More than 100GB of data, including more than 25 million Facebook and Yahoo passwords, was found to be traded on the darknet

Troy Hunt: Inside the Massive Naz.API Credential Stuffing List
https://www.troyhunt.com/inside-the-massive-naz-api-credential-stuffing-list/

Researcher uncovers one of the biggest password dumps in recent history | Ars Technica
According to Mr. Hunt, the data discovered on the dark web site amounted to 319 files, totaling 104 GB. The data includes 70,840,771 email addresses and over 25 million passwords, and 427,308 users registered with 'Have I Been Pwned?' were affected. It turns out that In addition, since approximately 35% of the email addresses in 'Have I Been Pwned?' have not been confirmed to have leaked personal information, it is clear that this is not a reuse of previously leaked data.

Mr. Hunt also highlighted some of the personal information that was leaked, showing that login information for Facebook, Roblox, Coinbase, Yammer, Yahoo, etc. was leaked.
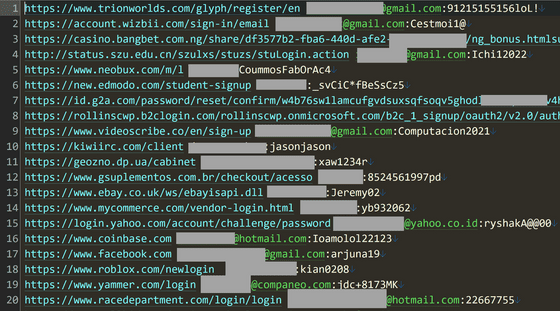
This personal information is said to have been leaked by ``malware that uploads all usernames and passwords entered on the login page'' that infiltrated the victim's device, and the passwords being traded are in ``plaintext'' without encryption. It is said that it was displayed.
Mr. Hunt also points out, ``Most of the passwords that have been leaked and made public are one-of-a-kind passwords that are easy targets for ``

Furthermore, ``The risk of data leakage increases when the same password is used for multiple services, or when a completely different person uses the same password.For example, the name of the pet dog, the birth date, etc. 2018 has less variation than humans, making them easier targets,” Hunt noted.
According to this dark web site, a large-scale dataset called ``Naz.API'' that was previously distributed on another site is used to obtain personal information. Mr. Hunt also claims that ``the majority of the credential information being traded is due to a ``credential stuffing attack ,'' which is a type of ``account hijacking attack'' that collects a large amount of account credential information that has been leaked in the past.'' doing.
Ars Technica, an overseas media outlet, recommends that to properly protect your account, ``Use a randomly generated password or passphrase,'' ``Do not enter your password on phishing sites,'' and ``Use two-factor authentication or security keys whenever possible.'' ” recommends “Use Passkey , the passwordless sign-in standard.”
Related Posts:
in Security, Posted by log1r_ut