Utilizing the vulnerability of security chip 'T2' that Apple's Mac series is hacked only by USB
Apple's proprietary security chip, the
Plug'nPwn --Connect to Jailbreak
https://blog.t8012.dev/plug-n-pwn/
A custom USB-C cable can jailbreak the T2 chip in a MacBook Pro | AppleInsider
https://appleinsider.com/articles/20/10/13/a-custom-usb-c-cable-can-jailbreak-the-t2-chip-in-a-macbook-pro
T2 exploit team demos a cable that hacks Mac w / o user action --9to5Mac
https://9to5mac.com/2020/10/13/t2-exploit-team/
The jailbreak tool 'checkra1n' for Apple products is compatible with the OS 'Bridge OS' for T series chips, so it is now possible to access the T2 chip and operate the Touch Bar via the T2 chip. However, jailbreaking with checkra1n required a step for the user to switch the Mac device to ' device firmware update (DFU) mode', which could not be hacked without user interaction.
Jailbreak tool supports Apple's Mac security chip 'T2', enabling intrusion into Touch Bar-GIGAZINE

This time, the team 't8012 Development Team' that hacks the T2 chip reports that it succeeded in jailbreaking the T2 chip just by connecting a modified connector to the USB-C port of the Mac device. A demo movie of jailbreaking the MacBook Pro's T2 chip via USB has been released.
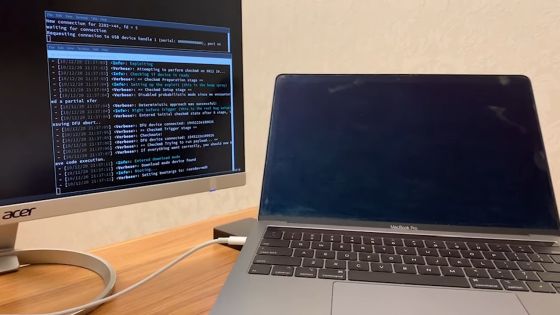
When you connect the connector to the USB-C port of your MacBook Pro ...
The screen of the MacBook Pro disappeared, and the monitor on the left showed the analysis.
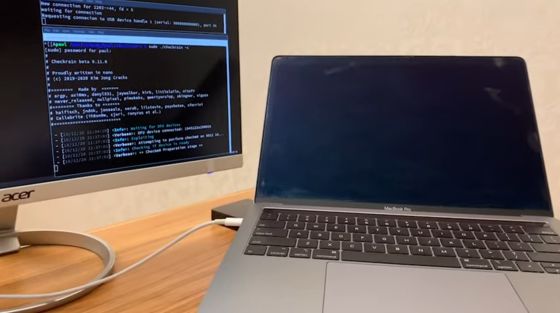
The word 'DFU device connected' is displayed on the monitor, indicating that the MacBook Pro has been successfully entered into DFU mode without any special user action.
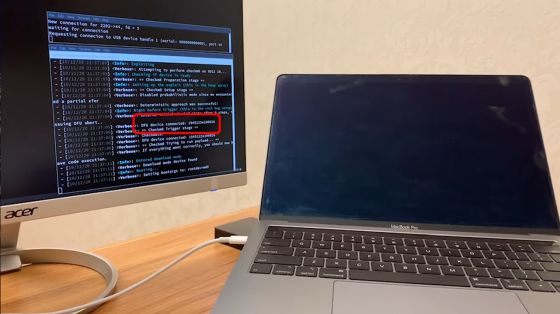
Jailbreak by checkra1n was done as it was, and hacking was successful. In the movie, I log in to bridgeOS with SSH and display the kernel information.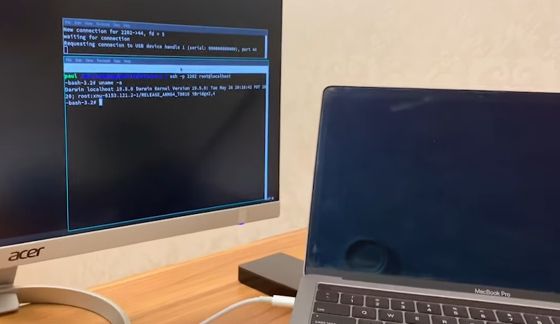
We have also succeeded in changing the boot logo via the T2 chip.

The image below shows the pinout of the MacBook series USB-C port. 'CC1' and 'CC2' are pins used to control the power supply standard '
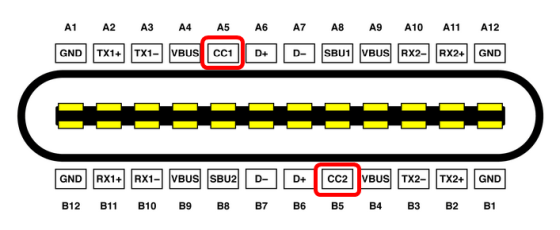
Among Mac products, laptop-type devices have a T2 chip and keyboard directly connected, so by exploiting the vulnerability discovered this time, an attack such as loading a keylogger into a Mac product from a hacking device disguised as a charger Will be possible. “Apple needs to document the vendor-specific messages used in Mac products so that consumers can understand the security risks,” points out the t8012 Development Team.
Related Posts:






