Attack methods are developed to steal passwords and data by using Wi-Fi chips and Bluetooth chips installed in billions of smartphones as a trigger.
Research teams at the University of Darmstadt in Germany and the University of Brescia in Italy have revealed a method that enables password extraction and traffic manipulation on Wi-Fi chips by attacking the Bluetooth component of the device.
Attacks on Wireless Coexistence: Exploiting Cross-Technology Performance Features for Inter-Chip Privilege Escalation
(PDF file)
Bugs in billions of WiFi, Bluetooth chips allow password, data theft
https://www.bleepingcomputer.com/news/security/bugs-in-billions-of-wifi-bluetooth-chips-allow-password-data-theft/
The latest electronic devices such as smartphones have separate components that support Bluetooth, WiFi, and LTE in the SoC, and these components have dedicated security functions, but these components are energy efficient. We share antennas for reasons such as improving throughput.
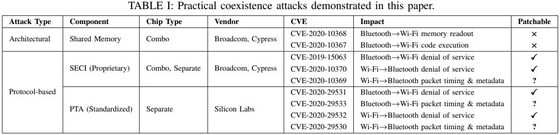
A paper published by research teams at the University of Darmshut and Brescia this time exposes the remote code execution vulnerabilities inherent in Wi-Fi or Bluetooth chips and bridges the resources shared by these chips in the device. It is about the method of expanding the attack target to each chip of. The research team is actually performing arbitrary code execution, memory read, and DoS attacks against SoCs manufactured by Broadcom, Cypress, and Silicon Labs.
Products equipped with these SoCs include iPhone 11, iPhone X, iPhone XR, iPhone 8, iPhone SE (2nd generation) Samsung Galaxy S20, Note 20 5G, etc.
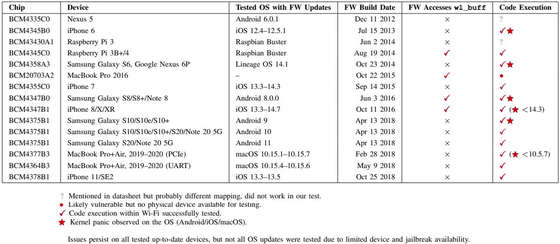
The research team reported the flaw to Broadcom, Cypress, and Silicon Labs, but it seems that there are SoCs that are no longer supported or SoCs for which firmware is not applicable, and in most cases they cannot be fixed.
The common vulnerability identifiers assigned to this vulnerability are 'CVE-2020-10368', 'CVE-2020-10367', 'CVE-2019-15063', 'CVE-2020-10370', 'CVE-2020-10369', and 'CVE'. -2020-29531 '' CVE-2020-29533 '' CVE-2020-29532 '' CVE-2020-29530 'There are nine types, and these vulnerabilities require hardware fixes or depending on the fix. It is said that there are some that significantly reduce performance.
Related Posts:
in Hardware, Smartphone, Security, Posted by darkhorse_log