EFF points out the problem of 'Project Verify' that manages accounts with terminal information rather than passwords

by TheDigitalArtist
Four major US telecommunications carriers announced a service to manage accounts with terminal information such as "phone number", "IP address", "SIM card information", not a password. The Electronic Frontier Foundation (EFF) points out the problem as this " Project Verify " is a "bad idea".
The Devil Is in The Details Of Project Verify's Goal To Eliminate Passwords | Electronic Frontier Foundation
https://www.eff.org/deeplinks/2018/10/project-verify
Four major companies in the US, AT & T , Sprint , T-Mobile , and Verizon , were reported to have joined the project called "Project Verify". Project Verify eliminates "passwords" when users perform applications and services. In place of passwords, phone numbers, SIM card information, IP addresses, etc., as well as authentication using SMS and security token We will do.
Details of Project Verify can be seen from the following movie.
Introducing Project Verify - YouTube
Modern smartphone users have an average of 92 passwords, and it is difficult to get everything in mind. Also, despite having to trust the security of various web services and applications, 81% of data leakage is caused by "password theft".
Therefore, Project Verify was created as one solution to the "problem caused by passwords".

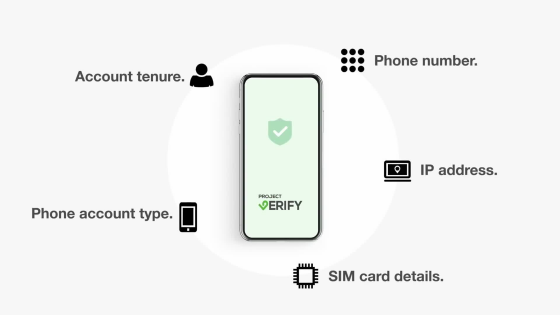
Project Verify authenticates with "multifactor ID" consisting of multiple elements such as phone number, IP address, SIM card information, mobile phone account type, and retention period of account.

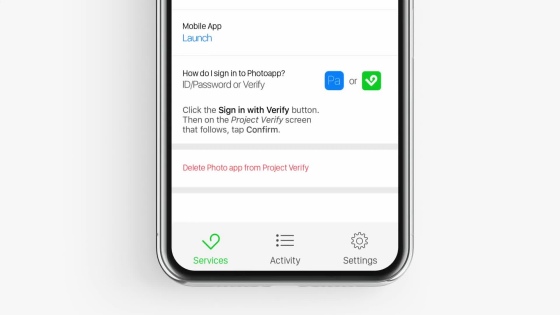
Easy to use. First, download Project Verify.
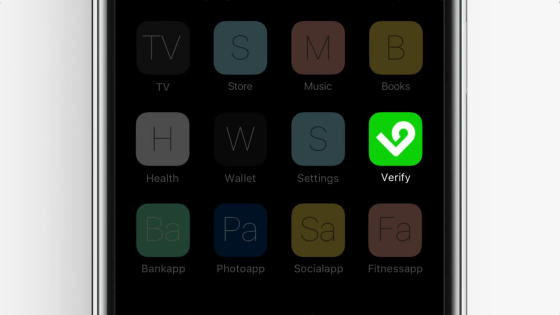
When I start the photo editing application with Project Verify now available ......
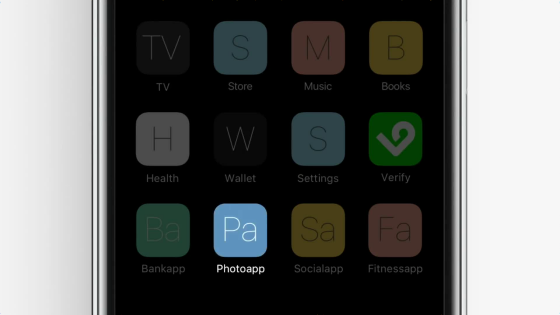
As shown below, a button labeled "Project Verify" is displayed below the box for entering an account password.
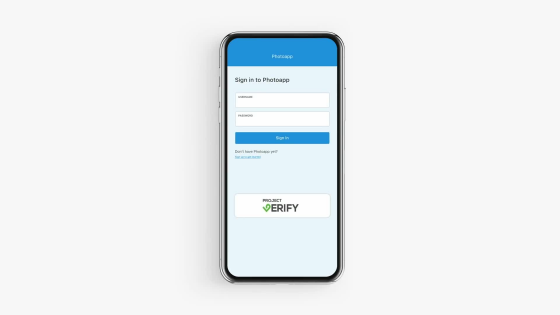
Just press this button without entering an account or password ... ...

