It turns out that the international hacker group 'LAPSUS $' centered on teenagers stole the source code of communication giant T-Mobile

The international hacker group ' LAPSUS $ ', which has been attracting attention for hacking
Leaked Chats Show LAPSUS $ Stole T-Mobile Source Code – Krebs on Security
https://krebsonsecurity.com/2022/04/leaked-chats-show-lapsus-stole-t-mobile-source-code/
T-Mobile confirms Lapsus $ hackers breached internal systems
https://www.bleepingcomputer.com/news/security/t-mobile-confirms-lapsus-hackers-breached-internal-systems/
Lapsus $ hackers breached T-Mobile's systems and stole its source code --The Verge
https://www.theverge.com/2022/4/23/23038570/lapsus-hackers-target-t-mobile-source-code-multiple-breaches-cybersecurity
LAPSUS $ is a group of hackers who have been active mainly in South America since around 2020, and from around 2022, they have switched their targets to international high-tech companies such as Microsoft and Samsung. The leader is likely to be a 17-year-old boy living in the United Kingdom who works under the IDs 'White', 'White Doxbin' or 'Oklaqq', and in March 2022 the City of London Police was involved in LAPSUS $. It was reported that seven young people aged 16 to 21 were arrested.
Seven young people, including a 16-year-old teenager, are arrested for being associated with the hacker group 'LAPSUS $' that attacked Microsoft and Samsung-GIGAZINE

The security blog Krebs on Security reported on April 22 that he had obtained a copy of 'a private chat exchanged during the week before LAPSUS $ members were arrested.' The chat obtained by Krebs on Security was conducted on a private Telegram channel in which only the seven members who are the core of LAPSUS $ participate.
In the chat in question, the exchange about the ' social engineering ' that LAPSUS $ uses for hacking was also evaded. According to Krebs on Security, LAPSUS $ used it as a stepping stone to gain remote access to compromised devices and credentials from dark sites such as 'Russian Market' to break into the targeted system.
LAPSUS $ used social engineering to perform 'SIM swapping ' to hijack the target SIM card, intercept SMS and voice calls, and break through multi-factor authentication for employee accounts. From the chat, we also know that LAPSUS $ was continuously targeting the major telecommunications carrier T-Mobile to facilitate this SIM swapping.
In addition, leader White has insisted on stealing the T-Mobile source code, and it is clear that he stole the source code by overcoming the complaints raised by other members. Below is a screenshot of evidence White posted in a private chat that an automated script stole more than 30,000 source code repositories from T-Mobile.
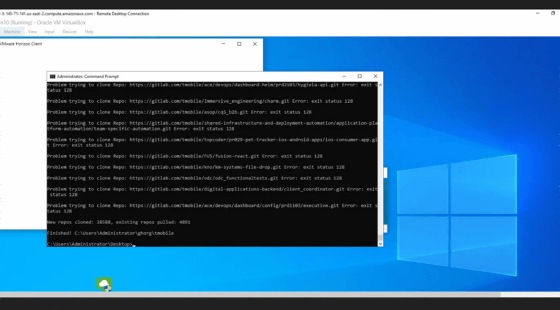
In response to a Krebs on Security inquiry, T-Mobile said, 'Our monitoring tools used stolen credentials to detect malicious actors accessing internal systems that store operational tool software a few weeks ago. I admitted that there was an external hack.
On the other hand, T-Mobile said, 'The accessed system does not contain customer information, government information, or other similar sensitive information, and there is no evidence that an intruder could obtain something of value. Our systems and processes worked as designed, intrusions were quickly shut down and blocked, and leaked credentials used by hackers were invalidated, 'said customer information and other information. Claims to have been.

In addition, Krebs on Security reports from the content of the chat leaked this time that members of LAPSUS $ were not arrested all at once when the City of London Police announced, but were arrested sequentially for several months. ..
In addition, leader White points out that he is acting fairly aggressively against members of LAPSUS $, especially abusive to members codenamed 'Amtrak'. 'White doesn't seem to count Amtrak and other LAPSUS $ members as friends,' said Krebs on Security.
In addition, LAPSUS $ seems to have agreed to store the data stolen by hacking in the cloud instead of personal devices in preparation for the seizure of electronic devices by the police, but access to the AWS server was blocked in late March. It is also stated in the chat that the stolen data was lost due to being done. Amtrak wrote in response to the Federal Bureau of Investigation (FBI) seizure of the server, 'This is illegal! It's full of illegal shit!'
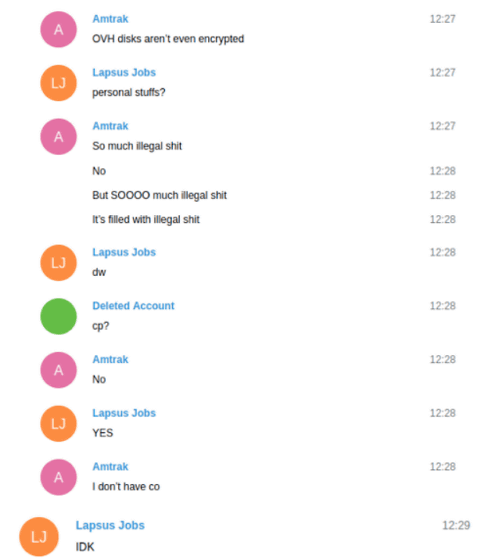
White was obsessed with the T-Mobile source code stored on the confiscated server and tried to hack again, but T-Mobile had revoked the access token used for the hack, so this attempt was made. It seems that it ended in failure.
In addition, T-Mobile, which was revealed to be hacked from LAPSUS $ this time, had previously stolen customer data for 30 million people and paid 200,000 dollars (about 25 million yen) for exclusive access. It is reported that the data continued to be sold in the black market even after purchasing the rights.
It was discovered that 30 million customer data that should have been recovered by paying 25 million yen continued to be sold in the black market --GIGAZINE

Related Posts:
in Security, Posted by log1h_ik






