The danger that the contents can be specified in the encrypted mail of 'Microsoft Office 365', Microsoft has no plan to respond

'Microsoft Office 365' allows you to send and receive encrypted emails in order to securely exchange emails with people inside and outside your organization. But the encryption at its core relies on an insecure operation called Electronic Codebook (ECB) mode. Despite being pointed out about this problem, Microsoft has clearly stated that it will not respond as 'it is not vulnerable'.
Microsoft Office 365 Message Encryption Insecure Mode of Operation | WithSecure™ Labs
It was the security company WithSecure's laboratory that revealed the problem of 'Microsoft Office 365'.
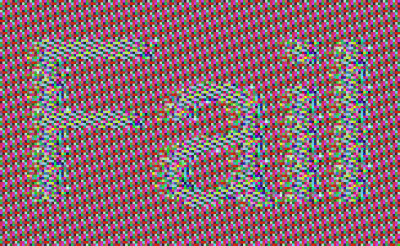
According to WithSecure Labs, 'Microsoft Office 365 Message Encryption (OME)', which sends and receives encrypted messages with 'Microsoft Office 365', encrypts by operating in ECB mode, but ECB mode is used to identify messages Since the structural information of the message is leaked, there is a possibility that a malicious third party can identify the contents of the message.
An image extracted from an OME-encrypted email, shown by WithSecure Labs as an example.
The problem of the ECB mode is also pointed out by the US National Institute of Standards and Technology.
Proposal to Revise SP 800-38A | CSRC
https://csrc.nist.gov/News/2022/proposal-to-revise-sp-800-38a
The scope of influence extends to most of the encrypted messages by OME, and it is possible that attacks against encrypted messages that have been sent, received, and intercepted in the past will be performed offline. There is no way to prevent sent messages from being analyzed, and even the rights management feature doesn't solve the problem.
In addition, knowledge of the encryption key is not required to exploit the ECB mode vulnerability, and there is no effect of remediation by encryption key protection measures.
WithSecure Labs contacted Microsoft multiple times about this, but the final Microsoft response was, ``Reports are not considered to meet security service standards, nor are they considered violations. No changes have been made, so a CVE (unique number given to vulnerabilities and incidents) will not be issued.'
Neither administrators nor end users have a way to avoid this vulnerability and use OME safely, so WithSecure Labs cites 'avoid OME' as the only countermeasure.
Related Posts:
in Web Application, Security, Posted by logc_nt