Acer · ASUS · DELL · HP · Lenovo has detected dangerous vulnerability in software installed from the beginning, Lenovo starts calling for deletion
It became clear that there are vulnerabilities that may cause security problems in many of the software pre-installed on PCs that are sold in general. In response to this situation, Lenovo is calling users to delete software.
Out-of-Box Exploitation: A Security Analysis of OEM Updaters: Blog: Duo Security
https://duo.com/blog/out-of-box-exploitation-a-security-analysis-of-oem-updaters
Out-of-the-box exploitation possible on PCs from top 5 OEMs | Ars Technica
http://arstechnica.com/security/2016/06/how-pc-makers-make-you-vulnerable-to-man-in-the-middle-attacks-out-of-the-box/
This problem improves securityTwo-factor AuthenticationIt is clarified by investigation of the company "Duo Security" which provides the service. The company has published a report that is preinstalled on products of very common PC makers such as Dell, HP, Lenovo, Acer, Asus and summarizes vulnerabilities related to "updater" that monitors software updates.
(PDF)Out-of-Box Exploitation Out-of-Box Exploitation - A Security Analysis of OEM Updaters - out-of-box-exploitation_oem-updaters.pdf

Manufacturer's software preinstalled on the PC just bought is sometimes called "crapware (garbage software)" or "bloatware (software to eat only the capacity)" and even subjects that are disliked by users Although it is, it is also clear that most of them contain vulnerabilities this time. Duo Security is a scaffold for attacks against third parties by taking over their PCsMan-in-the-middle attackAbout the risk of causing Man in the Middle (MITM), conducted surveys of updating data of each manufacturer. Then, it turned out that large and small problems existed in the products of both manufacturers.
Updaters that are confirmed vulnerable infer the design of software from the way they behavereverse engineeringIn addition, it can easily perform the protocol for conducting communication requiring security "Transport layer security(TLS) "is not supported, and as a result it leads to a vulnerability that malware is illegally installed.
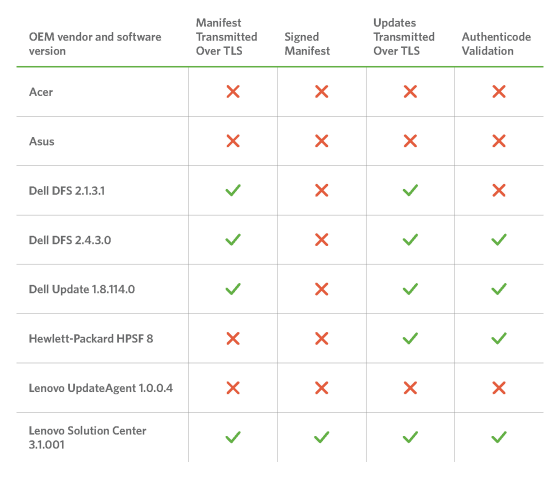
For each manufacturer, summarize the situation, the table is here. The problematic part is indicated by "x", but Acer and ASUS, and Lenovo's "UpdateAgent 1.0.0.4" seem to have confirmed the problem in all four items. Meanwhile, the same Lenovo's "Solution Center 3.0.001" clears all items. In addition, it was said that the survey was conducted on Windows 8.1 or Windows 10 models.
If these vulnerabilities are exploited, there is the danger of getting hijacked from devices on the same Wi - Fi network, for example, installing software at the administrator level.
On May 31, 2016 Lenovo said that the vulnerability in the update of "Lenovo Accelerator Application" provided by the company was found, and we have recommended to uninstall the software. The target model is the initial installation of Windows 10, some notebook PCs and desktop PCs with Lenovo Accelerator Application installed, and that the Lenovo Accelerator Application is not installed on ThinkPad and ThinkStation devices about. Detailed description of the target model and uninstallation method are described in detail in the following page, so if you own it, you should also check immediately for future safety.
Lenovo Accelerator Application Update Vulnerability - Lenovo Support (JP) | # 1 PC Maker
https://support.lenovo.com/jp/ja/product_security/len_6718
Related Posts: