'Blast RADIUS Attack' Reported Compromises Popular User Authentication Protocol

BLAST RADIUS
https://www.blastradius.fail/

RADIUS/UDP vulnerable to improved MD5 collision attack
https://blog.cloudflare.com/radius-udp-vulnerable-md5-attack
New Blast-RADIUS attack breaks 30-year-old protocol used in networks everywhere | Ars Technica
https://arstechnica.com/security/2024/07/new-blast-radius-attack-breaks-30-year-old-protocol-used-in-networks-everywhere/
New Blast-RADIUS attack bypasses widely-used RADIUS authentication
https://www.bleepingcomputer.com/news/security/new-blast-radius-attack-bypasses-widely-used-radius-authentication/
Many network devices on enterprise and communications networks use RADIUS as an authentication protocol. RADIUS has been the de facto standard for lightweight authentication for many years, and is supported by almost all switches, routers, access points, and VPN concentrators shipped from the 2000s to the time of writing.
The purpose of RADIUS is to seamlessly authenticate, authorize, and account for remote logins, and is essential for managing client/server interactions. At the time of writing, it is used in a variety of situations, including VPN access, DSL and FTTH provided by Internet service providers, Wi-Fi and 802.1X authentication , 2G and 3G cellular roaming, 5G data network name authentication, mobile data offloading, and authentication to critical infrastructure management devices.
RADIUS uses a hash function called MD5 for encryption, but MD5's 'collision resistance,' which means that it is difficult to calculate a combination of messages that return the same hash value, has been broken, and it is said that it should not be used when strength is required. However, MD5 is still used in several network protocols, and RADIUS is one of them.
A new attack method called 'Blast RADIUS' has been reported that exploits the RADIUS vulnerability ' CVE-2024-3596 ' and an MD5 collision attack to allow attackers to bypass RADIUS authentication. This allows attackers with access to RADIUS traffic to manipulate server responses and add arbitrary protocol attributes, allowing attackers to gain administrative privileges on RADIUS devices without the need for brute force attacks or credential theft.
The diagram below shows the general flow of RADIUS authentication using passwords. First, the user enters their username and password (1) and sends it to the client, which then sends an access request (2) to the server. In response, the server returns access acceptance (3) to the client, and the user is notified that login was successful (4).
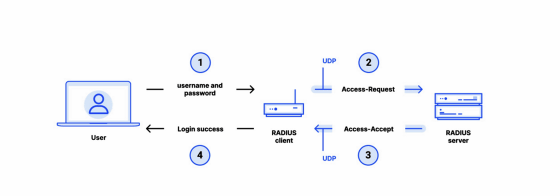
Blast RADIUS requires an attacker to be able to perform
The flow of Blast RADIUS reported by the research team is as follows: First, an attacker posing as a user performs '1: Entering an incorrect username and password', and the client sends '2: Access request' to the server. The attacker performs a man-in-the-middle attack to intercept the request, and performs '3: MD5 collision attack' to modify '4: Access request' to the server. Then, the attacker intercepts '5: Access denied' from the server and modifies the response to the client, changing it to '6: Access accepted', so that the client can communicate '7: Login successful' to the attacker.
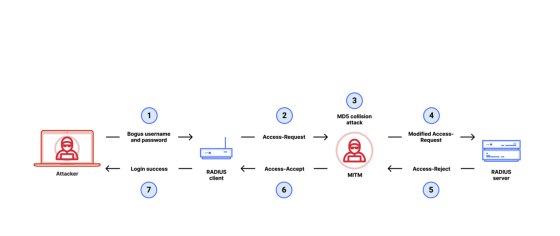
'The Blast RADIUS attack allows a man-in-the-middle attacker between a RADIUS client and server to forge a valid protocol accept message in response to a failed authentication request. This forgery allows an attacker to gain access to network devices and services without having to guess or brute-force passwords or shared secrets,' the research team said.
The research team is working with at least 90 vendors of vulnerable products to send out patches that implement a short-term fix to prevent Blast RADIUS, but the long-term solution to prevent Blast RADIUS is to use TLS or DTLS when transporting RADIUS, which the IETF is working on.
Related Posts:
in Software, Web Service, Security, Posted by log1h_ik