Login completed.
Since Project Verify is multifactor authentication , it is a point of security high security.
Even in the case of sending an authentication code to a designated e-mail address ......
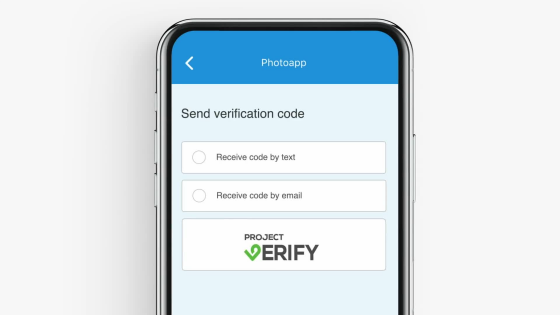
With Project Verify, you can save time and make authentication with a single button.
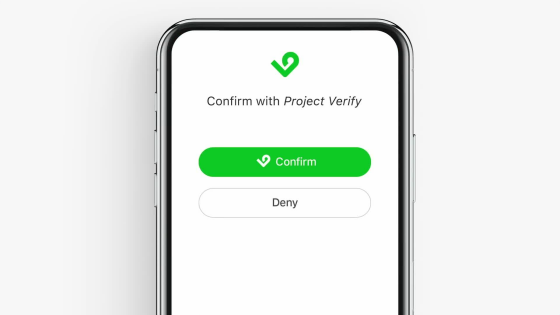
In addition, Project Verify has the control right of the user, it is possible to set each application that you want to use Project Verify and which you do not want to use. Three points of "simple", "safe", and "controllable" are features of Project Verify.
As in movies, account information often leaks out of passwords , and EFF recommends generating and managing strong passwords with password manager . In recent years there are also many services that offer a single sign-on (SSO) method, some people may have seen the button "Log in with Facebook account" and "Log in with Google Account". Although there is a possibility that this SSO system becomes a pitfall and information leaks out, basically SSO is considered to reduce security risk.
Project Verify seems to be the same as SSO in that "you register account with one service once, you can use the account and password you registered for other services". However, EFF is worried about using two of the multifactor authentication performed by Project Verify, "phone number" and "IP address".
In recent years, by linking accounts and phone numbers, problems tend to occur. One method of fraud is the attacker telling the provider the phone number and name of the target and resetting the terminal is also increasing due to "I lost the phone" or "I lost the SIM". At this time, if the provider gives the new SIM card to the attacker and invalidates the target SIM card, the attacker will be able to take over the account by using SMS based multi-factor authentication etc.
In addition, there is a possibility that problems with authentication using a telephone number may occur when simply losing a phone call or when an employee is using an application at work. If the phone number leaks, fraud / harassment / possibility of further hacking also occurs.

by geralt
Also, if an IP address is used for authentication, even if you use VPN or Tor , you will be releasing the IP address to the operator or website operator. In order for Project Verify to work, whichever user is using VPN, Tor, or local Wi-Fi network, the carrier will be involved in logging in to the application or website. As ISPs, including the four telecommunications carriers, track and sell user data, EFF said it is dangerous for users to log in to the network or log off information from the network .
In addition, Project Verify says "The platform shares data only when consumers agree", but it is not certain how this "consent" is required.
Despite the word "Verify" being used, details of Project Verify can not be confirmed at the time of article creation. It is worth seeking "an authentication method that is safer and easier to use than a password" itself. However, it should not be missed that telecommunications carriers that join Project Verify are companies responsible for hacking damage such as SIM swap . EFF said that it is "a bad idea in terms of what history suggests," to leave the gatekeeper of such identity authentication to telecommunications carriers who have been placing a lot of failures on privacy in the past.
Related Posts: