Exploit ``Terrapin Attack'' that allows man-in-the-middle attacks on SSH connections is discovered
The Terrapin Attack is an attack that violates the integrity of the Secure Shell (SSH) protocol by manipulating sequence numbers during the handshake process in the Secure Shell (SSH) protocol, which securely sends commands to computers over unsecured networks. An attack has been detected. This action allows an attacker to delete or modify messages exchanged over the communication channel, allowing a variety of attacks.
Terrapin Attack
Terrapin Attack: Breaking SSH Channel Integrity By Sequence Number Manipulation
(PDF file) https://terrapin-attack.com/TerrapinAttack.pdf
Terrapin attacks can downgrade security of OpenSSH connections
https://www.bleepingcomputer.com/news/security/terrapin-attacks-can-downgrade-security-of-openssh-connections/
Terrapin Attack was discovered by security researchers Fabian Baumer, Marcus Brinkmann, and Joke Schwenk from Ruhr University Bochum in Germany. Vulnerabilities related to this Terrapin Attack have been reported as CVE-2023-48795 , CVE-2023-46445 , and CVE-2023-46446 .
Terrapin Attacks work when an attacker acts as a man-in-the-middle against a remotely connected network. In order to perform a Terrapin Attack, the connection the attacker wants to interfere with must be protected with the encryption algorithm ``ChaCha20-Poly1305'' or ``CBC with Encrypt-then-MAC.'' Both are encryption algorithms added to the SSH protocol in the 2010s, and researchers say that 77% of publicly available SSH servers on the internet support one or the other, and of those, 57% are It is said that the encryption algorithm is selected with priority.
The following is a schematic overview of the Terrapin attack. Communication is exchanged (handshake) between the client and server, but the attacker inserts the message 'IGNORE' before the handshake ends. This changes the sequence number and allows the attacker to delete the message 'EXT_INFO' from the server.
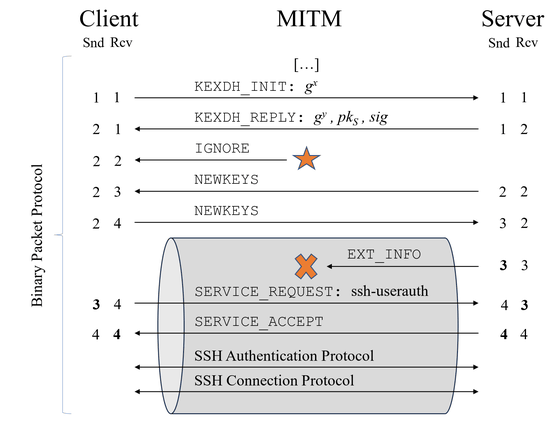
Baumer and his team wrote, ``The Terrapin Attack exploits weaknesses in the SSH transport layer protocol by combining new cryptographic algorithms and encryption modes introduced by OpenSSH more than a decade ago. It affects a large portion of the population as it is being adopted in the country.”
The research team has released a scanner tool that can check whether you are affected by the Terrapin Attack vulnerability in the GitHub repository below.
GitHub - RUB-NDS/Terrapin-Scanner: This repository contains a simple vulnerability scanner for the Terrapin attack present in the paper 'Terrapin Attack: Breaking SSH Channel Integrity By Sequence Number Manipulation'.
https://github.com/RUB-NDS/Terrapin-Scanner
According to the research team, OpenSSH, AsyncSSH , LibSSH , PuTTY , Transmit 5 , SUSE , etc. are affected by Terrapin Attack. However, the research team reports that they have contacted approximately 30 providers that implement SSH and shared their findings so that they can fix the details of the Terrapin Attack before making it public.
Tera Term, a remote logon client for Windows, released version 5.1, a security update that addresses this Terrapin Attack, on December 19, 2023.
Tera Term 5.1 has been released. https://t.co/wCwtavl7jr
— TeraTerm Project (@Tera_Term) December 18, 2023
Supports SSH 'strict key exchange'.
Related Posts:
in Security, Posted by log1i_yk