Security researchers point out that there is a flaw that could leak personal information in the carrier's SIM card exchange process

by
The one-time password method using SMS or telephone, which is widely adopted as a method for authenticating accounts with web services such as SNS and EC, is a convenient authentication method that can authenticate accounts only by phone number. However, security researchers pointed out that using a prepaid SIM card phone number provided by a major US telecommunications carrier could easily break through authentication, including Kevin Lee of Princeton University. I am.
An Empirical Study of Wireless Carrier Authentication for SIM Swaps
(PDF) https://www.issms2fasecure.com/assets/sim_swaps-01-10-2020.pdf
Is SMS 2FA Secure?
https://www.issms2fasecure.com/
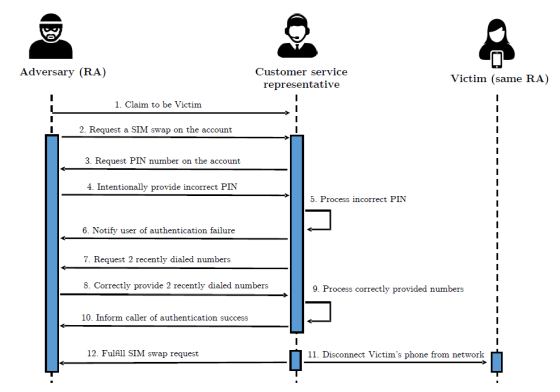
When losing a prepaid SIM card or changing the size of the SIM card in the United States, it is common to use `` SIM swap '' which activates a new SIM card and disables the old SIM card . The flaw was discovered this time at the operation of the customer service center (CSR) of the telecommunications carrier that performed this SIM swap. If the attacker exchanges the SIM card without the original contractor's permission, it is possible to easily take over the phone number, and there is a risk that the one-time password authentication by phone or SMS can be easily broken through .
The survey on SIM swaps covers AT & T , T-Mobile , TracFone , US Mobile and Verizon , the major carriers that offer prepaid SIM cards in the United States. Lee and his colleagues set up multiple accounts and requested a carrier's CSR for a SIM swap, and the CSRs verified that the account authentication method was flawed.
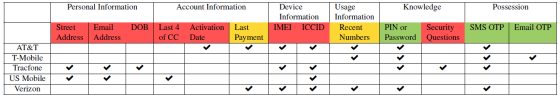
The survey found that all carriers offered insecure authentication methods using information that could be known by others. Communication carriers whose red and yellow items use an authentication method that can avoid authentication even if they are not themselves. For example, when authenticating with the 'last phone number', if the attacker knows only the take-over phone number, the attacker calls the take-up phone number, requests a return phone call, and identifies the last call destination. Can be changed on purpose.
Also, according to
It is necessary for the communication carrier to cancel the insecure authentication method when performing the SIM swap, and the website prepares an additional secure authentication method other than the authentication method using telephone or SMS, or the authentication itself by telephone or SMS Lee and his colleagues say they should stop.
Related Posts:
in Smartphone, Security, Posted by darkhorse_log