzing the traffic of iOS devices using the network analysis software
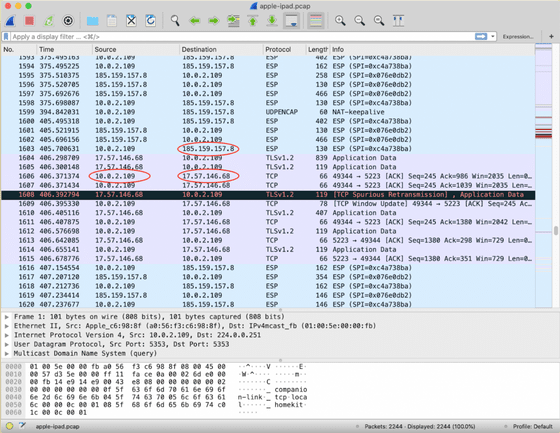
The serious thing is that VPN providers, including ProtonVPN, cannot address this issue because iOS does not allow VPN apps to forcibly terminate existing network connections. Therefore, the only solution to this problem is to fix iOS on Apple's side. ProtonVPN has already reported this problem to Apple, but at the time of writing the article, no patches or corrections by Apple have been distributed.
ProtonVPN commented, 'The users who are most affected by this bug are those in countries where governments are monitoring and civil rights are being violated.'
On the other hand, ProtonVPN also finds that in some cases, unencrypted communication can be disconnected with a simple operation. The method is as follows.
1: Connect to the VPN server.
2: Turn on airplane mode.
3: Turn off airplane mode.
This operation may disconnect the existing network and reconnect to the VPN, but it is not always certain. For this reason, ProtonVPN recommends using a more secure VPN connection for the time being.
Related Posts: