T-Mobile turned out to be damaged by cybercrime such as `` SIM swap '' that hijacks smartphones more than 100 times in 2022

Hackers Claim They Breached T-Mobile More Than 100 Times in 2022 – Krebs on Security
https://krebsonsecurity.com/2023/02/hackers-claim-they-breached-t-mobile-more-than-100-times-in-2022/
According to data released by Brian Krebs of KrebsOnSecurity, which conducts security-related research and information dissemination, three criminal groups used T-Mobile employees to access internal tools, and from that access smartphones were temporarily It has been suggested that they are conducting attacks that create controlled cybercriminal targets. In particular, by identifying personal information from the user's own information or leaked information, and impersonating the user, the mobile phone company is contacted and all the information in the smartphone is sent to the fake SIM card. It is analyzed that cybercriminals are working on 'SIM swap'.
According to data from KrebsOnSecurity, a total of 104 “SIM replacement claims” were made to T-Mobile by hacker groups across all groups in the seven months from May to December 2022. . All three groups of SIM swappers discovered by KrebsOnSecurity are known to remain active in 2023. SIM swap related scams have been observed with providers other than T-Mobile, but much less frequently than with T-Mobile. However, if the SIM swap to another provider is successful, it seems that a fairly high bill tends to be made.

KrebsOnSecurity shared the collected data with T-Mobile, but T-Mobile neither confirmed nor denied the cybercrime allegations in the data, saying in a statement, 'This type of activity affects the wireless industry as a whole. We are constantly working to combat it, and we are doing everything we can to prevent unauthorized access, including stronger multi-factor authentication controls, stronger authentication environments, and restricted access to data, apps, and services. 'We have continued to drive improvements in our ability to protect, and we are also focused on collecting threat intelligence data, such as the one shared, to further strengthen these ongoing efforts.'
According to Alison Nixon, chief research officer at
According to KrebsOnSecurity, despite T-Mobile's security exposure, T-Mobile's security team has been effective, with one cybercriminal group saying, 'T-Mobile's security team started monitoring their chats. Isn't it?' he said that he doubted. The following image shown by KrebsOnSecurity is a calendar for 2022 that shows the days when SIM swap warnings were confirmed in red, but you can see that the number of damages has decreased as the year progresses.
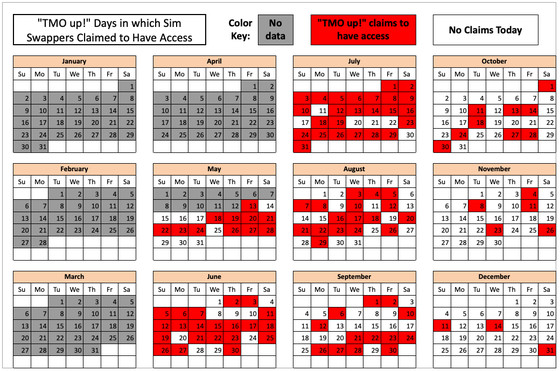
T-Mobile has not responded to questions about what it is doing to strengthen employee authentication, but Nicholas Nicholas, a researcher and lecturer at the International Computer Science Institute at the University of California, Berkeley, said: ``T-Mobile and all major wireless providers must require employees to use a physical security key as a second factor when logging into company resources,'' Weber said. I'm here. 'The biggest reason this problem has gotten out of hand is that these criminal groups are recruiting teenagers to do their dirty work, and children play a very important role,' Nixon said. Because even if minors are arrested for SIM swapping, they are quickly released due to legal protection and tend to repeat the same crimes,” he argues.
Related Posts:
in Security, Posted by log1e_dh







