The vulnerability 'Frag Attacks' inherent in virtually all Wi-Fi devices is exposed, user names and passwords can be leaked, and PCs can be hijacked.

Belgian security researcher Mathy Vanhoe (
FragAttacks: Security flaws in all Wi-Fi devices
https://www.fragattacks.com/
Fragment and Forge: Breaking Wi-Fi ThroughFrame Aggregation and Fragmentation
(PDF file) https://papers.mathyvanhoef.com/usenix2021.pdf
WiFi devices going back to 1997 vulnerable to new Frag Attacks | The Record by Recorded Future
https://therecord.media/wifi-devices-going-back-to-1997-vulnerable-to-new-frag-attacks/
New vulnerabilities discovered in the Wi-Fi standard compromise devices from 1997 to the present – Explica .co
https://www.explica.co/new-vulnerabilities-discovered-in-the-wi-fi-standard-compromise-devices-from-1997-to-the-present.html
There are three types of vulnerabilities disclosed by Mr. Vanhoe, all of which are due to the design itself of the wireless LAN standard 'IEEE 802.11' that is the basis of the current Wi-Fi. One of the three types is 'frame aggregation ' that sends multiple Ethernet frames together into one 802.11 frame, and the other two types increase the reliability of the connection by dividing the large frame into smaller frames. It is related to 'frame fragmentation'.
For frame aggregation vulnerabilities, frame aggregation is a feature that improves network speed and throughput by combining small frames into large frames. Because of this feature, each frame has a header to identify 'whether it's combined', but Vanhoe says there's no protection in the 'combined' state header. Therefore, it is possible for the attacker to intercept the traffic by modifying this header part.
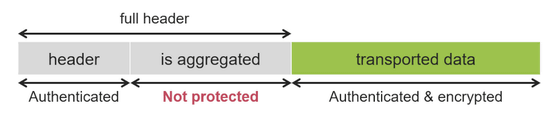
Vanhoe said that he has confirmed the existence of routers that allow frame forwarding even when the sender is not authenticated, and points out that these routers can perform the above aggregation attack without user interaction. ..
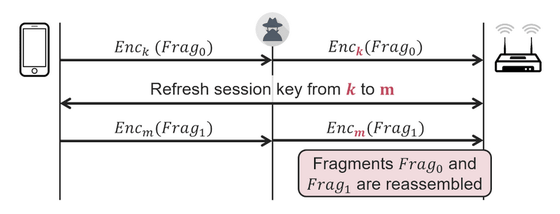
One of the vulnerabilities related to frame fragmentation is related to the encryption key used to divide a large frame into smaller pieces to improve the reliability of the connection. This encryption key is used as a common encryption key when dividing one frame, but it is passed from the device side because there is no process of 'verifying the encryption key' on the Wi-Fi connection side. The fragment will be restored by using the encrypted key unconditionally. Therefore, according to Vanhoe, data can be leaked by passing an encryption key that is different from the original encryption key. However, this method is only 'theoretically possible'.
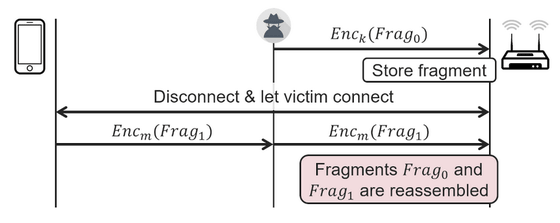
The second vulnerability related to frame fragmentation is related to the design that unreconstructed fragments are left undeleted in the memory of Wi-Fi devices when a client disconnects from the network. By using this design and placing a malicious fragment in the memory of the access point, it is possible to forcibly combine the fragment sent by the recipient with the malicious fragment that was placed. That thing. 'It sounds unusual, but it can actually steal data,' Vanhoe said of the vulnerability.
Vanhoe said that the general implementation of these fragmentation-related vulnerabilities also has a flaw that 'there is no process on the part of the recipient to check if the fragments belonged to the same frame.' Vanhoe explained that this flaw allows 'frame forgery' by mixing fragments extracted from different frames, and in some cases even mixing encrypted and plaintext fragments. doing.
According to Vanhoe, these vulnerabilities can be used to spoof encrypted frames, allowing Wi-Fi device usernames and passwords to be intercepted and the device itself to be hijacked. In fact, Vanhoe is demonstrating how to steal usernames and passwords from New York University's student pages and hijack Windows 7 machines connected to a protected Wi-Fi network via smart appliances. I will.
FragAttacks: Demonstration of Flaws in WPA2 / 3 --YouTube
Regarding this vulnerability disclosure, Vanhoe provided information to the Wi-Fi Alliance and the Industry Consortium for Advancement of Security on the Internet (ICASI), which are industry groups related to Wi-Fi. The announcement was made after a period of time for the patch to be created. The Common Vulnerabilities and Exposures (CVEs) for these three types of vulnerabilities are the following 12 types.
・CVE-2020-24588
・CVE-2020-24587
・CVE-2020-24586
・CVE-2020-26145
・CVE-2020-26144
・CVE-2020-26140
・CVE-2020-26143
・CVE-2020-26139
・CVE-2020-26146
・CVE-2020-26147
・CVE-2020-26142
・CVE-2020-26141
In the Windows Update distributed on May 12, 2021, bug fixes were made for 3 out of 12 types.
Related Posts: