Due to SSL vulnerability, it turned out that more than 11 million HTTPS sites worldwide, including major Japanese sites, can be attacked
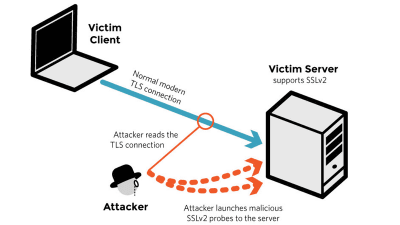
Security researchers have announced that there is a vulnerability that can easily be attacked on HTTPS sites encrypting communications via SSL / TLS. Attack with this vulnerability "DROWNThere are possibilities to receive a website that includes major Japanese sites such as Mainichi Shimbun, Nintendo, Hatena, LINE.
DROWN: Breaking TLS using SSLv2.pdf
(PDF file)https://drownattack.com/drown-attack-paper.pdf
DROWN Attack
https://drownattack.com/
"Decrypting RSA with Obsolete and Weakened eNcryption (DROWN)" is a vulnerability included in SSLv2. If this vulnerability is exploited, the encryption of the TLS session is canceled (decrypted) by the cross protocol attack and the communication is intercepted He said there was a fear. Because encrypted SSL / TLS communication exchanges information such as passwords and credit card numbers, highly confidential information may leak due to DROWN attack.
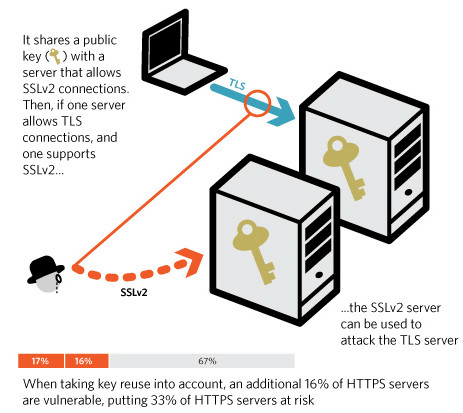
SSLv2 used in the 1990's before the TLS protocol appeared is rarely used already, but the troublesome thing about the DROWN attack is that even if the server is transitioning from SSL to TLS SSLv2 Where you support attacks where you support. 17% of the whole HTTPS site supports SSLv2 and is subject to DROWN attack.
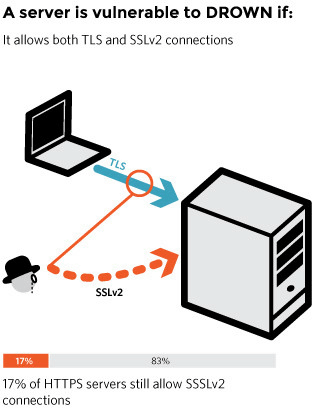
Furthermore, encryption may be broken if even a server that does not support SSLv2 uses a common secret key with a server that supports SSLv2. Considering the case where there is a server sharing the secret key, 33% of the HTTPS site is actually subject to the DROWN attack, so you can see the seriousness of the DROWN problem.
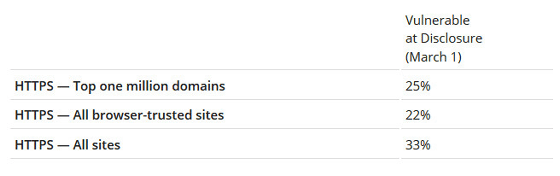
By the way, it is said that there is a risk of receiving DROWN attack by 25% in top 1 million domains, 22% in sites judged to be "reliable" in browsers.
DROWN The site "DROWN Attack" created to disseminate the risk of attacks has released a tool to judge whether a vulnerability is included in the server. To do so, enter the domain or IP address in the text box at the middle of the page below and click "Check for DROWN vulnerability".
DROWN Attack
https://drownattack.com/
The list of "top 10000 sites subject to DROWN attack" as of March 1, 2016 has also been released and includes major websites such as Mainichi Newspapers in Japan, Hatena, Sakura Internet, Excite, LINE .
DROWN Attack - Vulnerable Popular Sites
https://drownattack.com/top-sites.html

OpenSSL already released the latest version of 1.0.2 g, 1.0.1 s to invalidate the SSLv 2 protocol and excluded export grade SSLv 2. Besides DROWN attacks, OpenSSL also recommends that you do not use SSLv2 because it contains vulnerabilities.
OpenSSL Security Advisory [1st March 2016]
https://www.openssl.org/news/secadv/20160301.txt
Related Posts: