What is 'Credential Stuffing Attack' that automatically unauthorized access using leaked account information?

by Markus Spiske
Credential Stuffing Attack is a cyber attack that exploits the frequent occurrence of user account information and attempts to unauthorized access to various services automatically. A list of account information used in such Credential Stuffing attack is found, and it is clear that more than 100 million e-mail address information is leaked from here.
Troy Hunt: The 111 Million Record Pemiblanc Credential Stuffing List
https://www.troyhunt.com/the-111-million-pemiblanc-credential-stuffing-list/
Troy Hunt, who investigated data breach since 2013, cited "a rapid increase in Credential Stuffing attack" as a trend of the data breaching area in recent years. The Credential Stuffing attack is a cyber attack of automatically entering leaked account information and unauthorized access to the account. Mr. Hunt claims that "it is necessary to stop using the password and generate a password with a random character string using the password manager" because using the same ID and password for multiple services increases the damage. doing.
Users can significantly reduce the risk of receiving a Credential Stuffing attack by changing the password used for each service. However, when the service management side tries to cope with the Credential Stuffing attack, it is necessary to judge that "it is not a legitimate account holder for a person who inputs the correct user name and password", so realizing this It is very difficult. The US Federal Trade Commission (FTC) has filed a lawsuit against the operating organization of the targeted service of the Credential Stuffing attack in early 2018, but the affected organization was "FTC Although we can understand the message, if the customer data is compromised by the Credential Stuffing attack, the innocent company that was sacrificed has no defense measures by law "and we can not do anything for themselves We emphasize the situation.
From this background, Mr. Hunt has created a service called "Have I Been Pwned: Pwned Passwords". This is a service that allows web site operators to search for "passwords that have been infringed" in order to block the use of passwords that have been infringed.
"Pwned Passwords" that you can check whether your password is dangerous in the past leaked data for free - GIGAZINE
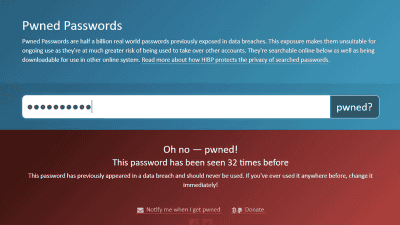
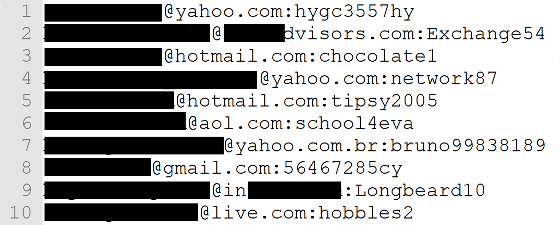
Mr. Hunt continuing such activity reported that it found a list for Credential Stuffing attack named "Pemiblanc" on July 10, 2018, and it includes 11 million cases It seems that it contains mail address information etc of.
In the list named Pemiblanc I found that the e-mail address and password are entered in a set as follows. According to Mr. Hunt, most of the account information recorded in Pemiblanc seems to be saved in the "USA" folder, so it is considered to be account information of a user living in the US.
In Have I Been Pwned operated by Mr. Hunt, more than 1 billion account information leaked due to data breach that occurred in the past is stored. However, the list of Pemiblanc found this time includes at least 6.8 million mail address information not stored in Have I Been Pwned, and data infringement which has not yet been confirmed is considerable It is suggested that it may happen on the scale of.
Mr. Hunt says, "It is unknown which account information leaked from which site," and it is presumed that Pemiblanc was created from multiple data breaches. And we recommend using a password manager to counter something like Credential Stuffing attack.
Related Posts:
in Security, Posted by logu_ii







