NetCAT attacks using vulnerabilities in Intel processors can steal SSH session input and communication content

by
By exploiting Data Direct I / O (DDIO) technology that improves processing speed and reduces power consumption, which is installed in Intel processors, there is a risk that key input contents and communication contents with the server can be stolen. Researchers have issued warnings.
INTEL-SA-00290
https://www.intel.com/content/www/us/en/security-center/advisory/intel-sa-00290.html
NetCAT-VUSec
Weakness in Intel chips lets researchers steal encrypted SSH keystrokes | Ars Technica
https://arstechnica.com/information-technology/2019/09/weakness-in-intel-chips-lets-researchers-steal-encrypted-ssh-keystrokes/
Naming an attack is considered from the vulnerabilities found, researchers from the initials of 'network cache attack (Net work C ache At tack)' and 'NetCAT'. A demonstration video showing how to steal the contents of an SSH session with NetCAT has been released.
NetCAT remotely leaking keystrokes from a victim SSH session-YouTube
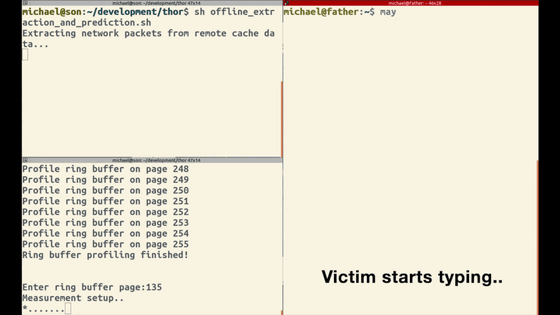
The left side of the screen shows the attacker and the right side shows the victim. Victim starts SSH session.
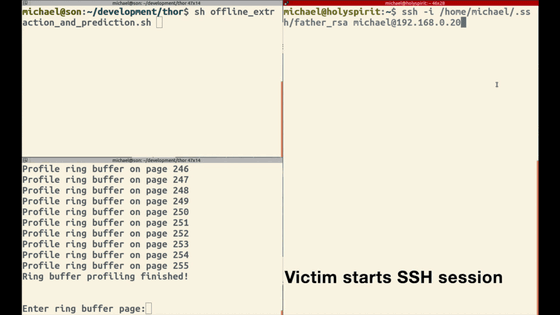
The attacker measures ring buffer activity and sets a profile.
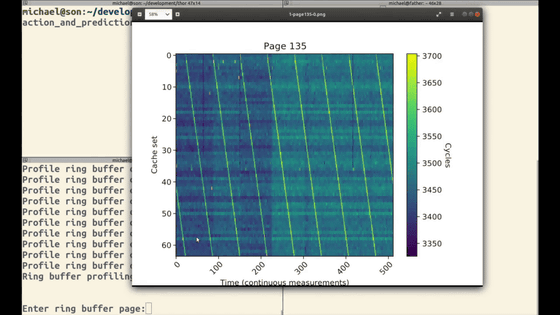
Victim starts typing
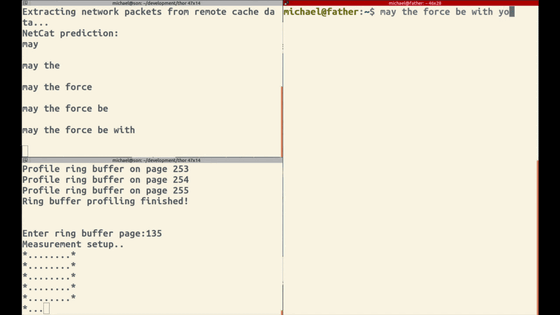
The attacker has successfully stolen the contents.
DDIO was specially introduced to improve the performance of high-speed network server applications. According to researchers, data centers and cloud environments where DDIO and Remote Direct Memory Access (RDMA) are enabled can be particularly serious, and Intel says `` If DDIO and RDMA are enabled 'Restrict direct access from untrusted networks.'
In this attack, researchers have simplified the attack by using an environment where RDMA is enabled, but strict requirements do not include `` RDMA enabled '', even if RDMA is disabled in the future. It is possible that they will receive similar attacks.
By the way, AMD and other manufacturers do not use DDIO, and network data is not stored in a shared CPU cache, so this vulnerability does not exist.
Related Posts: