There is a zero-day vulnerability in Cisco's network equipment OS 'Cisco IOS XE' that can gain complete control of the device, attacks have already been confirmed
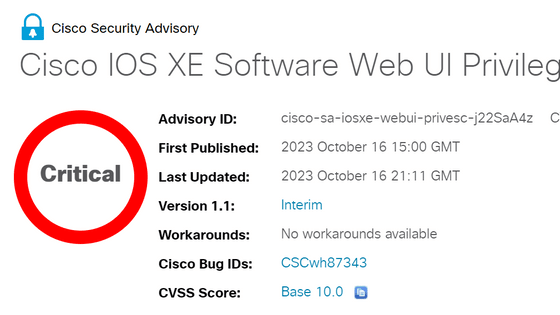
A privilege escalation vulnerability has been discovered in Cisco IOS XE, the operating system used in some Cisco routers and switches, including the ASR 1000 series. Attacks have already occurred even though a patch has not yet been released, and Cisco has published a page summarizing investigation methods and countermeasures.
Cisco IOS XE Software Web UI Privilege Escalation Vulnerability
https://sec.cloudapps.cisco.com/security/center/content/CiscoSecurityAdvisory/cisco-sa-iosxe-webui-privesc-j22SaA4z
Active exploitation of Cisco IOS XE Software Web Management User Interface vulnerability
https://blog.talosintelligence.com/active-exploitation-of-cisco-ios-xe-software/
The common vulnerability identifier (CVE) of the newly discovered vulnerability is 'CVE-2023-20198,' and targets Cisco IOS XE devices that have the web UI feature enabled and can be accessed from the Internet or untrusted networks. is. A successful exploit could grant the attacker full administrative privileges, effectively giving the attacker complete control over the affected router, allowing for further malicious activity. The Common Vulnerability Scoring System (CVSS) score is the highest, which is 10, making it a very critical vulnerability.
At the time of writing, there is no workaround yet, and Cisco recommends disabling the HTTP(S) server function on devices exposed to the Internet, as is traditional best practice.
Cisco has announced that the attack has been underway since September 18, 2023, and it is said that an implant was injected to make subsequent command execution easier. Cisco has outlined steps to check if your system has been compromised as follows:
◆ How to use Snort
Attacks can be detected by using the rule ID below.
・3:50118:2 - Can alert you to the first implant injection
・3:62527:1 - Can warn of implant interactions
・3:62528:1 - Can warn of implant interactions
・3:62529:1 - Can warn of implant interactions
◆How to access and detect the implant from the outside
If a hexadecimal string is returned when you run the command below, malicious code has been injected into the system. In addition, you need to replace the 'System IP address' part with the address of the router/switch, and if the system is set to only accept HTTP access, you need to change the schema to HTTP.
[code]curl -k -X POST 'https://system IP address/webui/logoutconfirm.html?logon_hash=1'[/code]
◆How to check system logs
Among the two logs below that are recorded when a user accesses the web UI, look for the one where the 'user name' part is a user name that the administrator does not recognize, such as 'cisco_tac_admin' or 'cisco_support.' Masu.
[code]%SYS-5-CONFIG_P: Configured programmatically by process SEP_webui_wsma_http from console as username on line[/code]
[code]%SEC_LOGIN-5-WEBLOGIN_SUCCESS: Login Success [user: Username] [Source: source_IP_address] at 03:42:13 UTC Wed Oct 11 2023[/code]
Also, you can check if there is anything unknown in the 'File name' part of the logs below that are recorded during the installation operation.
[code]%WEBUI-6-INSTALL_OPERATION_INFO: User: username, Install Operation: ADD filename[/code]
Related Posts:
in Security, Posted by log1d_ts







