Review of 'YubiKey 5C NFC', a physical security key equipped with USB Type-C and NFC that can be used on both smartphones and PCs

Yubico, a physical security key maker, released the latest model of the 'Yubikey' series ' YubiKey 5C NFC ' on September 9, 2020. YubiKey 5C NFC is equipped with USB Type-C and NFC, and it is said that it is a physical security that can be used in common with notebook PCs, iPhones, and Android terminals, so actually using YubiKey 5C NFC in two stages I tried to authenticate.
Introducing the new family of YubiKey! YubiKey 5C NFC is born! | Yubico
The YubiKey 5C NFC package is very simple.

Open along the perforations on the back.

YubiKey 5C NFC is a model in which the terminal of

When authenticating with YubiKey 5C NFC, you can use it as a security key by touching the central metal part marked 'y'.

The design on the back looks like this.

A comparison of the size with a transportation IC card. The length is about half that of an IC card.

Let's use YubiKey 5C NFC as a physical security key for Google 2-step authentication in combination with Pixel 3a equipped with both USB Type-C and NFC.

The setup method for Google 2-step authentication is the same as Google's physical key 'Titan security key'.

When you complete the 2-step authentication setup and try to log in to your Google account, you will be asked to use your security key, so tap 'Start'.
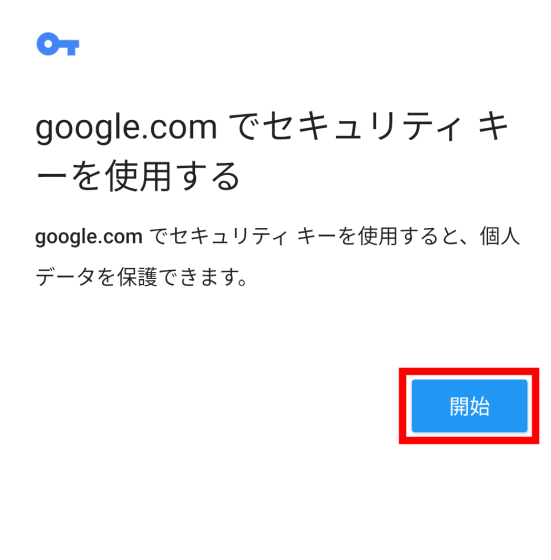
First, tap 'Use security key with USB' to authenticate with USB.
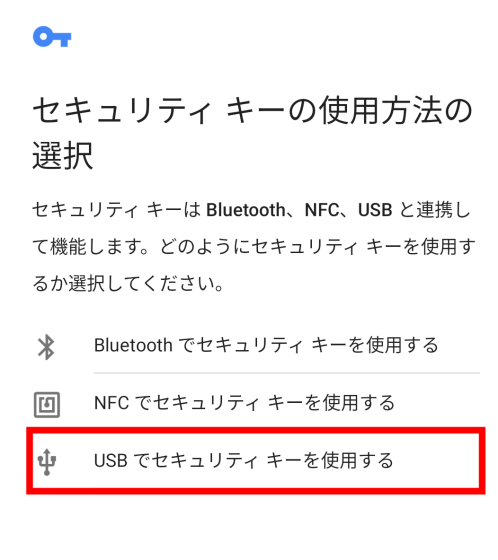
Insert the YubiKey 5C NFC into the Pixel 3a and touch the metal part.

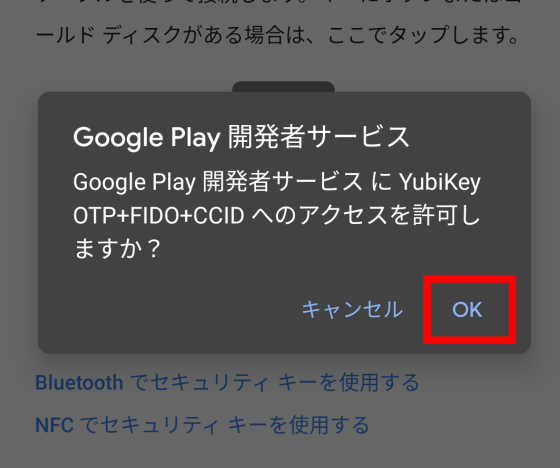
The Google Play developer service will ask for permission to access YubiKey, so click 'OK' ...
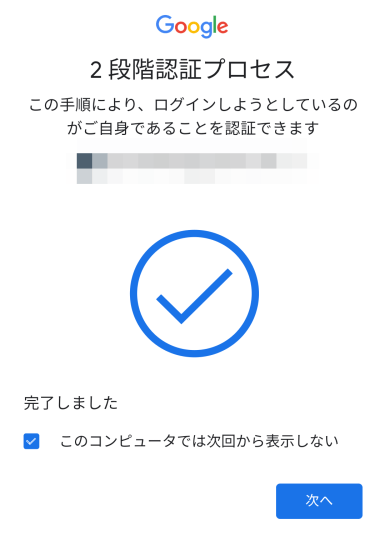
I cleared the two-step authentication and was able to log in.
This time I decided to try NFC authentication. Select 'Use security key with NFC' on the screen for selecting how to use the security key.

