What is the latest High Security Measures Law eradicating phishing damage by Google employees?

Phishing damage that stolen passwords for logging in to sites and services is a very important problem in the Internet society. While the login method of inputting passwords by hand is still being used, the "two-step authentication" using SMS and smartphone applications and the authentication technology "WebAuthn" which makes it unnecessary to memorize the password at all in the first place have appeared. It is.
Google: Security Keys Neutralized Employee Phishing - Krebs on Security
https://krebsonsecurity.com/2018/07/google-security-keys-neutered-employee-phishing/
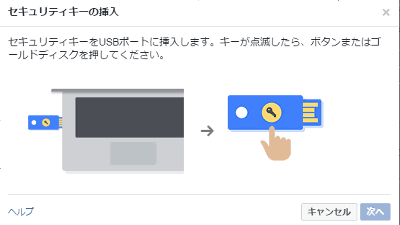
It is an important issue for Google, which has about 85,000 people and handles confidential information, to enhance the security of staff. In order to cope with repeated fishing damage, Google introduced a security device "security key" of a type to be inserted in the USB port. Then it seems that the damage of the phishing has not been reported at all after that.
Google introduced Yubico 's two-step authentication security key " YubiKeys ". This device is compliant with FIDO Universal 2nd Factor (U2F), and in the past when YubiKeys is required for a password, simply press the button on the device and authenticate safely.

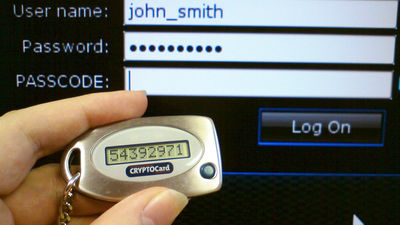
Behind the mechanism of YubiKeys is the concept called "two-step authentication". Traditionally, this method where sending "one-time password" to the mobile phone by SMS etc. and inputting it by hand when the login is necessary was effective, but it was effective, but if you use SIM card "A hole" was pointed out that a third party's illegal login became possible if it was stolen and put in another terminal. Also in the sense of "using smartphones", Google Authenticator provided by Google was basically unable to escape the same problem.
Google · Facebook · Yahoo! I found a method to break through 2-step verification such as GIGAZINE
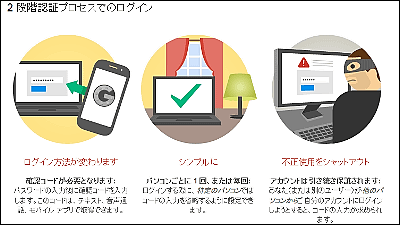
Meanwhile, a device such as YubiKeys that conforms to U2F has a big feature that authentication is performed safely only by pressing a button, and that information is never leaked to others. The open source U2F is supported by Dropbox, Facebook, Github, Google and other services as well as password manager applications such as Dashlane and KeePass .
The same flow is also adopted in the browser. When logging in to a Web application that realizes various functions on a browser, it is necessary to enter a password in many cases, but there is always a risk of security. The authentication technology " WebAuthn " to avoid this problem makes it possible to log in to the site and execute settlement without depending on the password. WebAuthn is already supported in browsers such as Chrome, Firefox, Edge.
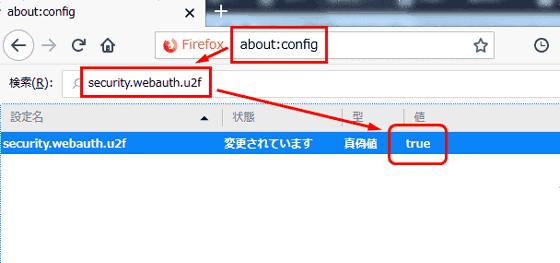
In most cases this feature is disabled by default. For example, for Firefox, enter "about: config" in the address bar, open the page, select "security.webauth.u2f" from the list, double click on the displayed item and change the value to "true" By doing so, you can activate it.
In the case of a password that records or memorizes all passwords and inputs by hand, there is a tendency to use the same password by all means, and once the password leaks from some site, login information to other services It may also run out. Two-step authentication and U2F technology are expected to avoid such problems.
Related Posts:
in Hardware, Security, Web Application, Posted by darkhorse_log