You will be instructed to apply the security key to the NFC sensor section of your smartphone.
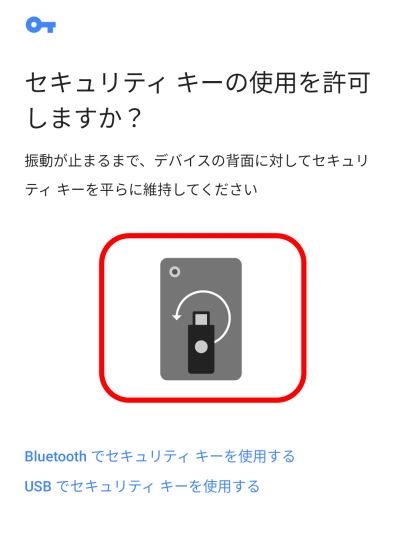
The range in which the sensor on the Pixel 3a responds to the security key is quite narrow, and you need to move the YubiKey as if you were stroking the smartphone while touching the metal part to find the point where the reading is successful. When YubiKey is detected by the smartphone, the smartphone's vibration will be activated.

YubiKey was read by the smartphone via NFC, and the two-step authentication was successful. Like this, the YubiKey 5C NFC is characterized by being able to be used as a security key via both USB Type-C and NFC.
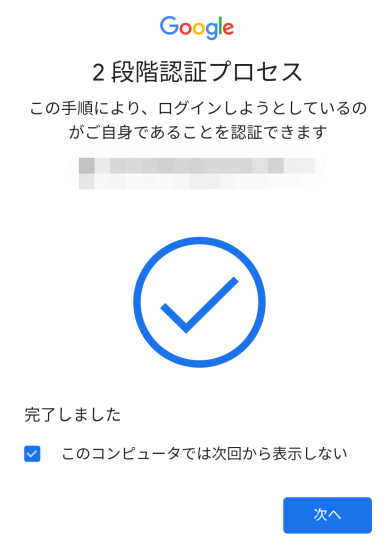
Since it supports NFC, it can of course be used on iPhones that do not have USB Type-C.

When you try to log in to Google from Safari on your iPhone, you will be asked for two-step verification, so click 'Next'.
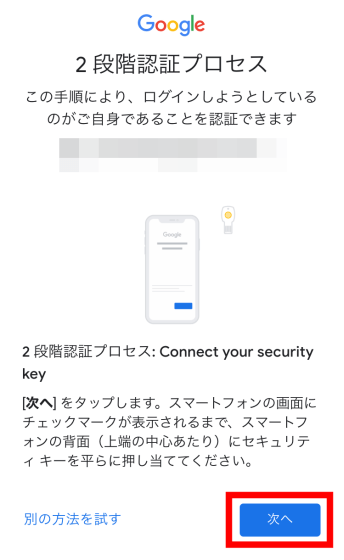
You will be prompted to 'Insert your security key or move the key closer to the top of your iPhone.'
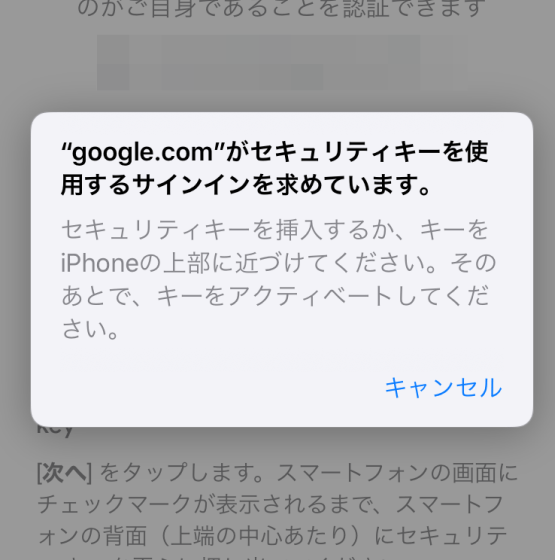
When I held the Yubi Key over the top of the iPhone, it immediately detected the key and succeeded in authentication.

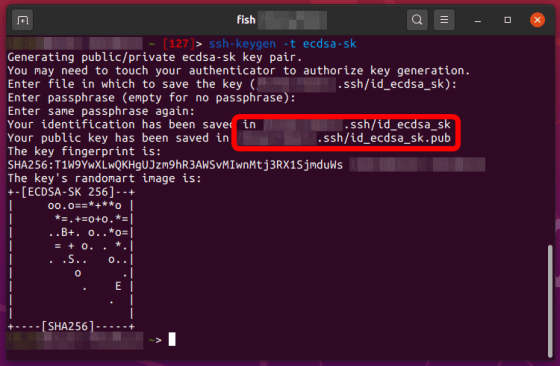
You can also use the YubiKey 5C NFC as your SSH private key by using the key types 'ecdsa-sk' and 'ed25519-sk' that have been supported since
For example, if 'ecdsa-sk' is selected as the key type of the 'ssh-keygen' command, the generated public key 'id_ecdsa_sk.pub' will be sent to the login destination server, and the key file 'id_ecdsa_sk' will be sent to the client PC. If you place it and specify 'id_ecdsa_sk' as the private key when connecting from the client PC, you can authenticate with YubiKey 5C NFC.
Since YubiKey 5C NFC supports FIDO2 , it can also be used with WebAuthn adopted by GitHub etc. Safari and Android on iOS are also supporting authentication by FIDO2, and YubiKey 5C NFC may be available in more situations in the future.
Related Posts: